
Analysts have reportedly discovered the source of the sextortion emails that’ve plagued the internet since last year — the ones that demand Bitcoin or else they’ll leak videos of you masturbating to kinky pornography.
Reason Cybersecurity researchers dubbed the malware Save Yourself, as recipients typically receive the bogus emails from senders like “SaveYourself@856.com.”
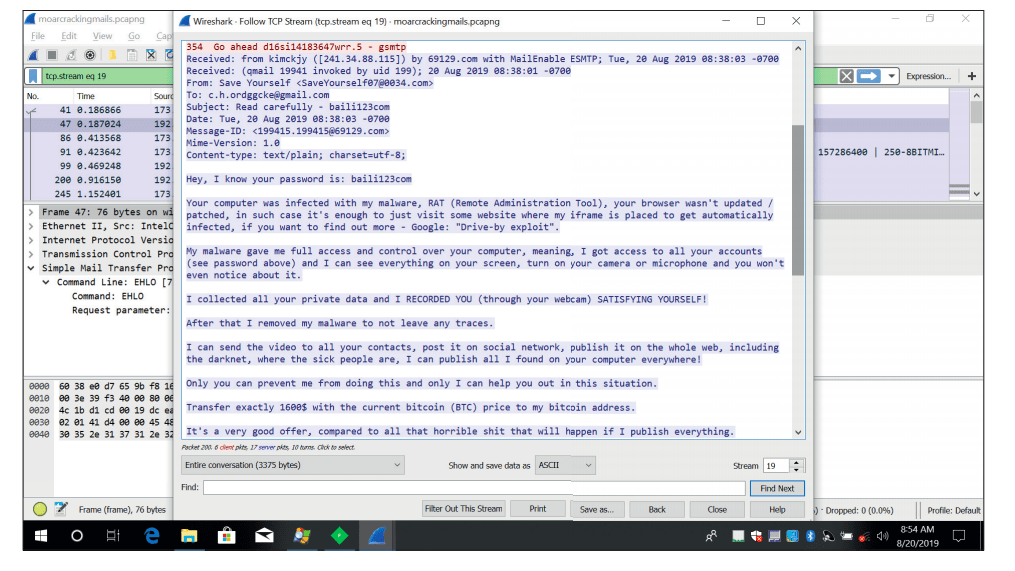
The emails state that dangerous malware has infected the recipient’s machine, but Reason found this isn’t the case.
Instead, the firm discovered the malware forcing devices to act as blackmail proxies is also secretly mining privacy-focused cryptocurrency Monero, with all funds generated going directly the attackers.
Save Yourself cleaners are spreading more malware
The firm was clear to point out that receiving the Bitcoin sextortion email doesn’t automatically mean infection, just that the recipient’s email address has been exposed in a password dump.
Researchers ironically found, however, that many sites offering products to supposedly remove the Save Yourself malware were actually peddling malware.
“It is very possible that the malware author has gathered and combined several viruses and modified them to suit their own needs,” said Reason.
To date, analysts found more than 110,000 users have been infected with the Save Yourself malware.
Save Yourself can also steal your Bitcoin
Reason reported that the malware is designed to remain under the user’s radar. In particular, Save Yourself only uses 50 percent of the infected machine’s CPU to mine Monero, so as not to raise suspicion.
The malware can also reportedly read clipboard data and replace Bitcoin wallet addresses with its own, presumably to redirect cryptocurrency transactions to the attackers.
Save Yourself is also said to compromise any executable found on the target machine to ensure automatic infection any time the user runs such files.
“The desired executable will then run as it should, so the user won’t suspect that there’s anything wrong,” said Reason. “Nor will anything look suspicious when analysing the sample since – at first glance, it will look like known software (icon, signature, strings, functionality).”
The firm noted that most anti-virus solutions should detect and clear the malware. As well, major email providers are automatically protecting users against the sextortion emails.
Hard Fork previously reported, though, that the attackers are pivoting, now demanding Litecoin instead of Bitcoin so as to dodge email filters.
Want more Hard Fork? Join us in Amsterdam on October 15-17 to discuss blockchain and cryptocurrency with leading experts.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





