Git is a developer’s best friend… except when it’s not used properly and exposes a site’s security.
The tool is used for version control. It tracks changes to code over time, so that multiple developers can work together efficiently and roll back if they need to.
Git is also the core tool used to contribute to social coding site GitHub, though they aren’t the same thing.
It’s a glorious tool and fairly straightforward to use, but has a steep learning curve, as most of the interactions you’ll have with it are through the command line.
Git can also catch inexperienced developers off guard.
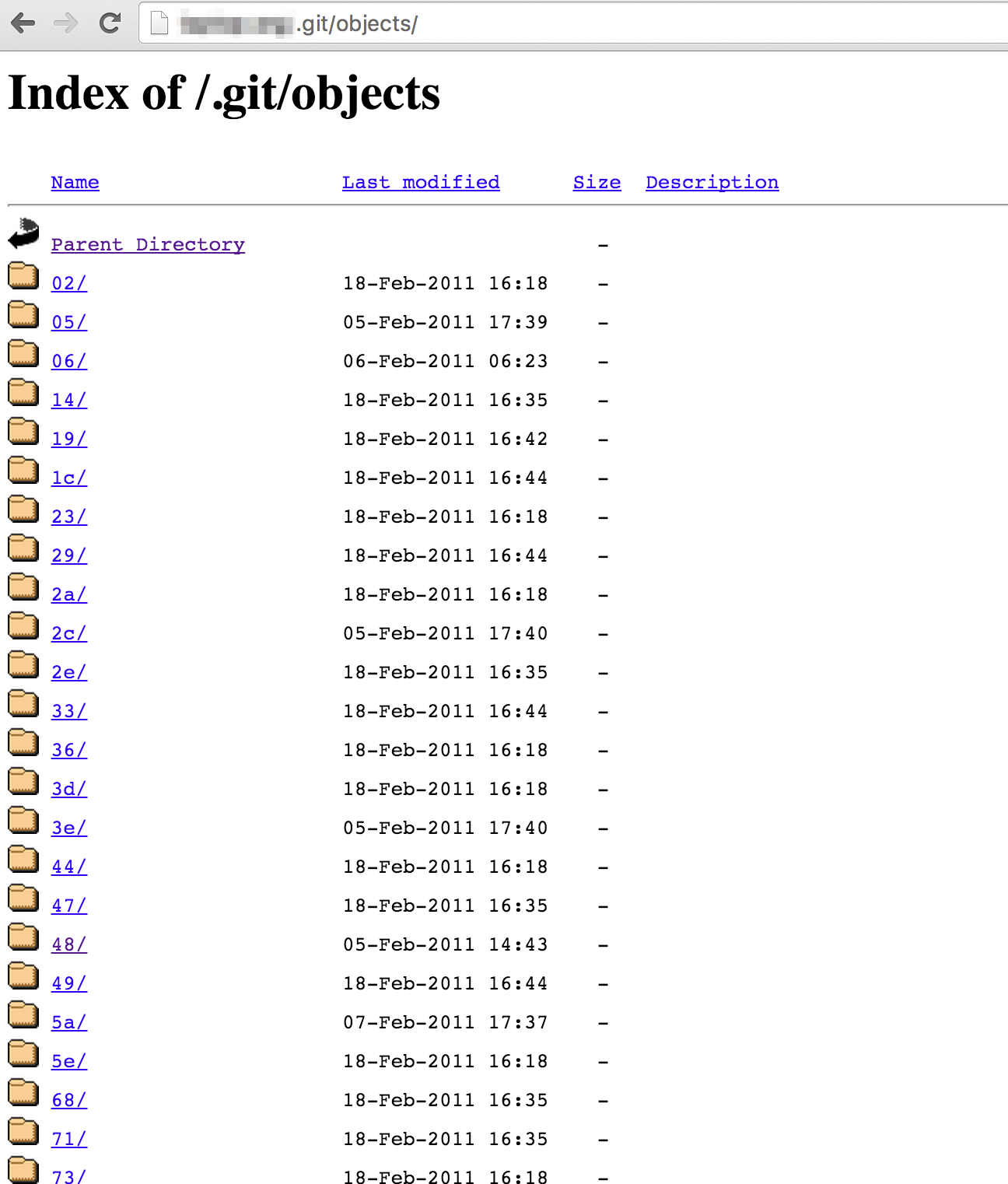
As it tracks your changes over time, it keeps them in a hidden folder — called .git. Exposing this to the world is catastrophic.
