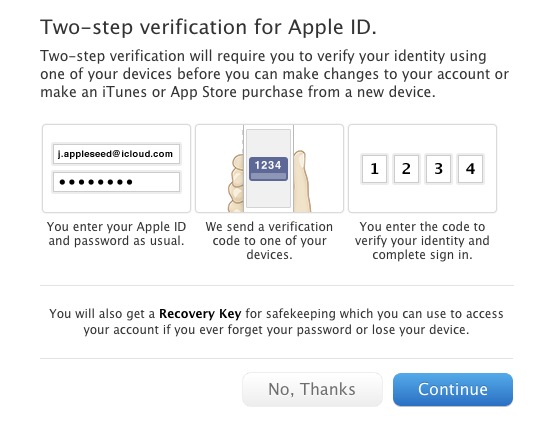
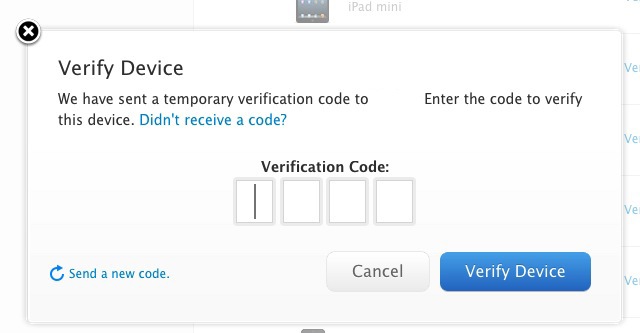
Apple has introduced a two-step verification system for Apple IDs today. This is a system that lets you require verification of your identity when you sign on to a new device. This will theoretically make it more difficult for people to use your Apple ID on devices other than your own, especially to make purchases.
The new system, first noted by 9to5Mac, is relatively simple and resembles those in use at other web companies. You can set up two-step verification by visiting the Apple ID site here. You then enter your password and click on Password and Security. Once you’re there, you’ll have to enter your security questions, click on Two-Step Verification at the top of the page and then you’ll be led through the setup process. Two-step Verification is currently available in the U.S., UK, Australia, Ireland, and New Zealand but Apple says it will be rolling out to other countries.
First, the system is explained to you. It involves entering your Apple ID on a new device and receiving a verification code that you use to confirm your identity via SMS. You’ll also get a master Recovery Key that lets you gain access to your account if you lose your SMS device.
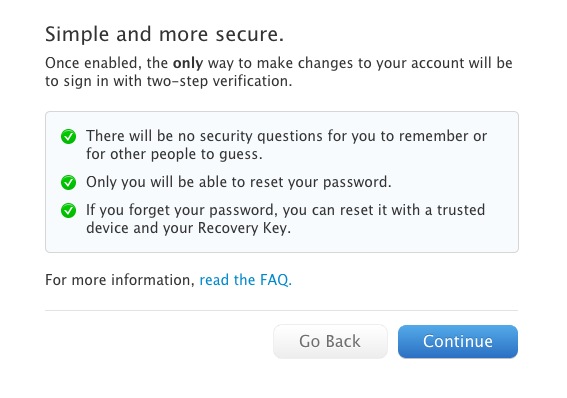
Once you’ve begun the process, Apple notes that you will not have any security questions, only you will be able to reset your password and that you need both a ‘trusted’ (owned) device and your Recovery Key to reset it.
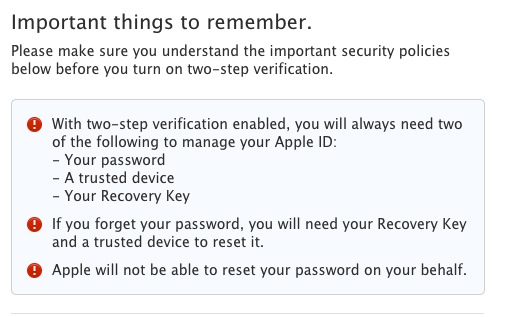
Then, Apple warns you again that in order to manage your account, you will always need two or more of the following: password, trusted device or a recovery key. It also notes that Apple will not be able to reset your password for you. This is a change from the current system, and should be noted with extreme caution, as recovery after you enable two-step verification is very tough if you don’t have those items in hand.
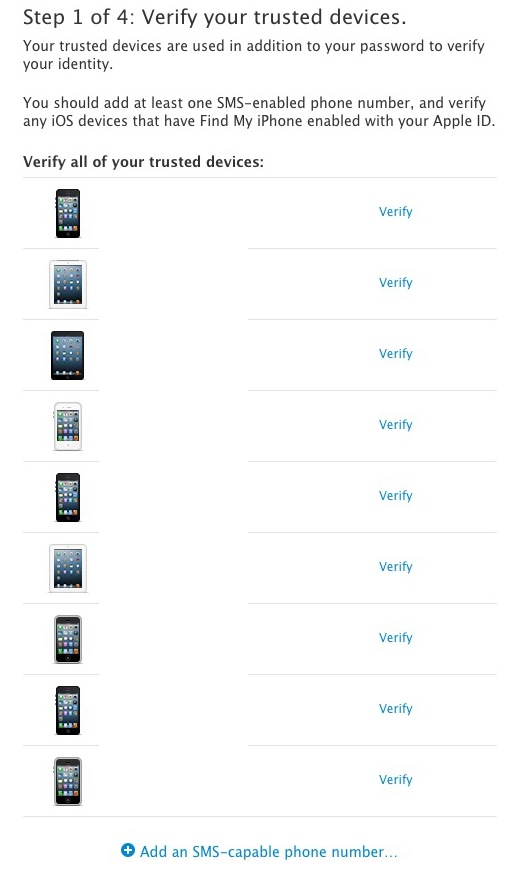
Next, you’re given a list of ‘trusted’ devices that you can use to verify your account. You should choose at least one that has SMS service, like an iPhone, and Apple recommends that you also verify any devices that have Find My iPhone enabled. This is important because it means that you’ll have the ability to track and locate those devices and they’re authorized to reset your password. It also means that you’ll keep track of exactly which devices can wipe your account.
If the device is an iPhone, you’ll actually enter two verification codes when you click verify. One adds the device as a verified option for resetting your password and the other sets up your phone number as the SMS gateway to receive your verification code. You’ll enter two verification codes in the following process.
Once you’ve set up Two-Step verification, you’ll be asked to enter a Verification Code every time you log into your Apple ID on a new, unverified device. You can remove devices from the list when you sell them so that they won’t be able to be used to reset or log in to your account any longer. And yes, you can turn Two-Step verification off if you don’t like it.
You’re also given a printable Recovery Key that you should keep in a safe place, like a safe. Don’t carry it around with you either for goodness sakes. It’s one of the three things that you could need to reset your Apple ID password. Once you’ve printed it, you’ll be asked to re-enter it and then you’ll get a confirmation email. There’s a full FAQ up at Apple’s site if you want to know more about Two-Step Verification.
Two-step verification is a nice addition to the Apple ID security regimen for several reasons. Chief among these is the fact that limiting password resets to those people who have physical access to your device greatly narrows the ability of people to gain entry to your account without your permission. It greatly mitigates the social engineering aspects of hacking when it comes to companies as well. It doesn’t matter how charming a hacker is, they can’t convince Apple to reset your password to one that they like if Apple has no ability to do that.
It’s definitely not a foolproof system and shouldn’t be seen as making an Apple ID ‘hacker proof’, but it’s a good step forward and has been adopted by many companies.
Get the TNW newsletter
Get the most important tech news in your inbox each week.