It’s been a whirlwind few months for LulzSecurity (LulzSec), bursting onto the tech scene with the high-profile hacks of US TV network Fox, moving on to compound Japanese electronics giant Sony, taunting its detractors as they sought to expose row after row of SQL database entries in high-profile government and agency websites.
On Saturday, LulzSec announced on Twitter that after 50 days of “anarchic lulz” it was to cease operations, dropping its largest collection of compromised data in torrent file posted to The Pirate Bay. The 457.84MB download contained information including AOL internal data, AT&T internal data and the “FBI being silly” among its contents.
In 50 days, the group dominated headlines of nearly every print and online news agency across the world, distanced itself from the arrest of Ryan Cleary by the Metropolitan Police and antagonized whoever it could, simply “for the lulz”. With each day, we got to know more about the group; what its motivations were, how it was able to steal so much data and the identities of its members were supposedly revealed on a number of occasions.
With the group now apparently disbanded, here’s a look back at 50 days of LulzSec’s exploits.
X-Factor, Fox and PBS
On May 7, LulzSecurity emerged on Twitter, registering the @LulzSec username. Posting its first tweet, the group detailed the compromise of Fox.com with the message:
“FOX.COM HACKED! # MySQL version: (5.1.47-log) running on 10.96.57.102 (www.fox.com) #Fox #hacked –> #XFACTOR <–“
Ironically, we reported news of the attack five days before LulzSec announced its haul, not knowing at the time who was behind the hack that was designed to expose details of applicants to The X Factor. The group didn’t have its own website at the time, so it took to the world’s most well-known torrent hosting website The Pirate Bay to release hundreds of thousands of names, email addresses, telephone numbers and street addresses of people wanting a shot at becoming the next big star.
In its first day, the group was happy to have amassed 50 followers, little did it know that it would be a drop in the ocean compared to now many followers it would accumulate in the days that followed.
Three days passed between The X Factor leak and its next big release, Fox.com’s “innerworkings” and a database drop of Fox’s sales database. During this time, “The Lulz Boat” was coined, ASCII art was drawn up, UK ATM details released and the group highlighted the password used by the Vice President of Fox.
On May 12, LulzSec announced it was contemplating creating its own website to host its releases and give it a proper presence on the web, predicting at the time that Twitter might not take kindly to the LulzSec Twitter account. As the next two days passed, the group released more Fox user credentials, teasing that it had data from an FBI affiliate and then announced that LulzSec had three people maintaining its Twitter account.
It was all quiet on the LulzSec front until it would become one of a long list of attackers that leaked Sony’s details, compromising databases hosted by Sony Japan and releasing them on Pastebin.
LulzSec finally got the press coverage it craved when it posted a seemingly innocuous link on its Twitter feed, linking to US TV network PBS. The tweet “http://www.pbs.org/lulz/ Oh shit, what just happened @PBS?” linked to a newly created page on the PBS domain but its decision to create a fake news article stating that “2Pac still alive in New Zealand” thrust the group into the spotlight, with every technology and online news outlet linking to the hack and LulzSec’s announcements.
The group had gained access to PBS’s internal hosts, its database list, staff database, authors database, pressroom users database, stations database and MySQL users database – which, at the time was its biggest overall haul of company-wide data. It was believed that the group took action after the network aired a show which was seen to paint whistleblowing website WikiLeaks in a bad light.
To make things worse, LulzSec adopted the theme-song from the Love Boat, all the while soliciting for Bitcoin donations.
LulzSec Enemies, LulzSecurity.com and More Sony “Ownage”
With more high-profile hacks, LulzSec found itself the target of other members of the Internet (in)-security scene, most notably @th3j35t3r, an attacker (or group of attackers) which was hellbent on exposing the identities of LulzSec members. Realizing that this was the case, LulzSec immediately began DDOS’ing the IRC servers used by th3j35t3r and also servers used by hacking magazine 2600.
On June 2, LulzSec released what it referred to as “Sownage”, a complete dump of Sony Pictures’ codes, coupons and user databases, stating that it had released details on “1,000,000 users’ personal information, including passwords, email addresses, home addresses, dates of birth, and all Sony opt-in data associated with their accounts”.
The following day, the group announced it had hacked Nintendo but did not release data stolen in the attack. However, a more notable release was issued the same day, an attack on InfraGard Atlanta’s user database, a company that was affiliated with the FBI.
