
Cybersecurity researchers have profiled a hacking crew named “Panda” believed to have amassed roughly $90,000 worth of cryptocurrency via remote access tools (RATs) and illicit mining malware.
The Cisco Talos Intelligence Group noted that while Panda isn’t exactly sophisticated, it has persisted as one of the internet’s most active attackers in recent years.
Talos researchers highlighted the group’s willingness to continuously exploit vulnerable web applications worldwide as key to its success. By October last year, a configuration file featured in Panda malware had been downloaded more than 300,000 times.
“They also frequently update their targeting, using a variety of exploits to target multiple vulnerabilities, and is quick to start exploiting known vulnerabilities shortly after public POCs become available, becoming a menace to anyone slow to patch,” said the firm.
Panda has a big bag of RATs (and other exploits)
Panda was first detected in mid-2018 during the wildly successful “MassMiner” campaign. This was powered by a worm which leveraged multiple in-built exploits, and even brute-forced access to Microsoft SQL servers, to mine the alternative cryptocurrency Monero (XMR).
Now, Panda reportedly utilizes Mimikatz, an open-source program for stealing sensitive information from compromised systems, such as usernames and passwords.
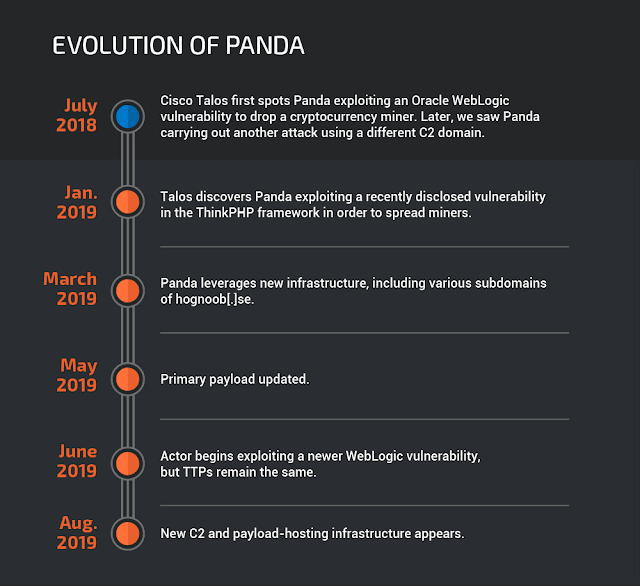
Researchers also found Panda operates with exploits previously used by Shadow Brokers, a hacking crew that gained its reputation by publishing information taken from the US National Security Agency.
To date, Talos has confirmed that Panda has hit organizations in the banking, transportation, telecommunications, IT services, and healthcare industries.
This cryptocurrency mining crew could be of Chinese origin
Whoever is behind Panda doesn’t really care too much about operational security. For example, the group got its name as one related domain had been registered to a Chinese-speaking actor who went by the name “Panda.”
An analyzed malware sample also requested data using an IP geolocation service which provided the machine’s IP address and location in Chinese.
Even more curious, Talos analysts found Panda had been exploiting a vulnerability in the ThinkPHP web framework to spread its malware. Researchers report this software is particularly popular in China.
“Panda’s operational security remains poor, with many of their old and current domains all hosted on the same IP and their TTPs remaining relatively similar throughout campaigns,” wrote the firm. “The payloads themselves are also not very sophisticated.”
Still, Panda’s efforts are said generated around 1,215 XMR in profits, which today is worth around $90,000 — but the exact amount earned is dependent on when they sold their cryptocurrency.
That’s one prolific hacking panda.
Get the TNW newsletter
Get the most important tech news in your inbox each week.



