
Crypto-jacking schemes are getting more intricate by the day. It appears hackers are now disguising cryptocurrency mining malware and passing it off as legitimate Windows installation packages.
Researchers say the malicious software, more commonly known as Coinminer, was specifically designed to fly under the radar. What makes the attack particularly difficult to detect is that it uses a series of obfuscation methods.
The discovery comes from security firm Trend Micro, which has since documented the attack vector at more length.
“The malware arrives on the victim’s machine as a Windows Installer MSI file, which is notable because Windows Installer is a legitimate application used to install software,” the report reads. “Using a real Windows component makes it look less suspicious and potentially allows it to bypass certain security filters.”
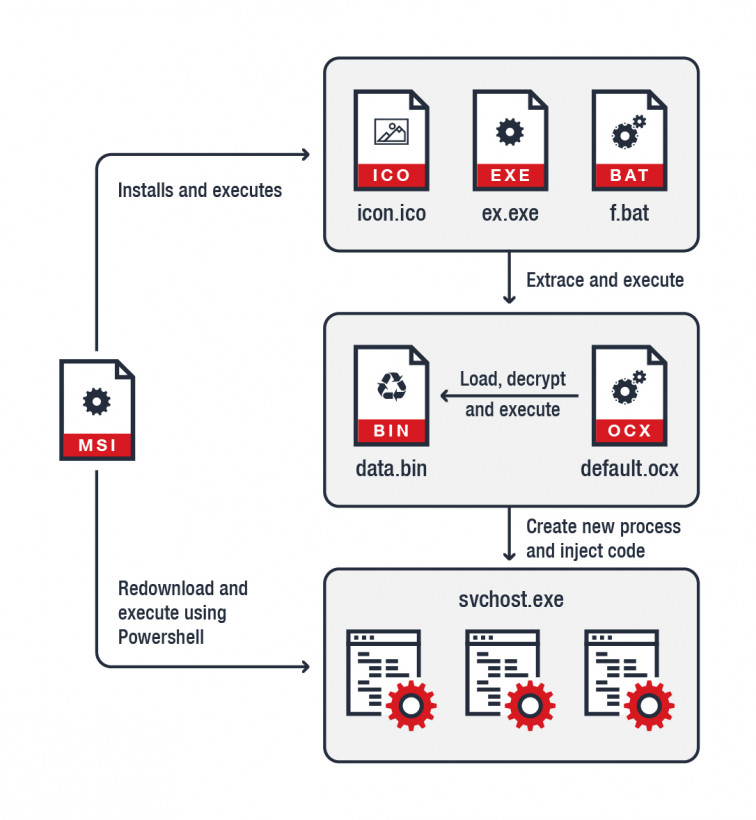
The hackers’ trickery doesn’t stop there though. The researchers note that, once installed, the malware directory contains various files acting as decoy. Among other things, the installer comes with a script that counteracts any anti-malware processes running on your machine, as well as the actual cryptocurrency mining module.
The researchers also observed that the malware has a built-in self-destruct mechanism to cover its tracks. “To make detection and analysis even more difficult, the malware also comes with a self-destruct mechanism,” the report says. “It deletes every file under its installation directory and removes any trace of installation in the system.”
While Trend Micro has been unable to link back the attack to a specific country, it notes the installer uses Cyrillic. In all fairness, Cyrillic seems to be pretty popular among cryptocurrency criminals.
The cryptocurrency mining malware epidemic
Back at the beginning of 2018, security experts warned that crypto-jacking scripts are expected to proliferate in all sorts of unexpected places.
Indeed, this year we’ve seen hackers sneak in cryptocurrency malware via Adobe Flash updates, routers, and thousands of commercial and governmental sites,
In the latest high-profile crypto-jacking case, last week a Canadian university was forced to temporarily kill its entire network after it discovered pesky hackers had been stealing its computing power to secretly mine Bitcoin.
Factoring in the scale of cryptocurrency mining malware, it is no surprise that reports suggest crypto-jackers are profiting more than $250,000 each month.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




