
North Korean hacking outfit “Lazarus” is the most profitable cryptocurrency-hacker syndicate in the world.
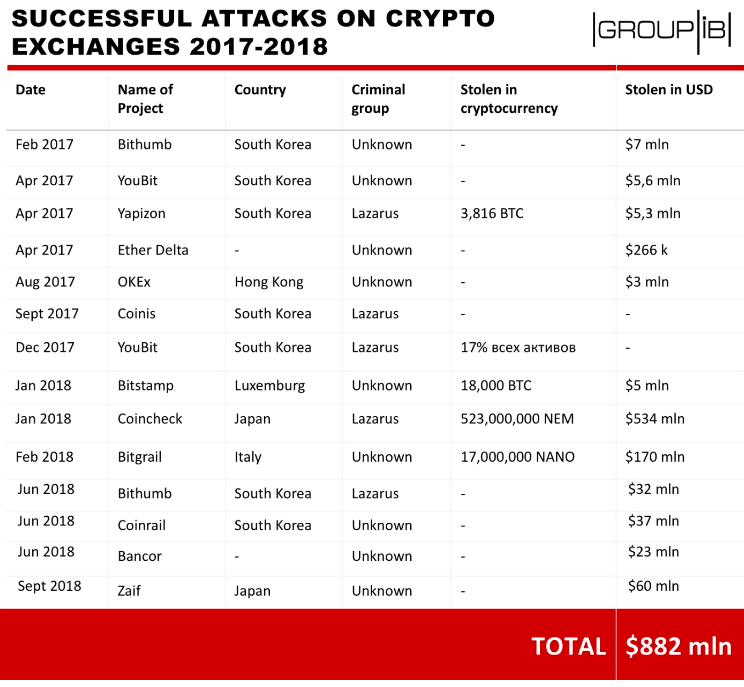
Since 2017, internet baddies have in total stolen $882 million worth of cryptocurrency from online exchanges, but none have done it quite as well as the infamous North Koreans.
World-renowned cybersecurity unit Group-IB is prepping to release its annual report on trends in hi-tech cybercrime.
A summary obtained by Hard Fork details 14 different attacks on cryptocurrency exchanges since January last year and calculates the state-sponsored Lazarus group is responsible for $571 million of the ill-gotten gains.
That’s well over half the total sum, more than half a billion dollars.
Hackers targeting cryptocurrency exchanges mostly use traditional methods and tools, such as spear phishing, social engineering, and malware.
“Spear phishing remains the major vector of attack on corporate networks. For instance, fraudsters deliver malware under the cover of CV spam [with an attachment] that has a malware embedded in the document,” the summary explains. “After the local network is successfully compromised, the hackers browse the local network to find work stations and servers used working with private cryptocurrency wallets.”
Group-IB expects the number of targeted attacks on cryptocurrency exchanges to rise, and not just the ones from Lazarus. It warns the most aggressive hacker groups, usually known for attacking banks, will shift their attention to cryptocurrency exchanges now they know just how lucrative it can be.
Phishers responsible for 56% of stolen ICO funds
The report also reveals 10 percent of the total funds raised by ICO platforms over the past year and a half have been stolen. A majority of the funds were lost to phishing.
Group-IB attribute much of the losses to baddies taking advantage of “crypto-fever,” where investors are so overcome with a fear of missing out they rush to contribute to new cryptocurrency projects as fast as possible, without checking for fake domain names.
According to the report, large phishing groups are capable of stealing roughly $1 million a month.
Cryptocurrency fraudsters are also getting more inventive. Group-IB found several instances of investor database theft, where hackers steal sensitive financial information to re-sell on the dark net or use to blackmail cryptocurrencers.
Fraudsters are even building fake websites using stolen cryptocurrency project descriptions and plagiarized whitepapers, disappearing with investor funds shortly after launching a fake ICO.
51-percent attacks are increasing
Group-IB predict attacks on ICOs will remain a threat for almost every project looking to attract investors.
“Fraudulent phishing-schemes involving crypto-brands will only get more complex as well as cybercriminals’ level of preparation for phishing attacks,” the group warns. “Automated phishing and the use of so-called ‘phishing-kits’ will become more widespread, including for the attacks on ICOs.”
Ominously, Group-IB also floats the possibility of the world’s largest mining pools becoming an easy target for state-sponsored hackers, declaring attempted ‘51-percent attacks‘ to be increasingly common.
For 51-percent attacks to be successful, bad actors must control a majority of the total computing power utilized by a Proof-of-Work powered blockchain.
“In 2017, no successful 51-percent attacks were detected, but they are now [happening] more often. In the first half of 2018, five successful attacks were registered with direct financial losses ranging from $0.55 million to $18 million,” Group-IB reports.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




