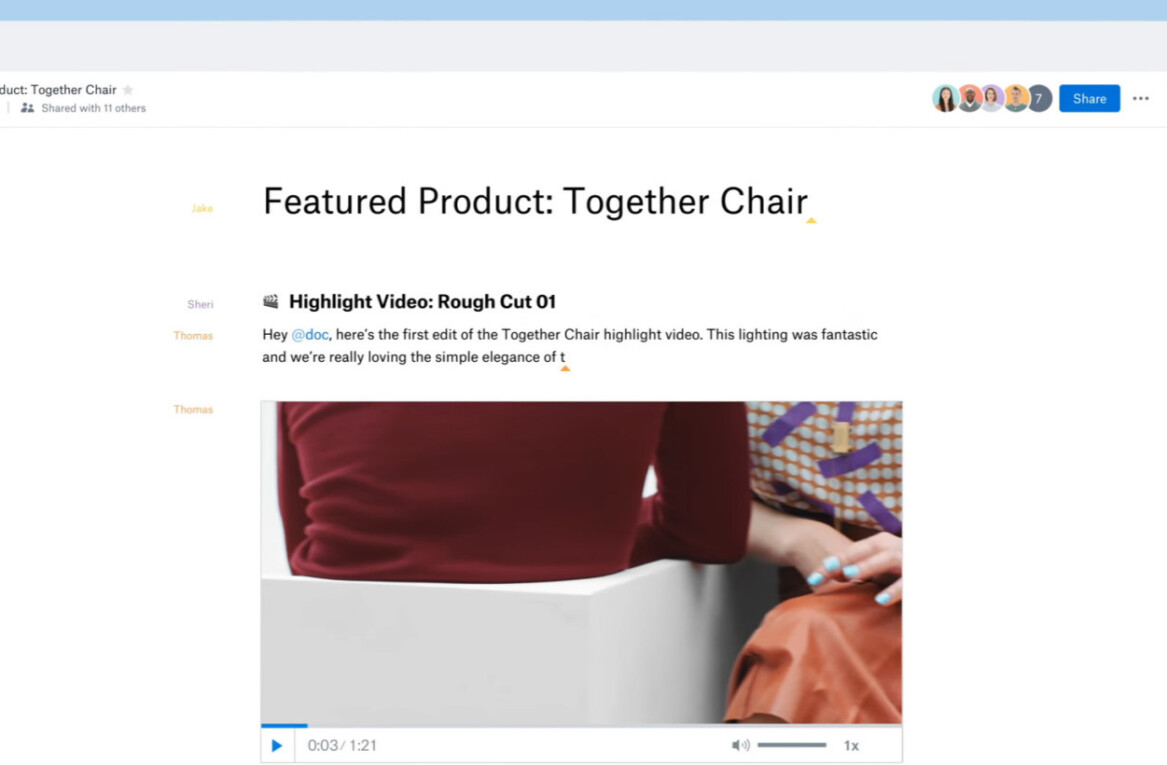
Dropbox has made a change to its feature that lets users share links to their documents, after it revealed a vulnerability that could give third-parties access to data on its severs.
A company post disclosed a weakness with referer headers that could expose information in the following scenario:
A Dropbox user shares a link to a document that contains a hyperlink to a third-party website.
The user, or an authorized recipient of the link, clicks on a hyperlink in the document.
At that point, the referer header discloses the original shared link to the third-party website.
Someone with access to that header, such as the webmaster of the third-party website, could then access the link to the shared document.
Dropbox says it isn’t aware of any information that has been compromised due to this hole. To mitigate any potential risk, it has completely disabled the ability to share links to existing documents that include hyperlinks. It expects to have the feature back up and running up again “over the next few days.”
Meanwhile, Dropbox says that document sharing works fine for all other files, which are free of the vulnerability.
Security expert Graham Cluley points out that the issue can also affect Box users. He warns users of cloud storage services to keep all shared links private (and particularly away from search engines) to avoid making private information available to third parties.
Image via Ian Lamont / Flickr
Get the TNW newsletter
Get the most important tech news in your inbox each week.