Pokémon Go launched back in July, but it was only available to download in a handful of countries. Most people desperately want what they can’t have, so those in unsupported regions flocked to shady third-party file sharing websites to install what they believed to be a final build of the game.
Little did they know, however, that they were actually infecting their device with a nasty piece of malware that allowed prying eyes to monitor their every keystroke. In some cases, the savviest hackers were even able to take full control of their victim’s phone.
It didn’t take long for these malware-filled versions of the title to become a thing of the past, though, as Pokémon Go started landing in additional countries at a relatively fast pace. Unfortunately, the malicious code is back again, but this time it’s hidden in applications related to the game.
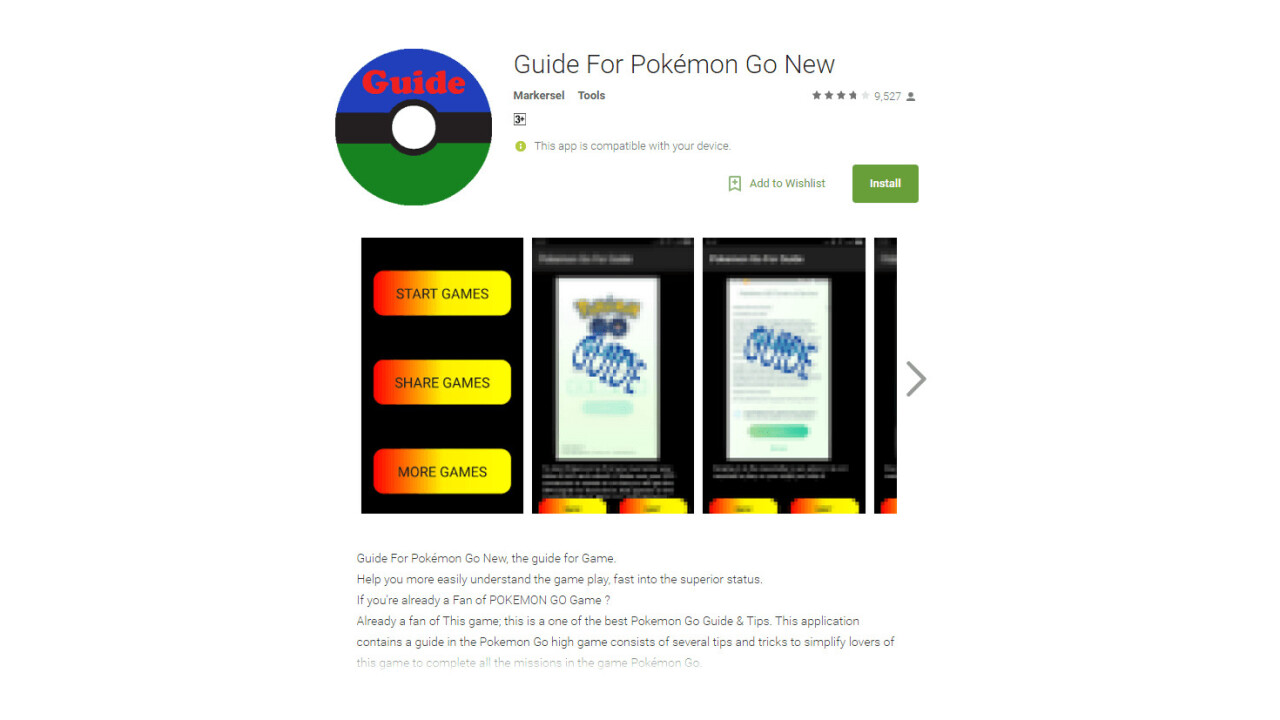
Computer security giant Kaspersky Lab first noticed this emerging trend and has pinpointed its most successful example — an Android app operating under the name ‘Guide for Pokémon GO’. Downloaded by over half a million people, it contains a string that displays ads and grants hackers root access to the Android OS.
As luck would have it, the code isn’t activated immediately. Instead, it’s thought to have only infected around 6,000 handsets, and not all 500,000 devices the application was installed on.
If you’ve downloaded Guide for Pokémon Go, or similar, you’re at risk of infection. To see if yours is one of the 6,000 plus units exposed to the malware, check out Kaspersky’s free scanning software.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