In many cases, revealing it means giving anyone access to source code, server access keys, database passwords, hosted files, encryption salts and more.
Unfortunately that’s exactly what many websites are doing.
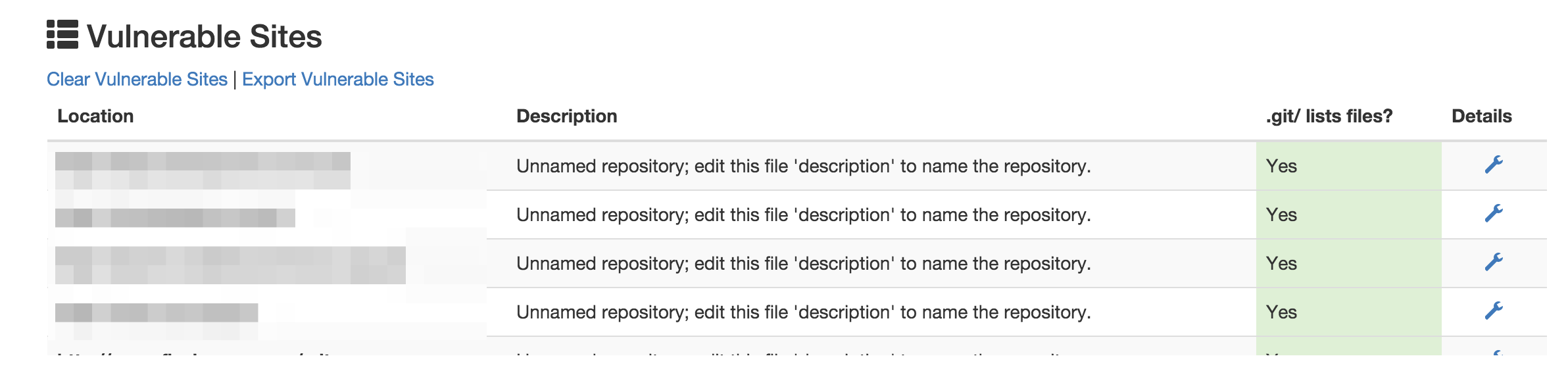
Jamie Brown, a developer, wrote on his blog that 1 in every 600 websites has its .git folder exposed to the world.It’s a rookie mistake to make when you deploy a site.
Brown says that 2,402 of the 1.5 million sites he tracks have an exposed and downloadable .git folder.
Brown gave me access to his database to verify the claims. I was surprised by what I saw.
A number of major universities, non-profit organizations and large companies are making the mistake of exposing their entire .git folder on the root of their domain.
At many of these groups the data is just sitting there, wide-open at http://example.com/.git/, waiting for an attacker to spot it.
Some of the .git directories are open, but harmless, as the developers had the forethought to exclude sensitive files from their version control. Others aren’t so harmless and include masses of sensitive data.
Brown said that one prominent human rights group exposed everyone who had signed up for a gay rights campaign, including their home and email address, in a CSV file tracked by their Git repository.
In our testing we came across a major non-profit that had over four years worth of its Git changes available online for the world to see, including SQL database backups.
We can’t name the companies in the spreadsheet as many of them still have sensitive data publicly accessible via this method, though I’m working to contact some of the organizations.
Unfortunately for those making this mistake there are already tools that exist to help the casual hacker spot it.
One publicly available Chrome extension automatically tests for the existence of the directory and sends a notification when it is discovered on a site.
It’s a dumb mistake with an easy fix: don’t upload your .git repository to your website.
If the Git repository containing keys, passwords or hashing algorithms is wide open to those that know how to find it, no amount of security can help prevent an attack.
There are other ways to mitigate the impact if the files were uploaded. Server admins should disable file directory browsing or add a rewrite rule to servers to ban all access to the .git directory.
Many developers are taught not to check sensitive files, like AWS access keys into GitHub, but seem to be forgetting when deploying their sites just how sensitive the .git directory is.
If you’re responsible for a website, it’s worth checking right now to see if your .git directory is exposed and if it is, remove it.
➤ One in every 600 websites has .git exposed [Jamie’s OC]
Get the TNW newsletter
Get the most important tech news in your inbox each week.