
Security researchers have uncovered a knock-off cryptocurrency trading website designed to steal the funds of unwitting victims.
Cybercriminals have created a website that imitates the Cryptohopper cryptocurrency trading platform to distribute malware that could steal personal information, hijack your clipboard, and crypto-jack your system, Bleeping Computer reports. It appears to have helped hackers amass a trove of over $260,000 in various cryptocurrencies.
When users visit the imitation Cryptohopper website, their system will automatically download and execute a file simply called Setup.exe. While on the surface it might appear legitimate, it’s actually a Trojan.
On execution, the Trojan installs two further viruses: one acts as a cryptocurrency miner, and the other, as a clipboard hijacker. This kind of attack helps hackers earn digital coins from the mining, whilst also potentially stealing passwords, addresses, usernames, and other sensitive information that people might copy to their clipboard.
According to researchers, the malware attempts to steal browser cookies, payment information, login credentials, cryptocurrency wallets, auto fill data, and two-factor authentication data.
The clipboard hijacker component appears to have given the attackers some success already, though.
When a user copies a cryptocurrency wallet address to their clipboard, the hijacker will replace the address with one belonging to a wallet in their control. As such, any funds are directed to the attackers and not to the intended recipient.
That said, researchers are unable to say exactly how much has been earned from this particular campaign on its own, but have identified wallets associated with the attackers which hold a sizable amount of cryptocurrencies.
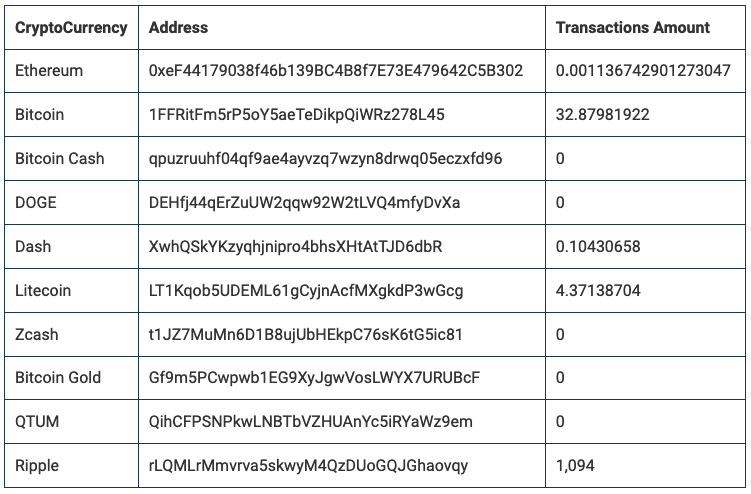
By the looks of things, the attackers have purloined over $260,000 in assorted cryptocurrencies from their exploits. The majority of which has been obtained through redirected Bitcoin payments, earning them over $257,000. How much of this has been earned through hijacking clipboards, is difficult to say.
Hiding cryptocurrency stealing viruses inside seemingly legitimate sources is nothing new sadly.
Last year, malware distributors hid cryptocurrency mining malware in Adobe Flash updates to hide malicious files. Hackers employed a similar tactic where they hid malware in legitimate Windows installation files.
Always be sure you’re updating your system with files from legitimate sources. And in this case, it can’t hurt to double-check cryptocurrency wallet addresses after you paste them from your clipboard.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