The group issued a press release to accompany the hack, stating:
“It has come to our unfortunate attention that NATO and our good friend Barrack Osama-Llama 24th-century Obama have recently upped the stakes with regard to hacking.
They now treat hacking as an act of war. So, we just hacked an FBI-affiliated website (InfraGard, specifically the Atlanta chapter) and leaked its user base. We also took complete control over the site and defaced it, check it out if it’s still up: http://infragardatlanta.org/.”
Details emerged that the companies’ owner Karim Hijazi asked LulzSec to help him “eliminate [his] competitors”, which the group didn’t take kindly to. The group decided to release nearly 1,000 of Hijazi’s personal emails, as well as the IRC log where he spoke with the group.
At the beginning of June, LulzSec started releasing details of its exploits on LulzSecurity.com, presenting a united presence for its releases, making sure that copycats where unable to utilize Pastebin to piggyback of its name.
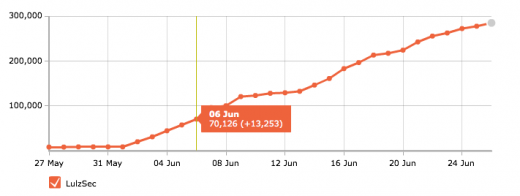
On June 6, the group crossed the 75,000 Twitter followers milestone:
Compromising The NHS, The Senate And Getting The Taiwan News Treatment
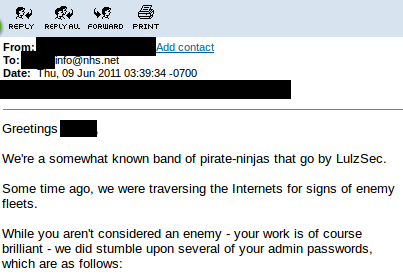
June 9 saw LulzSec admit it had managed to infiltrate the servers of the National Health Service (NHS) in the UK, but in a move away from its typical policy, the group decided to email NHS administrators and alert them to security holes in their online portal.
This gained LulzSec more press coverage, helping to boost the group’s Twitter following to above 100,000 followers.
This is a two page report, please click the button below to read the article in its entirety or to read the second page.
Within four days, LulzSec released a huge dump of adult website login credentials, continued its assault on popular online games by releasing internal data from Fallout creators Bethesda and captured the internal databases of Senate.gov, issuing the following statement:
“We don’t like the US government very much. Their boats are weak, their lulz are low, and their sites aren’t very secure.
In an attempt to help them fix their issues, we’ve decided to donate additional lulz in the form of owning them some more!
This is a small, just-for-kicks release of some internal data from Senate.gov – is this an act of war, gentlemen? Problem?”
On June 16, 62,000 random user email addresses and passwords were released, with LulzSec prompting its Twitter followers to access accounts to gain any sensitive information they can find.
“Be creative instead of being a potato. Try PayPal combinations, Twitter, Facebook, eBay, Runescape. Pick a target from the list.”
Within minutes, Lulz Security’s Twitter followers had already downloaded the file, hosted by MediaFire, 3200 times. This lead to LulzSec getting the Taiwanese news treatment:
Anonymous, Arrests And Arizona
With many of LulzSec’s followers believing the group was at war with Anonymous, the group’s announcement on June 20 may have been a massive shock. With LulzSec starting its new “AntiSec” campaign, it decided to throw open the doors to its new project and partner with Anonymous for its operation to “open fire on any government or agency that crosses their path”.
LulzSec’s Twitter followers began tagging real-world objects with #AntiSec, making sure to place the hashtag on websites if they had successfully gained access. During this time, the group turned to DDOS attacks on numerous targets, including the UK’s SOCA police website.
On June 21, the authorities took what they thought were first steps in bringing the members of LulzSec to justice. The Metropolitan Police, in collaboration with Essex Police and the FBI, arrested 19-year-old student Ryan Cleary, a suspected member of LulzSec.
The teenager was arrested on suspicion of contravening the Computer Misuse Act, and Fraud Act offences and was taken to a central London police station, whilst forces searched a residential address in Wickford, Essex, following the arrest.
Cleary now faces five charges, including one related to a recent Distributed Denial of Service (DDoS) attack on Britain’s Serious Organized Crime Agency’s website, which has been attributed to the LulzSec hacker group. The earliest charges he faces are from October and November last year and relate to attacks on the British Phonographic Industry (BPI) and the International Federation of the Phonographic Industry (IFPI) respectively. It’s telling that Cleary was charged with just one attack that is linked with LulzSec.
