Not only are they super annoying, but it turns out text-based CAPTCHAs are also potentially a security risk.
Researchers from security firm F-Secure have figured out how to use AI to trick Microsoft Outlook’s text-based CAPTCHA into thinking a human solved it. In a blog post, the security experts explained the biggest challenge wasn’t correctly labelling the text, but mimicking the keystrokes a human would make when submitting the answer.
Considering their past experience in cracking text-based CAPTCHAs, the researchers were confident the mechanism protecting Microsoft’s Outlook Web App portal wouldn’t stand a chance. It turns out they were wrong.
After manually labelling about 200 CAPTCHAs, Outlook’s system turned out surprisingly resilient to F-Secure’s convolutional neural network, which could only identify the characters with an accuracy of 22%. This is when the researchers decided to up their sample size and label a total of 1,400 CAPTCHAs.
In the process, they figured out that the noise in the CAPTCHAs made it difficult for their AI solution to identify the letters. To counteract this effect, they tweaked their tool to remove noise.
Even after all this work, the algorithm didn’t perform any better — in fact, its accuracy dropped to a little under 16%.
Upon further inspection, the researchers realized that they wrongly labelled roughly 50 out of every 300 manually entered CAPTCHAs. Some of the common mistakes included confusing “I” for “l” (lower-case L) and “Y” for “V.”
They noticed a pattern: Outlook’s CAPTCHA mechanism never used “l” (lower-case L). With this in mind, the researchers narrowed down their crack alphabet, which helped them improve the accuracy of the algorithm from nearly 16% to 47%.
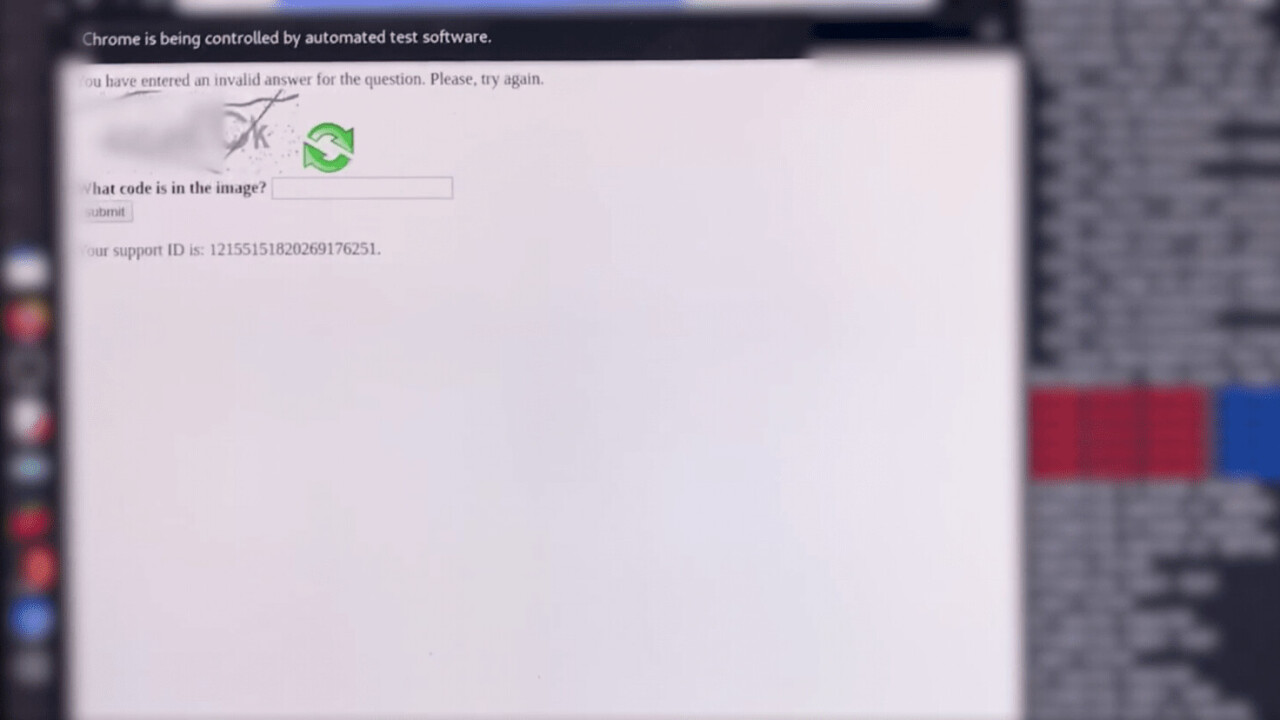
The next step was figuring out how to submit the cracked CAPTCHA to Outlook’s web portal. Since the CAPTCHA was designed to keylog each letter the user submits, the researchers had to mimic the keystrokes a human would make to fool the mechanism.
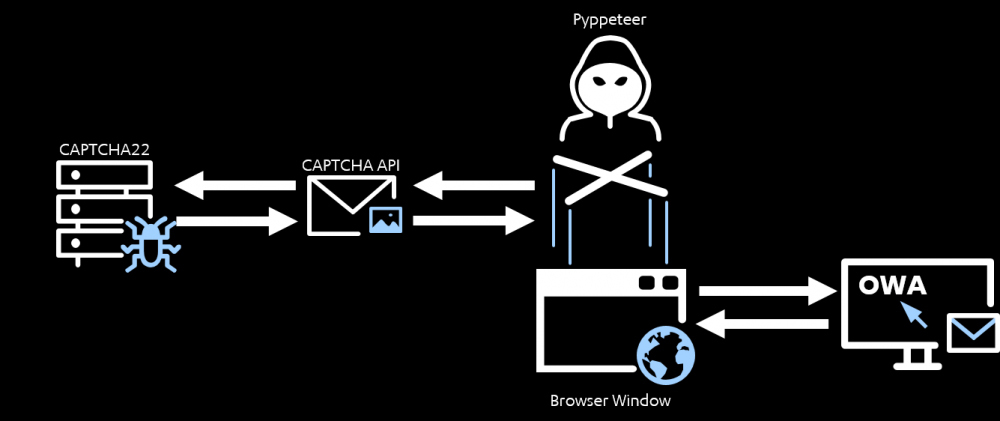
Here’s a video of F-Secure’s cracking tool in action. In the meantime, those interested in a closer look at F-Secure’s CAPTCHA cracking tool ought to head to this blog post.
Of course, breaking CAPTCHAs is nothing new.
Back in 2013, researchers developed software that cracked Google, Yahoo, and PayPal CAPTCHAs with an over 90% success rate.
“We said it last year and we will say it again: text-based CAPTCHAs are just not cutting it anymore,” F-Secure said in its blog post. “There are some interesting new CAPTCHA samples on the market, but it is just a matter of time before these also buckle under the CAPTCHA Cracken. We are not saying that CAPTCHAs are useless, they should just not be seen as the silver bullet that stops automated attacks.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.