
American retail behemoth Target has come out to clarify that a tweet it posted, containing a link to a Bitcoin giveaway scam, came from a third-party software provider – not Twitter.
In an email to Hard Fork, a company spokesperson said – contrary to what it suggested previously – Target’s Twitter account was never inappropriately accessed. Rather, it appears the attackers leveraged an account owned by one of its marketing vendors to send the tweet to its audience of almost two million..
“After a thorough investigation with Twitter and our cyber security team, we’ve confirmed that an attacker accessed one of our marketing vendor’s Twitter handles yesterday,” Target told Hard Fork. “This gave the attacker the ability to post an ad on Target’s behalf, and the vendor has since implemented a number of security measures to re-secure their account.”
“We can also update what we shared yesterday and clarify that there was no inappropriate access, at any point, to Target’s Twitter account,” the spokesperson added. “Nevertheless, we have taken a number of security measures and will continue to work with Twitter to ensure Target’s account is secure.”
The retailer refrained from naming the vendor in question.
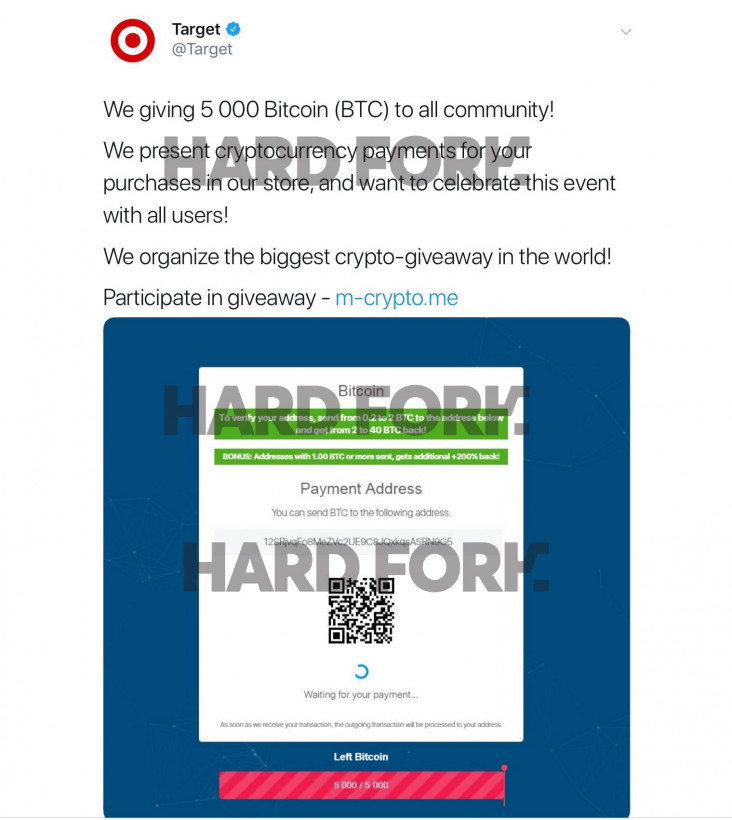
The Bitcoin giveaway scam mystery
The details provided by Target add an odd twist to the string of cryptocurrency-related breaches of big brands on Twitter, mostly for the purpose to promote giveaway scams.
In a window of less than 10 days, hackers managed to post malicious giveaway links from the accounts of politicians, film studios, government agencies, and even an official Google profile.
Twitter told Hard Fork on November 11 it is working hard on curbing the situation – moments before Google’s G Suite account posted a malicious giveaway link (which was swiftly deleted).
Considering the sheer volume of compromised accounts, it seems possible the hackers had gained access to a third-party app (authorized to post content from a large list of accounts).
Earlier this year, security experts warned certain, particularly inventive attackers are much more likely to target software-providers (with access to a bunch of accounts) than individual profiles. It seems the cryptocurrency scammers were paying attention.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





