
Is your computer suddenly sluggish and hot all the time? You might have fallen victim to this new Russian malware designed to steal your computing power to secretly mine cryptocurrency.
Researchers from McAfee labs have discovered a new breed of crypto-jacking malware which cannibalizes your computing power to mine Monero or Zcash.
What is particularly interesting is that the malware – dubbed WebCobra – will install a different miner depending on the configuration of your machine.
Upon close analysis, the researchers noticed the attackers are distributing the software through a malicious Microsoft installer package. Interestingly, the package was programmed to install Cryptonight miners on x86 systems, and Claymore’s Zcash miner on x64 systems.
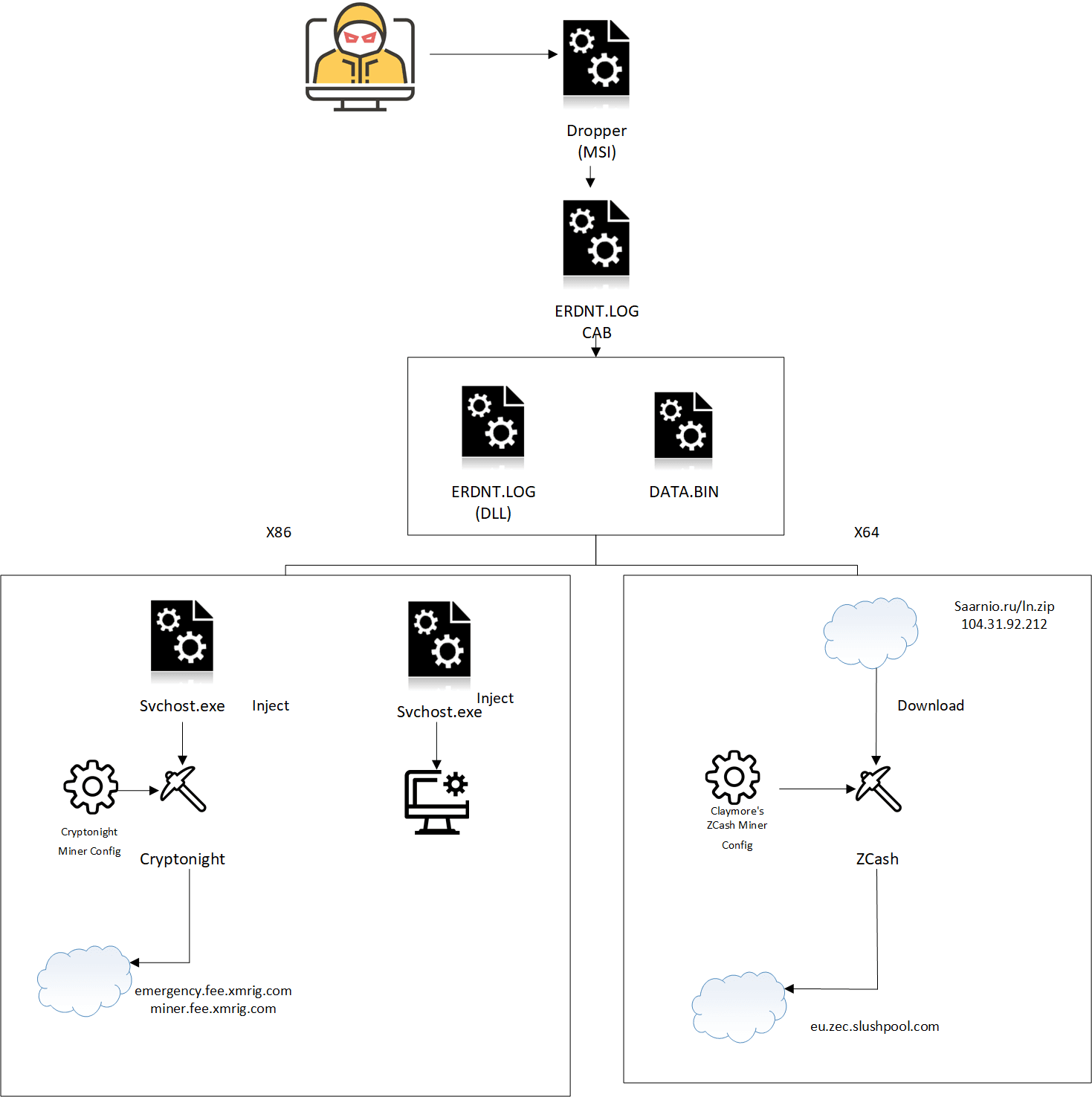
It is worth pointing out that the Cryptonight miner is not strictly limited to Monero. In fact, it is compatible with pretty much any other coin that uses the Cryptonight algorthm.
While the researchers tracked the origins of the malware to Russia, the report notes that currently the infection seems to have impacted Brazil, South Africa, and the US most severely.
One thing is for sure though: crypto-jacking attack vectors are getting more complex by the day.
Last week, researchers came across a new tactic which involved disguising mining malware as legitimate Windows installer files. Swiss security experts similarly warned cryptocurrency scammers are constantly adding new techniques – like trojan attacks – to their arsenal.
McAfee labs suggests that this trend is likely to continue – at least in the near future.
“The increase in the value of cryptocurrencies has inspired cybercriminals to employ malware that steals machine resources to mine crypto coins without the victims’ consent,” the report reads.
To give you some context, reports suggest that CoinHive – another Monero miner often employed by hackers – is generating over $250,000 in profits each month.
“Coin mining malware will continue to evolve as cybercriminals take advantage of this relatively easy path to stealing value,” the researchers conclude. “Mining coins on other people’s systems requires less investment and risk than ransomware, and does not depend on a percentage of victims agreeing to send money.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.




