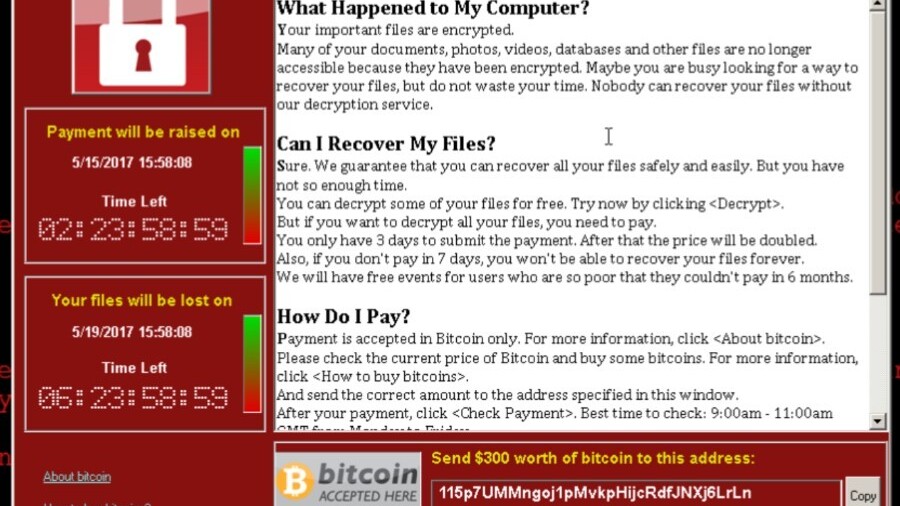
Ransomware is a type of malware that impairs the functionality of a computer (for example, by encrypting files on the hard drive), and then demands the victim pay a ransom in order to return their system to normal.
It’s frighteningly common. The term ‘Ransomware’ first entered the Oxford English Dictionary in 2012. We have seen several ugly and dangerous permutations of it, including CryptoLocker, CryptoWall, and most recently, WannaCry.
But it’s not the cash cow you probably think it is.
Take WannaCry, for example. This specimen devastated the UK National Health Service, as well as countless private sector businesses, like Spain’s Telefonica and Banco Santander. It took roughly a week for the Bitcoin wallets associated with the malware to reach $100,000 in payments. That’s not a huge amount when you compare it to the chaos it caused.
A recent paper from three University of Kent researchers, called “Economic Analysis of Ransomware” published in March of this year, makes several suggestions at how ransomware developers can increase their bottom line.
The researchers note that the money earned from ransomware is largely contingent upon people’s willingness to pay to recover their files. This is influenced by a number of factors, including how the victim values their files, and how much they trust that, should they pay, they will see their files again.
The paper suggests that ransomware developers aim to get 50 percent of those affected to pay up. One way to accomplish that is by creating detailed profiles of their victims, and charging accordingly. A person with a lot of files may be willing to pay more than someone with relatively few. Likewise, a victim may be more incentively to pay up if the files encrypted are vital work documents rather than, say, their music collection.
An attacker could also look at the hardware. Someone with a more expensive laptop might be more able (or willing) to pay than someone with a cheap netbook.
Gender also comes into play. According to the paper, women are more willing to pay to recover their files than men, saying:
“We find in our data that the willingness to pay is on average higher for women (mean £326) than men (mean £233) and increasing with age (correlation coefficient 0.07).”
Although it’s worth mentioning the paper notes that while this is interesting, it it isn’t statistically significant.
While the paper suggests that ransomware developers should be flexible with what they charge victims, it does suggest an “ideal ransom” of £950, where 10 percent of victims would have paid up, explaining.
An interpretation of this finding is that it is in the criminal’s interest to target high value victims that are willing to pay £1000 or above. For instance, at the optimum value the expected profit of the criminals is £99 per victim (because a little over 10% of victims will pay £950). If the ransom is dropped to, say, £150 then over 40% of victims will pay but this only results in a profit per victim of around £60.
You can read the entirety of the paper here. It’s a fascinating read. And it could be indicative of a future where ransomware attacks take a more sophisticated approach to pricing, rather than the current one-size-fits-all model.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