The group, which remained silent on the matter for a number of hours after the arrest, issued a response to the charges:
“Seems the glorious leader of LulzSec got arrested, it’s all over now…wait…we’re all still here! Which poor bastard did they take down?”
It later transpired that Cleary was only mildly associated with the group, mainly due to the fact he ran their IRC servers. It is not yet known if he took part in any of the more recent attacks.
On the same day as the arrest, LulzSec was also linked with an attack on the UK 2011 Census. We noted at the time that, if true, the Pastebin release was a step away from its traditional release process, as it was not accompanied with a tweet. The group later confirmed it was not behind an attack on the Census, with the Office of National Statistics confirming no intrusion was detected.
As the hacking group neared its final goodbye, it made sure to release “hundreds of private intelligence bulletins, training manuals, personal email correspondence, names, phone numbers, addresses and passwords belonging to Arizona law enforcement.”
Press and officials at the police department criticized LulzSec for the leak, saying it put officers at risk – LulzSec, of course, didn’t care, instead it joked about the content that the files contained.
Newsnight, Leaked Identities And A Goodbye
As the weekend fast approached, LulzSec did something it hadn’t done before – it engaged the press. Perhaps knowing it was about to call time on its operations, the group spoke with Gawker but made its debut on British TV in an interview on BBC current affair programme Newsnight.
In the interview, one Lulzsec member “Whirlpool” discussed LulzSec’s agenda and motives. Claiming “People fear new rules, people fear the higher-ups and we’re here to bring them down a few notches.”
Speaking via an online chat (full transcription can now be found here), Whirlpool revealed little new information, however one interesting nugget did come to light. LulzSec has been using the much discussed Bitcoin currency to receive donations. In total, Whirlpool claims LulzSec has received over $18,000 from fans and supporters. Whether that figure covers the costs involved in hacking major organizations, we can’t be sure, but when asked whether LulzSec planned to hack with political or monetary motivations in future, Whirlpool replied:
“At some point our operations will have to veer onto the more serious side of things that’s true. Our pirate hat is whitehat, grayhat and blackhat, so we often entertain many flavour of public. But yes, enjoying the breeze of politically-motivated ethical hacking is more fulfilling.”
We noted at the time that there was definitely no sense of LulzSec’s hacking crusade coming to an end any time soon. The group even posted the following message to its Twitter account:
“Monday release is being planned. We’re still here, fine sirs.”
So it came as a surprise to LulzSec’s 250,000 strong Twitter following when the group decided it was calling time on its operations. Posting “we have a very special surprise for you tonight!”, the group quickly followed that with a press release via Pastebin (of course) saying that it was quitting after fifty days of activity.
“For the past 50 days we’ve been disrupting and exposing corporations, governments, often the general population itself, and quite possibly everything in between, just because we could,” the group notes. “While we are responsible for everything that The Lulz Boat is, we are not tied to this identity permanently.”
“Our planned 50 day cruise has expired, and we must now sail into the distance, leaving behind – we hope – inspiration, fear, denial, happiness, approval, disapproval, mockery, embarrassment, thoughtfulness, jealousy, hate, even love.”
If LulzSec is telling the truth and this really is the end, it’s gone out with what seems like a bang. A torrent file posted to The Pirate Bay points to a 457.84MB download which claims to contain information that includes AOL internal data, AT&T internal data and the “FBI being silly” among its contents. You can read a breakdown of the files in our report, located here.
What was the reason behind the group’s sudden decision to stop its campaign? We may never know. However, shortly after the announcement, a file was released by online group “The A Team” which claimed to list and name each member of LulzSec, suggesting that some of its members were also affiliated with Gnosis, the online collective that hacked Gawker Media’s portfolio of websites.
The revelation may have helped the group decide that its time was coming to an end, before it found itself subjected to interrogations by the authorities.
With the dust still settling around the “50 days of Lulz”, some will be glad to see the back of the hacking group (if it is really the end) whilst some will be genuinely sad to see them disband. The group says supporters should assist Anonymous with its operations, helping the loose online collective with its own campaigns but also to continue Operation AntiSec.
The LulzSecurity.com site will be left and will expire, it is not known what will happen to its Twitter account.
No matter what your opinion on the group is, there is no doubt you checked your accounts and made sure they were that extra little bit more secure. Perhaps that was the goal of LulzSec all along, to ensure that Internet users took more care with their security, whilst declaring war against “corrupt” governments and agencies.
Get the TNW newsletter
Get the most important tech news in your inbox each week.