
 There have been a number of reports this morning highlighting Android’s first trojan app has made it to users handsets, sending SMS messages to premium rate numbers in the background without the owner knowing.
There have been a number of reports this morning highlighting Android’s first trojan app has made it to users handsets, sending SMS messages to premium rate numbers in the background without the owner knowing.
As the messages are sent, the user incurs a large bill whilst the applications developers get a share of the profit.
Anti-virus company Kaspersky Lab, caught wind of the malicious program, classified it as a “Trojan-SMS” and gave it a name: SMS.AndroidOS.FakePlayer.a.
The file works its way onto a users handset disguised as a media player application .APK file that is just 13KB and when installed immediately starts sending out the premium rate SMS messages. Currently, only Russian Android owners can physically lose money by the trojan but users can still be infected regardless of location.
How Vulnerable Am I?
 If you want an honest answer, we don’t know.
If you want an honest answer, we don’t know.
The small matter of how you become infected has been neglected by Kaspersky. It is not clear whether a user can be infected by downloading an app via the Android Market or via a third-party download site. We assume that a user has to download the APK manually and then install it on their Android device, a process that the Android operating system blocks by default.
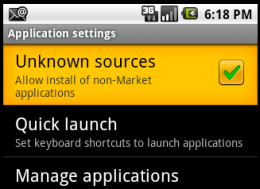
The Android operating system is set to disable the installation of apps from unknown sources, stopping trojans such as FakePlayer from ever gracing your Android handset.
Technical Android owners are more likely to have enabled this option leaving themselves a little more vulnerable than users who leave their Android settings set to factory defaults but Android has another system to stop even those users from mistakenly installing rogue applications.
Whether it’s a Market or non-Market app being installed, Android will always display the permissions that the application requests. Using FakePlayer as an example, you would not expect a media player application to request SMS permissions, meaning you should proceed with caution.
Protecting Yourself
Even though your handset might have the above options selected, you still need to be vigilant when installing applications. If you are keen to avoid untrusted apps, always stick to the Android Market and make sure the Unknown Sources option is unticked in your Application Settings.
Even then, carefully read what permissions each app requests when installing so you can be in complete control of what data is accessed on your device.
Conclusion
We are keen to stress that security should never be taken lightly, appropriate steps should be taken whenever you install an app, whether it be from the Android Market or otherwise.
With so many tech outlets stressing that this trojan is a blow for Google and its OS, we wanted to show that Android holds its own when it comes to security, visually prompting the user as to what resources installed apps will try to access and blocking third-party apps by default. This is a complete contrast to the JailbreakMe PDF exploit which can affect any iPhone or iPad device regardless of security settings.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





