
As long as cryptocurrency has value, people will try to steal it.
According to the latest figures from cybersecurity firm Avast, a cryptocurrency stealing malware has been blocked more than 360,000 times by its software.
The malware, named Clipsa, is described by Avast as a “multipurpose password stealer.” It exploits numerous attack vectors to steal or illicitly mine cryptocurrency.
Avast says the malware can replace cryptocurrency addresses in an infected system’s clipboard to redirect funds away from their intended destination and toward wallets owned by hackers.
More than just theft
Several versions of Clipsa have also been recorded to deploy XMRig, a cryptocurrency mining script that runs surreptitiously on infected systems. All cryptocurrency mined is then sent back to the hackers, earning them a pretty penny at the expense of the infected system’s owner.
Security researchers from Avast believe the malware is being distributed as part of a malicious codec installers for media players.
The campaign appears to have focused on India. Avast says it has blocked more than 43,000 Clipsa infection attempts in the country. More than 28,000 users were implicated in these attempts.
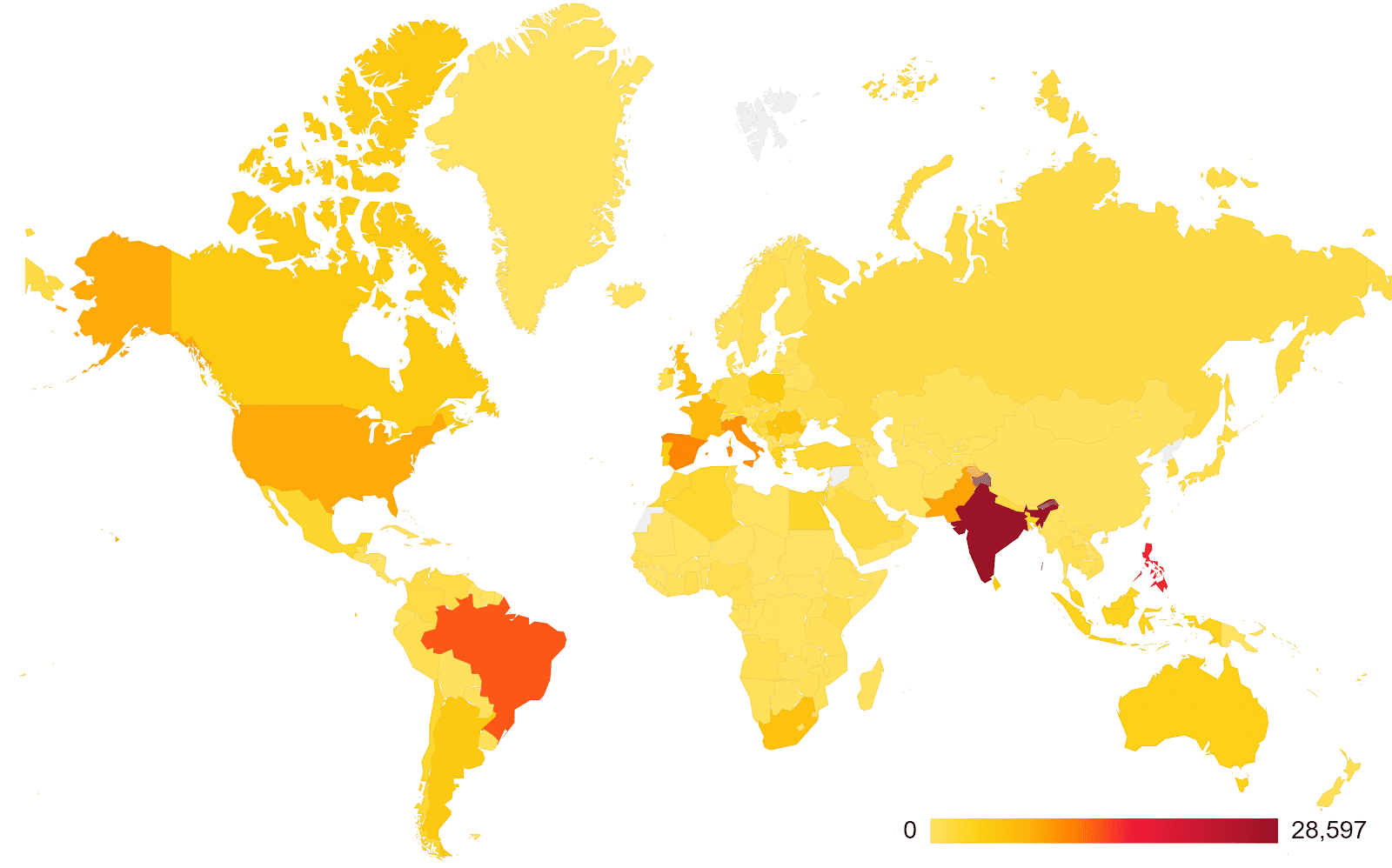
Clipsa has also targeted the Philippines and Brazil where Avast says it prevented more than 15,000 and 13,000 users from being infected, respectively.
Between August 2018 and July 2019 Avast says it blocked Clipsa from infecting computer systems more than 360,000 times, protecting more than 253,000 users in the process.
