DNS. It’s a tricky piece of Internet technology and a a couple of years ago a group had released some malware that was sending people to the wrong websites, attempting to use phishing schemes in order to profit. The FBI tracked the group and eventually shut it down, but millions were still affected. To ease the pain, the FBI set up its own DNS servers, but in July of this year those servers are being shut down.
So what’s an infected person to do? Fortunately there’s a site for the DNSChanger Working Group that will let someone know if they’ve been using the FBI’s DNS servers, but those who are infected are the least likely ones to realize it, much less to know how to fix the problem. So how does the DNSWG get its word out to more people? They turn to CloudFlare.
Starting today, if you have a site running on CloudFlare, you can enable a simple app that will alert a visitor that they are running on the government’s DNS servers, possibly with an infected computer:
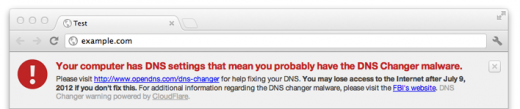
That’s pretty huge, considering the reach of CloudFlare, but the team wanted to go even further. So other site owners can now implement the same warning splash by simply taking CloudFlare’s code from Github.
You’ll notice that the link from CloudFlare is pointing users to OpenDNS in order to give them a good solution to their infection problems. OpenDNS went to work in assembling all of the information that someone would need in order to find out what the problem is and how to fix it.
According to CloudFlare’s Matthew Prince, the two companies should see around 60% of the world’s affected machines over the course of the next month. While that still leaves 40% untouched by their hands, it’s a great start to solving a big problem. When the FBI shuts off its servers on July 9th, hundreds of thousands of people are set to have no Internet service.
More? Click here to see how CloudFlare is hoping to help fix our broken Internet.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





