
Welcome to Hard Fork Basics, a collection of tips, tricks, guides, and advice to keep you up to date in the cryptocurrency and blockchain world.
Every week there seems to be an alert for a new cryptocurrency hack or scam. Honest, hardworking cryptocurrency hodlers need to be aware of the risks that come with digital assets, lest they be stolen or extorted from them in embarrassing ways.
Crypto-jacking is fast becoming one of the internet’s biggest threats, but most people don’t even know what it is or what to do about it. If you do want to understand crypto-jacking better and know how to protect yourself from it, just read on.
What is crypto-jacking?
To the uninitiated crypto-jacking might sound complex, but in principle, it’s actually quite simple.
Crypto-jacking is the name given to a type of malicious hack that steals your computer’s hardware resources to mine cryptocurrency for someone else. As a result, you’ll be paying the electricity bill and reaping none of the rewards.
Have I been crypto-jacked?
Crypto-jacking uses your computer resources to mine cryptocurrency, which is very CPU intensive. If your computer seems to be running hotter and noisier than normal, then you might have been crypto-jacked. Just listen to how loud commercial cryptocurrency mining operations are.
One of the quickest, easiest, and in fact, best ways of confirming if you’ve been crypto-jacked is to fire up your computer’s resource monitor and check your CPU use. For Windows, you can use Task Manager and for Mac users, the Activity Monitor.
For reference, here’s what normal CPU usage should look like.
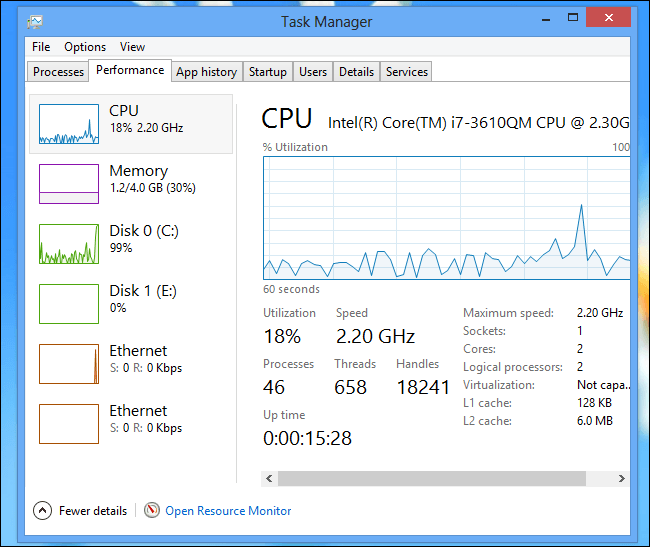
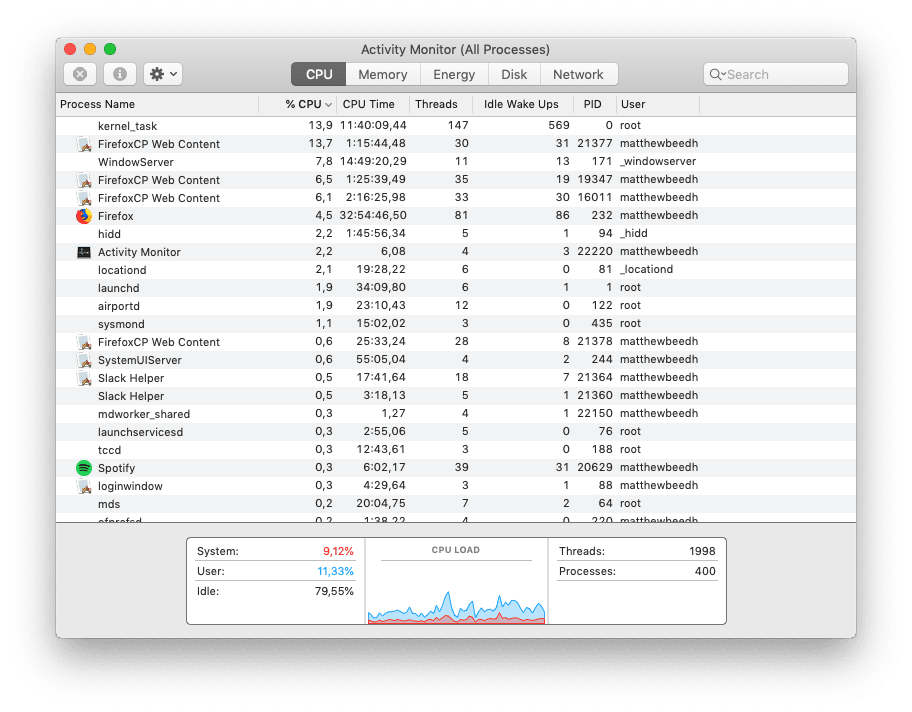
If your CPU is working at full capacity all the time, even when you think it should be idling, then you may have been crypto-jacked.
You can also get a confirmation by using this crypto-jacking test, made by the good folks over at Opera. Just visit the link in your web-browser, click start, and await your results.
Luckily, there are a number of things we can do to protect ourselves against crypto-jackers and keep our hardware out of their hands.
How to protect yourself against crypto-jackers
Crypto-jacking comes in many shapes and sizes — making it difficult to counteract — but attackers generally share a few common tactics. Some hackers run malicious script on websites that you might visit, and others infect your computer when you click on dodgy links. Some even hide the code alongside legitimate software updates.
One of the most common forms of crypto-jacking infects web browsers and websites with malicious code. Every time you run your web browser or visit an infected site you inadvertently mine cryptocurrency for people who don’t really deserve it.
Usually, if you stop the code, you stop the crypto-jacking. The first port of call should be to run a good anti-virus. The likes of Avast and Norton are adding crypto-jacking definitions to their virus libraries to pick up on these cybernasties.
If crypto-jackers have managed to sink their claws into your browser, then the best response is to update your browser and install a cryptocurrency mining blocker extension.
Chrome has a few to choose from. Top rated extensions include minerBlock, No Coin, and Coin-Hive Blocker. Firefox also features NoMiner in addition to its own version of minerBlock.
If you’re a webmaster and concerned about the sites you look after check here for information on how to keep your internet real-estate protected.
Another increasingly popular form of crypto-jacking is to infect routers with mining scripts. After all, they’re always switched on, and people rarely perform any kind of maintenance on them.
Establishing whether your router has been hit by crypto-jackers is a much more technical process, which involves monitoring web-traffic. So for most of us, the best plan of action is to update your router’s firmware to the latest version to ensure it’s as secure as it can be.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




