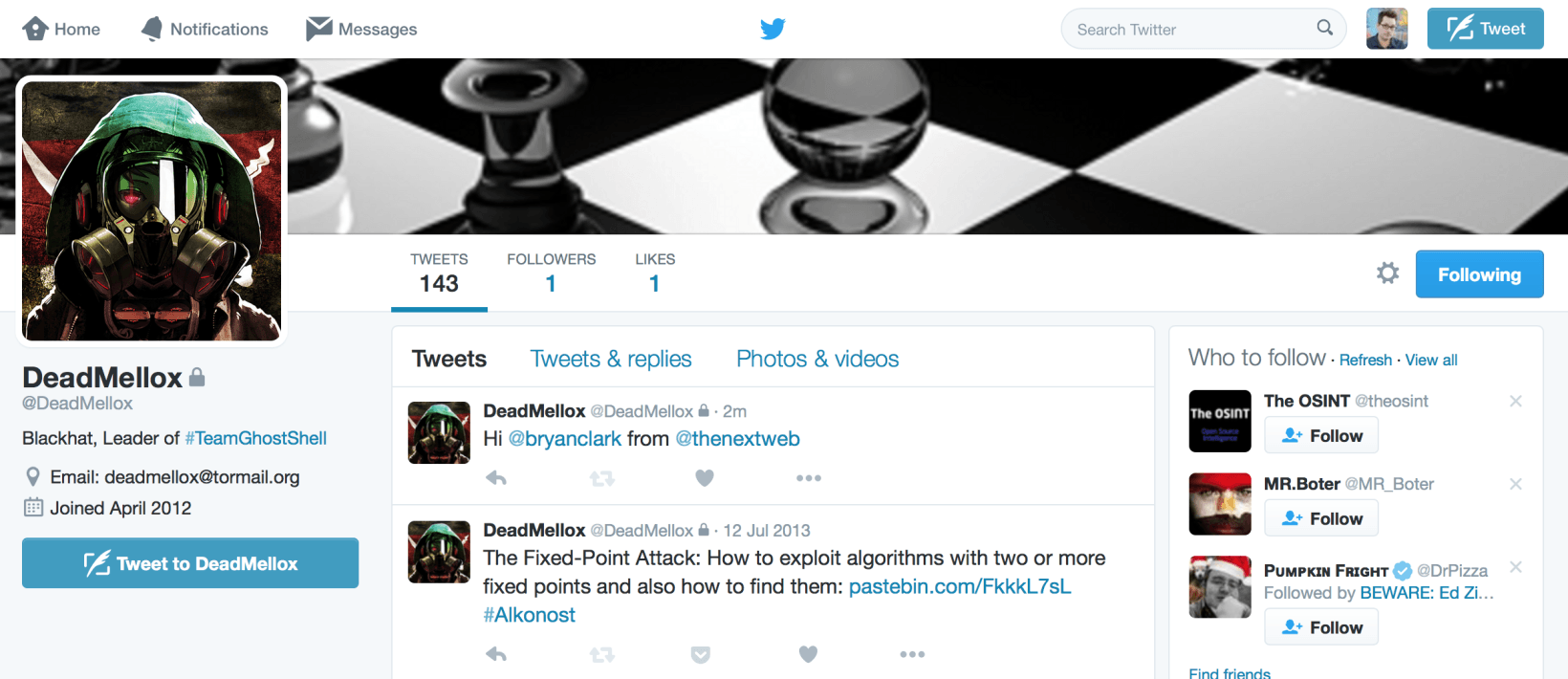
The man behind Team GhostShell — the hacker collective behind some of the biggest cyber attacks in recent memory, including attacks on the FBI, NASA and the Pentagon as well as a leak that saw 2.5 million Russian “government, educational, academic, political and law enforcement” accounts compromised — is ready to come clean and face the music.
GhostShell was most active in 2012, penetrating the aforementioned hacks on US and Russian intelligence agencies, but the silence that came in the three years between its last public attack and the subsequent return wasn’t quite the death of the group that many thought it would be.
In 2015, GhostShell came back with a vengeance, only this time a much darker, seedier version emerged hell-bent on destroying anything in its path and leaking information through its “dark hacktivism” campaign for seemingly no other reason than to prove it could.
The hacks included attacks on the Smithsonian photo contest website, Socialblade, The Church of Jesus Christ of Latter-day Saints and even the Exploratorium in San Francisco.
GhostShell, it seemed, was hacking sites out of spite, just to prove to the world that the Web was boundlessly hackable all while publicly mocking the likes of security firms Trend Micro and Booz Allen Hamilton.