Given that this is just one security firm’s figures, actual infection attempt figures could be much higher.
Fortunately, incidents of Clipsa seem to be decreasing. The malware was most prevalent towards the end of 2018. Reports have been dropping since the start of the year.
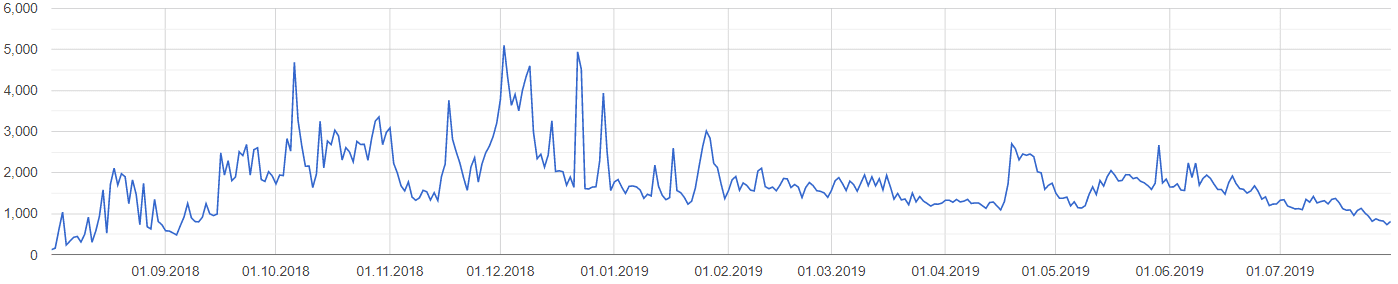
Even so, Clipsa has had some success in stealing cryptocurrency from unsuspecting victims.
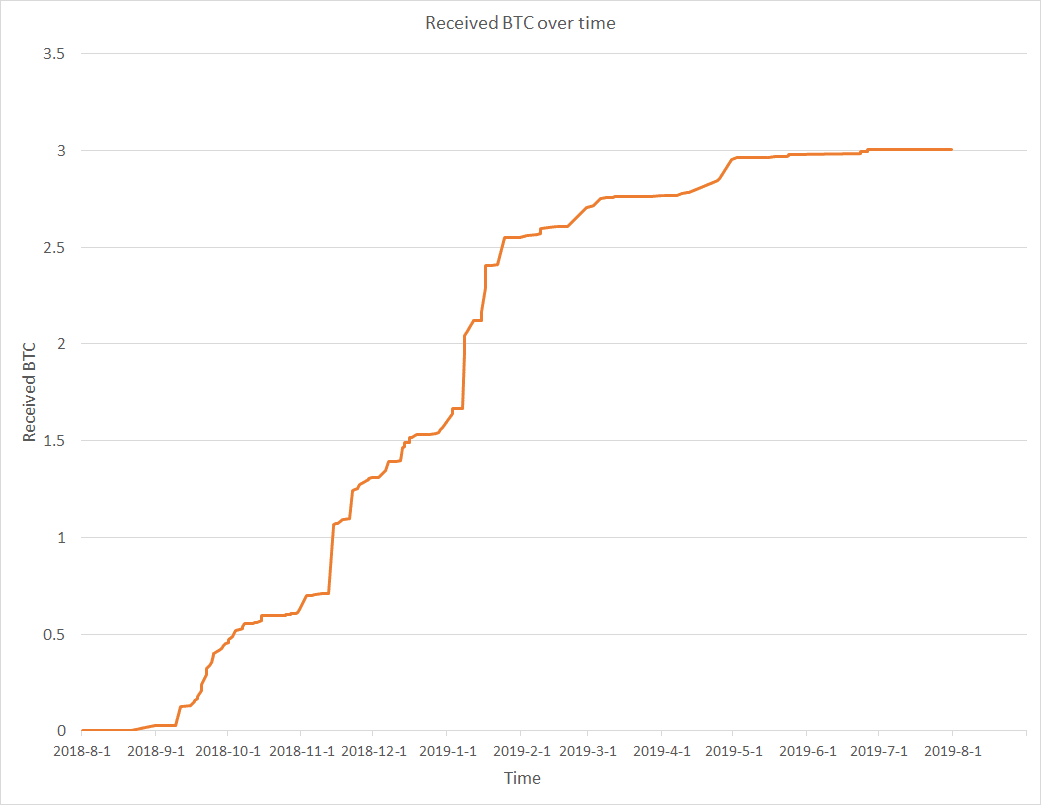
Avast’s analysis of malware files found Clipsa came pre-loaded with 9,412 cryptocurrency addresses that were ready to be used to hold stolen funds. However, only 117 were identified to have ever received any digital coins.
According to Avast’s list of addresses, hackers were able to net 300,214,005 Satoshis, or just over 3 Bitcoin, that’s about $36,700 at the time of writing.
As you might expect, the amount, and frequency, of Bitcoin that the hacker’s addresses were receiving tallies with the same period that Clipsa was most active (between late 2018 and early 2019).
Back in May, another cybersecurity firm, Malwarebytes, reported that it was blocking 1 million crypto-jacking attempts everyday.
It goes to show it’s worth running antivirus software and always scan any files you download before opening them. Even if you think they’re clean.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





