
A hacking group believed to be from North Korea is reportedly stepping up its game to continue its cryptocurrency stealing campaigns.
In a statement published yesterday, security researchers from Kaspersky say they found evidence to suggest Lazarus has made significant changes to its attack methodology.
According to Kaspersky, the hacking group is taking “more careful steps” and is employing “improved tactics and procedures” to steal cryptocurrency.
In other words, Lazarus has adjusted the way it infects a system, remains undetected, and illicitly obtains cryptocurrency from compromised machines and victims. To go undetected, Lazarus’ malware executes in memory rather than being run from hard disk drives.
Researchers say Lazarus is now using messaging app Telegram — popular in the cryptocurrency community — as one of its key attack vectors.
Security Researchers have dubbed the new wave of tactics as “Operation AppleJeus Sequel.” An evolution of the AppleJeus campaign that was uncovered back in 2018 and ran throughout 2019.
As with previous campaigns, Kaspersky says fake cryptocurrency trading companies are used to lure in victims. The fake companies have websites complete with links to equally fake Telegram trading groups.
In one instance, a Windows system was infected by a malicious payload delivered to the device through Telegram messenger. The user downloaded the payload themselves through the app, Telegram itself wasn’t compromised.
Once infected, attackers can gain remote access to control the compromised device and further their attacks. Lazarus almost always goes after cryptocurrency.
During its research, Kaspersky found a number of these fake cryptocurrency trading websites. It believes they were made using free web templates.
As can be seen in the image below, one of the fake sites had an active link to a Telegram group. While Kaspersky has only recently uncovered that Telegram was used to deliver a Lazarus payload, the group itself was created way back in December 2018.
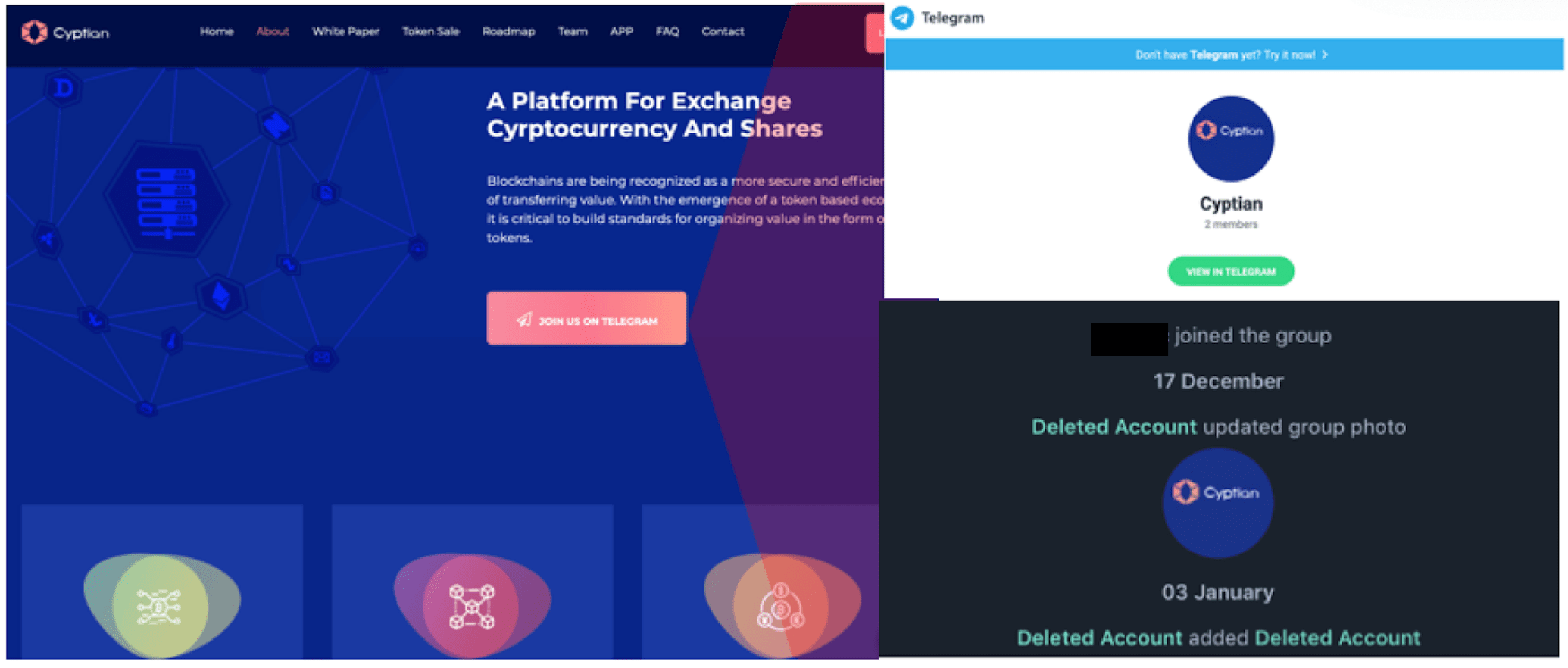
The researchers say they’ve identified several victims, based in the UK, Poland, Russia, and China. Several of these victims were confirmed to be cryptocurrency businesses.
The value of cryptocurrency or other funds Lazarus managed to obtain in this campaign wasn’t mentioned.
According to a UN report published last August, North Korean hackers were thought to have stolen $2 billion by hacking foreign financial institutions and cryptocurrency exchanges.
With the latest wave of updates to its campaign, it doesn’t look like Lazarus will ease up on its attempts.
Update, January 10, 2020, 1235UTC: The piece has been amended to reinforce that Telegram itself wasn’t compromised. The infected files were downloaded by victims from malicious links shared in the app.
Get the TNW newsletter
Get the most important tech news in your inbox each week.







