
Enterprise search engine Elasticsearch is under threat of being turned into a sophisticated cryptocurrency mining botnet to be used in distributed denial of service (DDoS) attacks.
Cybersecurity firm Trend Micro describes a new malware strain that launches multi-stage attacks on publicly accessible databases and servers that run old versions of Elasticsearch software.
“[…] Many of the malicious traffic or attacks that we see targeting Elasticsearch are relatively straightforward, and more often than not, profit-driven,” wrote Trend Micro.
“An attacker looks for unsecure or misconfigured servers or exploit old vulnerabilities, then drop the final payloads that typically consist of cryptocurrency-mining malware or even ransomware,” added the firm.
Not just a botnet, BillGates is here too
This malware is a little more evolved. First, it finds out-of-date servers, forcing them to download and execute a series of dangerous scripts with malicious search queries.
“The ways that the scripts are retrieved are notable,” said Trend Micro. “Using expendable domains, for instance, allows the attackers to swap URLs as soon as they are detected.”
Firstly, a script attempts to shut down any firewall running on the target machine. It then kills any competing or already-running cryptocurrency mining process, before downloading another script that’s likely hosted by an already-compromised website.
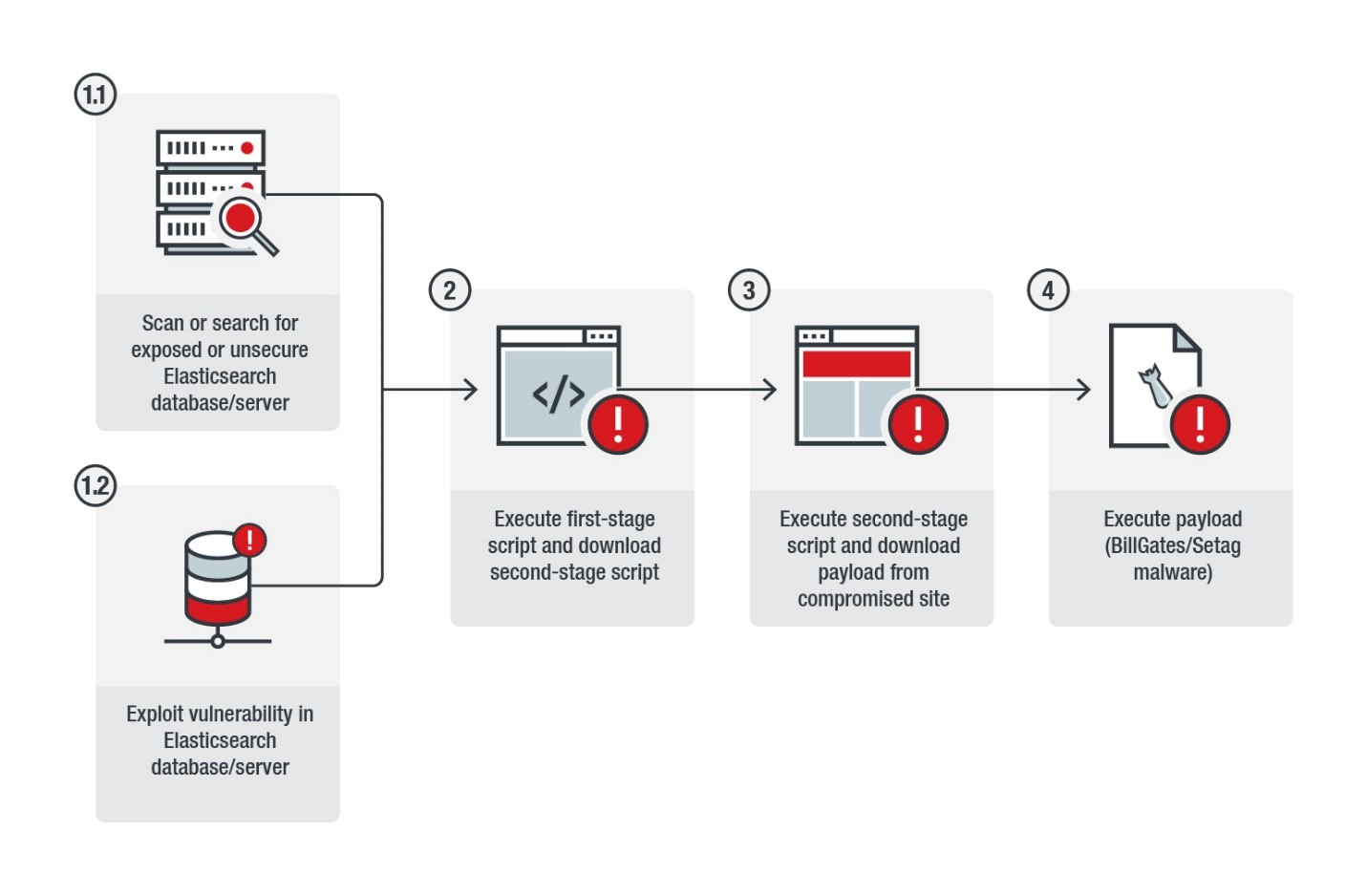
This secondary script generally prepares the host for delivery of the final payload by stopping firewalls, removing configuration files, and scrubbing traces of the initial infection.
Once this process is completed, the machine would be loaded with the BillGates/Setag malware, which is capable of hijacking systems, initiating DDoS attacks, and even linking up with other infected machines to form powerful botnets.
Is this preparation for bigger attack?
Ominously, Trend Micro researchers warned that any malware that evades detection and features multi-stage execution is a “red flag.”
“That the cybercriminals (or threat actors) behind this attack used URL encoding, staged where the scripts are retrieved, and compromised legitimate websites could mean they are just testing their hacking tools or readying their infrastructure before mounting actual attacks,” they said.
Those running Elasticsearch databases and servers are advised to patch their software immediately, as well as review guidelines on how to enable and configure security features.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




