Cybercriminals have managed to alter the DNS records of some Go Daddy hosted websites. As a result, users visiting these pages are being infected with ransomware.
For the uninitiated, ransomware is a very profitable type of threat which restricts access to the computer it infects, spamming the user with prompts that demand a ransom paid for functionality to be reinstated. Access is limited either by encryption or locking the system.
The attackers in this case are accessing and modifying the DNS records of sites, adding one or more additional subdomains with corresponding DNS entries referencing malicious IP addresses, ensuring they resolve to rogue servers with the Cool Exploit Kit. As a result, the attacks appear to use legitimate-looking URLs, helping evade security checks as well as tricking users into thinking the content must be safe.
Instead, the users are hit with various malicious files, since the exploit kit takes advantage of several different vulnerabilities and can serve up different types of malware, mainly ransomware according to Sophos:
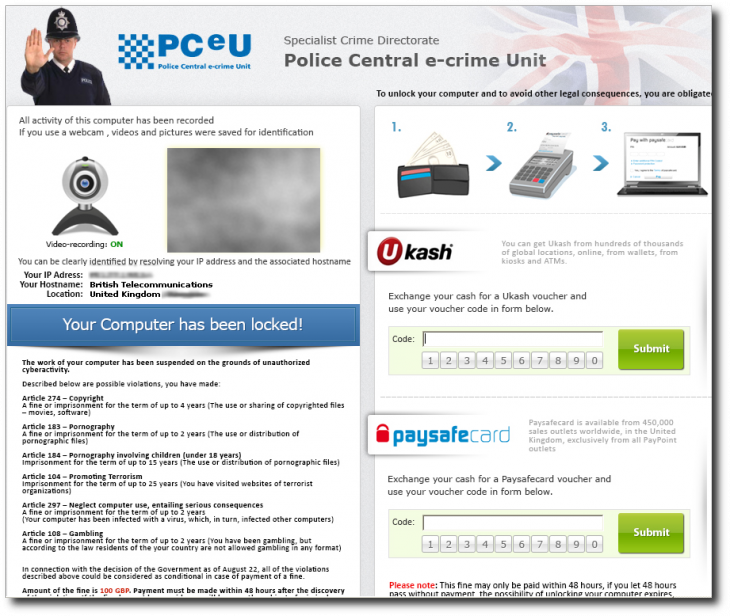
Recent ransomware variants use law enforcement imagery to make it look as if the warnings are legitimate. Many even leverage geo-location services, like the one in this case, to determine the location of the infected computer in order to display a message appropriate to that country. Sophos detects the threats as Mal/ExpJS-AV, Troj/DexFont-A, and Mal/JavaGen-E.
The above is a British example, but again the warning pages vary depending on where you are in the world. Those infected are told they have viewed or downloaded copyrighted or illegal material and must pay a fine (in the above case, 100 British pounds) in order to have their computer restored. If not, they are told they will be arrested.
In all cases, never pay the ransom. If you don’t know how, have a friend clean out your computer.
Sophos isn’t sure how the attackers were able to access the Go Daddy DNS records, but the security firm speculates that they may have used compromised user credentials (stolen or weak passwords). Unfortunately, webmasters are unable to check their historical login activity to verify this theory, and Go Daddy is refusing to release such information.
We have contacted Go Daddy about this issue. We will update this article if and when we hear back.
Update on November 26: Go Daddy blames phishing (not security hole) for some sites pushing malware, resets passwords
See also – Ransomware uses Anonymous name to extort money: Your files are encrypted, pay up to get them back and Warning: Skype users attacked by ‘lol is this your new profile pic?’ ransomware and click fraud
Image credit: Paul Joseph
Get the TNW newsletter
Get the most important tech news in your inbox each week.