
We’ve seen cryptocurrency hungry hackers hiding mining malware in Adobe Flash updates, and even in legitimate Windows updates, but now hackers are hiding it in cracked audio production software.
Security researchers at ESET have uncovered a Monero cryptocurrency mining bot called LoudMiner. Hackers have been distributing it since August 2018, but in the past month has begun to surface in pirated versions of VST (Visual Studio Technology).
Indeed, hiding malware in pirated software is nothing new. One always dances with the devil when downloading bootleg programs, but LoudMiner is unique in that it’s cross-platform, affecting both MacOS and Windows users.
LoudMiner in unique in that it runs on a Tiny Core Linux virtual machine, meaning it can run on both operating systems.
Researchers believe hackers used VST software because it’s highly likely that it will be installed on a computer with a high-end CPU. What’s more, given VST software uses lots of CPU resources, the miner stands a chance of going unnoticed.
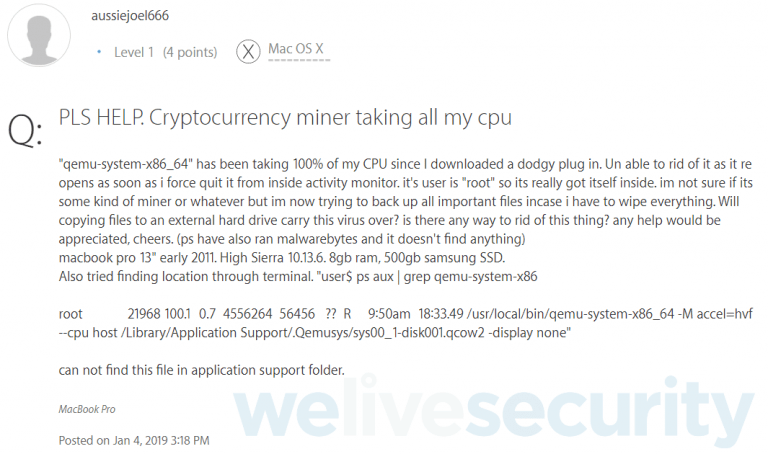
Unfortunately for hackers, though, some individuals recognized that their systems began to display suspicious activity after downloading a “dodgy plugin.”
The researchers found at least four versions of LoudMiner, which is itself an XMRig Monero cryptocurrency miner. It’s unclear if hackers were able to earn any cryptocurrency through this attack.
It installs itself at the root level, in a virtual Linux environment, programmed to load every time the user reboots their system. One victim reported having to reinstall MacOS to get rid of the bug.
As you might expect, ESET researchers recommend not installing pirated software as a first line of defense against this kind of attack. And obviously, we agree, we would never recommend you download torrents.
Researchers also recommend keeping an eye on CPU useage, and watching out for new processes added to your OS’ list of startup programs.
If you want to know the real techy details about how LoudMiner works, you can read ESET’s full report here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





