
There’s a lot IT pros get wrong about social engineering, but let’s start with what we get right. We know that social engineering is one of the most powerful tools used by attackers today. In fact, it’s probably at the root of every major breach of the past year.
We err in our understanding of how social engineering manifests. We tend to think of social engineering as a technique used in advanced attacks against specific organizations. We imagine attackers collecting bits and details about the organization, its structure and its employees.
We envision them aggregating all the digital traces that employees leave around the cyber universe and then using this information to create that irresistible email to which one or more employees will fall prey, providing the attacker with the magical keys to the kingdom.

The reality is less glamorous, yet much scarier. As Imperva pointed out in a recent blog entry, most cybercrime activity stems from massive infection campaigns that rely on mass-scale social engineering.
Using the law of large numbers and the very basic elements of human behavior, attackers determined the optimal email messages and techniques for targeting large populations. They found that, when distributed in large enough numbers, these messages are bound to find their perfect victim.
By choosing general addresses like info@someorg.com and hr@someorg.com, these campaigns become even more effective. Smaller distribution lists reduce the likelihood the messages will be tagged spam.
Attackers target both work and personal accounts in social engineering campaigns. For enterprise the risk of phishing is especially pertinent, because one user’s mistake may enable large-scale persistent attacks on the organization’s network.
There have been many articles covering the most obvious indicators of phishing, including poor spelling and grammar, typos, requests for personal information, mismatched hyperlinks and special offers. Today I want to take a closer look at a couple of less well-known indicators of phishing, using examples straight from my own inbox.
Tell-Tale Sign #1: The never-ending recipient list
An email might be engineered if it includes a very, very, very long recipient list.
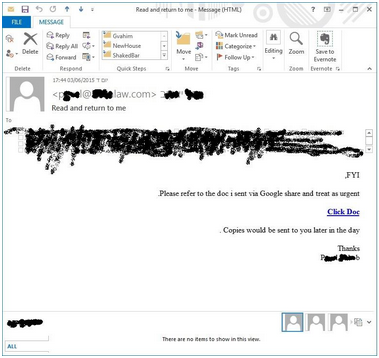
I recently received this email from a law firm with which I worked previously. I read the header information and was able to verify the message was indeed sent from the mailbox of a lawyer working for that firm. Should be safe, right?
Nope. Take another look. With an eye tuned for possible phishing you’ll notice the recipient list feels sort of bulky – that’s because it is. It includes every contact in the lawyer’s contact list.
This seemingly personalized attack was actually the result of two automation tools – one that infects individuals indiscriminately (to which the specific lawyer fell prey) and another that goes through victims’ contact lists and sends further phishing emails.

People on the list included clients as well as attorneys in other firms. The victims fell prey to this phishing attempt because it appeared to be the documents they were waiting for. The attack succeeded because of the overwhelming likelihood at least some of the recipients were waiting on a document from the “sender,” the victim lawyer.
Tell-Tale Sign #2: Vague messages from a seemingly familiar source
This second sign requires extra vigilance to spot. Here messages are not sent through the account of a company but from a separate account impersonating the sender’s address.
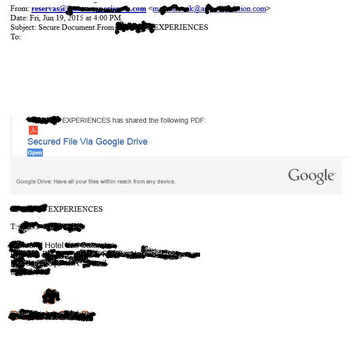
This second message came in from a travel agency in Brazil with which I just booked a trip via email exchange. Since the travel company is small, I was expecting a customized itinerary from them.
A fan of conspiracy theories would grab onto this with both hands claiming that someone tracked me down, found out that I was planning a trip with this company and took advantage of the opportunity to craft this message just for me.
While I’d love the extra attention, the reality is that a computer inside the agency was already infected with a Trojan that once in a while goes through the list of recently sent emails, grabs the recipients’ addresses and sends them this standard message using a lookalike address.
No doubt that a less suspecting individual than me (probably 99.99 percent of healthy population) would have fallen prey for this phishing scam.
Tell-Tale Sign #3: A compressed résumé
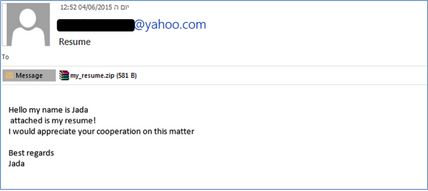
Our third and fourth signs have to do with the contents of an email. Let’s start with résumés.
The information contained in a résumé, while not confidential, is certainly personal. It makes sense to protect this information—address and phone number in particular—by only sharing a résumé with legitimate recruiters. I imagine most of us would send a PDF, .doc or .docx file to said recruiters.
A few months ago, I received this email from Jada the jobseeker. While Jada claimed to send “best regards” with her résumé, the file was, in fact, malicious. This message is part of a new résumé-themed campaign transmitting version 3.0 of the infamous CryptoWall ransomware. Needless to say, it is capable of wreaking havoc on businesses and people alike.
The malicious file uses an Adobe PDF icon, which tricks users into double-clicking, and thus running, the program. At this point, the phishing campaign becomes a whole different beast: ransomware. For our purposes, the takeaway here is to question why a candidate who wants their materials reviewed would send a zipped file in the first place. They likely wouldn’t and phishing is a far more probable explanation.
Tell-Tale Sign #4:
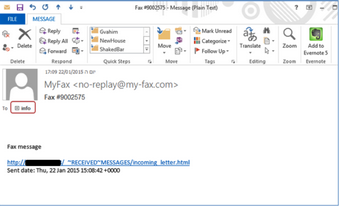
A different type of spam campaign hitting mail servers uses malicious fax and voicemail notification emails. These emails contain information that is typically included in legitimate fax and voicemail messages, such as a caller ID or confirmation number.
Clicking the link in the mail downloads the “Upatre” downloader, which eventually loads the dangerous “Dyreza” banking Trojan. At this point, it’s likely too late to remedy the issue.
The best defense against this form of social engineering is careful consideration of voicemail and fax notifications. Given the widespread adoption (and preference for) email and electronic documents, a voicemail or fax notification should at the least warrant the question, ‘What decade is it?’ The fact the message is addressed to “info” should also tip off users to a phishing scam.
Replying all on defenses
While employee education on phishing is key to reducing risk, it’s important to note this lesson must go beyond the usual social engineering methods to address subtler tactics.
Along with discussion of grammar mistakes and requests for confidential data, any conversation around social engineering should include long recipient lists, misleading sender addresses, compressed résumés and strange fax and voicemail notifications as potential warning signs.

By emphasizing the importance of approaching mail with a critical eye no matter the “sender,” expected number of recipients or supposed contents employers can encourage safer web use both in the office and at home.
The examples above also demonstrate how the combined force of the laws of large numbers and human behavior may sometimes prove unstoppable. With a large enough employee population, then, enterprises should consider compromise of some machines to be inevitable.
They must therefore also deploy monitoring and detection solutions around their business data assets to avoid the transition from a compromise to a breach.
Read Next: How to stop hackers from stealing your information on public Wi-Fi
Image credit: Shutterstock
Get the TNW newsletter
Get the most important tech news in your inbox each week.




