A new trojan for Android has been discovered that resides in the memory of infected devices and launches itself early on in the OS loading stage. Even if some elements of the threat are removed successfully, at least one component will still reside in the protected memory area and will reinstall the malware after a reboot and, thus, re-infect the system.
The threat, detected as “Android.Oldboot.1” by Russian security firm Doctor Web, is believed to be the first bootkit for Android according to the company. A bootkit, for those who don’t know, is a kernel-mode rootkit variant that can infect startup code in order to attack even attack full disk encryption systems as well as minimize the possibility that it will be deleted without tampering with the device’s file system.
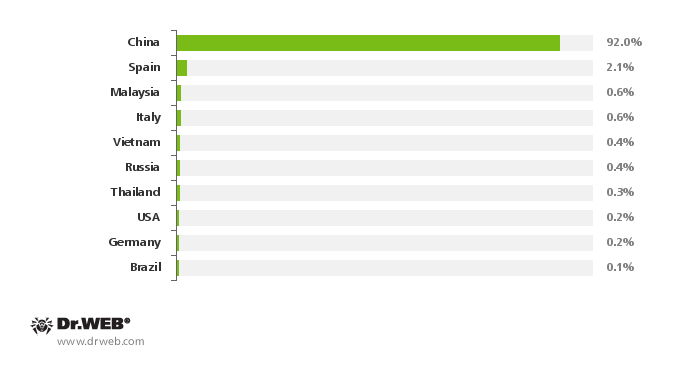
The malware has reportedly been detected on more than 350,000 mobile devices around the world, including Spain, Italy, Germany, Russia, Brazil, the US and some Southeast Asian countries. 92 percent of the compromised devices are, however, located in China:
This is key to understanding that this threat doesn’t spread by simply browsing the Web, opening attachments, or even sideloading suspicious apps. The malware either ships with the device in question or is manually deployed by someone with physical access to an Android phone or tablet.
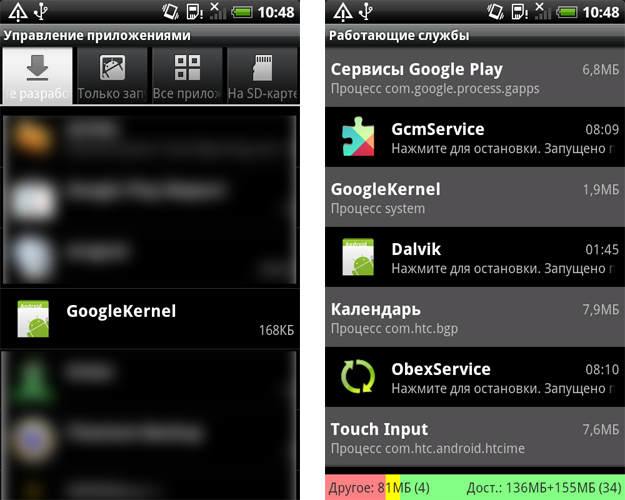
Doctor Web explains a device is first infected by placing one of trojan’s components into the boot partition of the file system and by modifying the init script responsible for the initialisation of OS components. When the device is turned on, the modified script loads the code responsible for the trojan’s Linux-library imei_chk, which extracts the files libgooglekernel.so and GoogleKernel.apk, placing them in /system/lib and /system/app, respectively.
Thus, part of the Trojan Android.Oldboot is installed as a typical application which further functions as a system service and uses the libgooglekernel.so library to connect to a remote server and receive various commands, most notably, to download, install or remove certain applications. Reflashing a device with modified firmware that contains the routines required for the trojan’s operation is the most likely way this threat is introduced, according to Doctor Web.
The good news is that your device is unlikely to be infected with Android.Oldboot.1 unless you have purchased a dubious product from a Chinese manufacturer. On the flipside, this sets a dangerous precedent for Android malware that is very difficult to remove.
See also – Android malware emerges on Google Play which installs a trojan on your PC, uses your microphone to record you and Sophos declares 2012 the year of Android and Mac malware, as cybercriminals look beyond Windows
Top Image Credit: Flavio Takemoto
Get the TNW newsletter
Get the most important tech news in your inbox each week.