TNW was approached by a man using a generic Yahoo email address, with the name White Fox that claimed to be the leader of the infamous hacker collective. The email moniker is an important one, as it has been tied to a previous GhostShell project with the same name.
In 2012, GhostShell claimed responsibility for a hack — dubbed #ProjectWhiteFox — that saw the leak of 1.6 million records and accounts from US defense contractors, government agencies and trade organizations.
My curiosity was piqued.
After a series of email and some additional text correspondence, I was added to an email list that included a handful of other cyber security journalists, including those from the likes of Wired, The Telegraph, The Atlantic and others, 10 in total.
From there, he wasted no time in giving us all what we were anxiously awaiting, his true identity. I’ll let him tell the story.

I obviously had questions.
Verifying hackers is and always has been a tricky proposition. While it’s simple to verify that this person is a member of GhostShell, tying his true identity to that of a hacker pseudonym is infinitely more difficult.
Hackers, after all, are notoriously careful about keeping the two identities separate — OpSec mistakes in this crucial step are generally what lead to arrest.
First, I needed verification that Eugen was indeed a member of GhostShell. He provided this in the form of a Pastebin login that I was quickly able to confirm was legitimate, and used by the official GhostShell Twitter account (@TeamGhostBin) to disseminate leaked information before its suspension.

Tying the (claimed) real identity to the pseudonym, or one of several pseudonyms, was a bit more tricky.
So, I sought as much info as I could gather.
Luckily, Eugen was more than happy to help out. He turned over photos, email accounts and even the private Twitter account he had been using to communicate for several years, @DeadMellox — another pseudonym that had been tied to GhostShell, but has since been abandoned.
Overall, we can’t with 100 percent certainty say that Eugen’s claims are correct, and that he is indeed GhostShell, but the case is pretty compelling.
Next I had to know why. Why now? Why reveal yourself at all? This is, after all, a group that’s wanted in multiple countries and has taken a place on several “most wanted” lists for cyber criminals.
Eugen told me:
“I just want to own up to my actions, face them head on and hope for the best. What I really want is to continue being part of this industry. Cybersecurity is something that I enjoy to the fullest even with all the drama that it brings and legal troubles.In return I hope other hackers and hacktivists take inspiration from this example and try to better themselves. Just because you’ve explored parts of the internet and protested about things that were important to you doesn’t mean you should be afraid and constantly paranoid of the people around you.”
GhostShell is a collective, and one that operates all over the world. Despite this, Eugen wants to make it clear “[other members] were never directly involved in the main projects/leaks. 99 percent of them are from me.”
While it’s admirable that Eugen is ready to face the music, the “music” in this case is probably a kicked in door and several years in prison, a fate that he’s well aware of.
He won’t be the first — or the last — hacker to face this fate. In fact, Eugen has already seen several of his friends and acquaintances made examples of by court systems promising to get tough on cyber security.
Several of these acquaintances can only be described as hacking elite, including notorious hackers Sabu, Adrian Lamo and Zeekill, but all were caught after lengthy investigations by law enforcement and intelligence agencies.
Eugen, is a rare breed. He’s going to go down on his own terms, but not before telling the story that he wants to tell.
Get the TNW newsletter
Get the most important tech news in your inbox each week.