Fledgling blockchain startup IOTA has ran into yet another technical issue. Researcher Joseph Rebstock has detailed a vulnerability in its network which makes users susceptible to replay attacks – a common exploit vector in which valid data is erroneously repeated in order to steal cryptocurrency from users.
The issue stems from a function related to IOTA’s choice to use one-time signatures when processing transactions on the Tangle – the company’s self-proclaimed “next-generation” blockchain technology which promises more efficient transactions and scalability.
“Reattaching is often required to get a transaction through and bundles can only be safely signed a single time,” the research explains. “Therefore the user is allowed to simply reattach any bundle of transactions they want without any proof of ownership. This should not be a problem because every bundle has a unique hash.”
But as it turns out, the function does not work as intended.
“The expected behaviour should be that only one use of the same bundle hash should be allowed inside a consistent transaction history (subtangle),” Rebstock writes. But instead, “[t]he coordinator will repeatedly approve the same bundle hash over and over.”
“This means that while you may have signed a transaction to send 500 Miota it can be attached to the network 10 times draining the account of 5,000 Miota,” he insists.
The researcher has provided several examples to prove the validity of the attack vector:
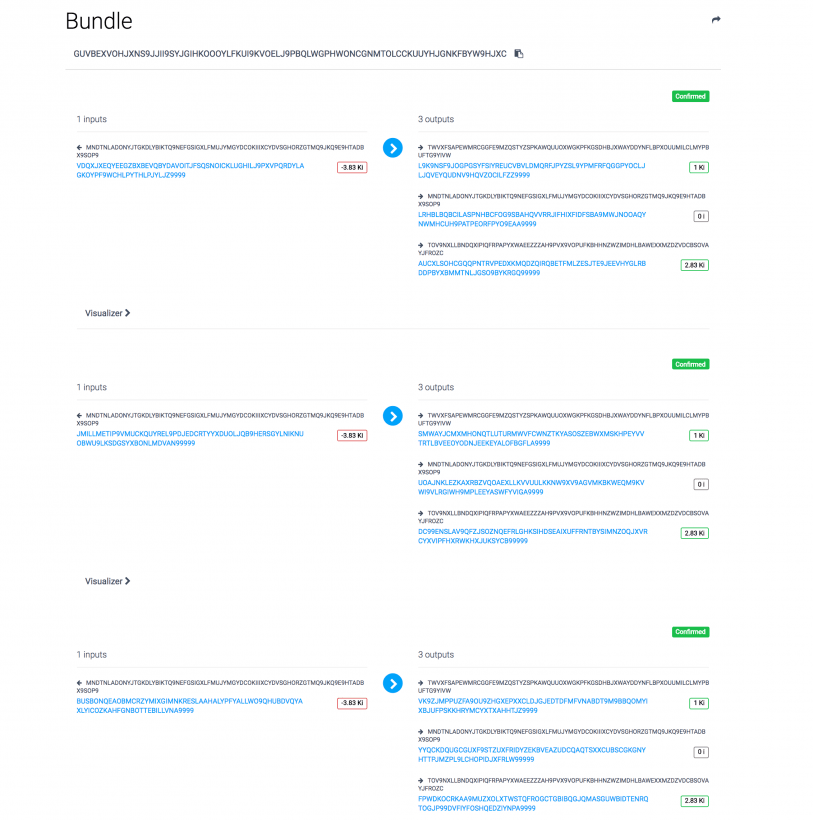
In all fairness, the attack vector described in the report hinges on reusing wallet addresses – a malpractice the company has repeatedly warned against.
Still, it is worth noting that, while the vulnerability is similar to the signature issue previously disclosed by Neha Narula from the MIT Digital Currency Initiative (DCI), this is a newly discovered flaw.
“Fortunately, since IOTA discourages the reuse of addresses it is uncommon for there to be any funds left on the address,” the researcher clarifies. “The replay attack is only applicable where addresses has [sic] been reused.”
“However it should not be confused with the signature reuse issue, which is only a theoretical concern for a single reuse,” Rebstock continues. “The replay attack applies with only one reuse and is easy to implement.”
The good thing, the author highlights, is that the glitch is relatively easy to eliminate.
IOTA developer Lewis Freiberg has since confirmed the issue is indeed authentic in a statement on Reddit. Still, the developer downplayed the severity of the vulnerability, adding that the company has no intention of tweaking the core architecture of the network to “accommodate this edge case.”
“If the user in the example scenario above had [refrained from reusing their wallet address,] then all of the IOTA from that address would have been sent else where,” Freiberg says. “Thus the attack would’ve never worked.”
In any case, the decision not to patch the exploit is odd – especially because both Rebstock and Freiberg agree it is a pretty “simple fix.”
(Clarification: Following the publication of this piece, Freiberg has pointed out that his response on Reddit does not suggest whether the vulnerability detailed by Rebstock is indeed a “simple fix.” It merely clarifies that IOTA has no immediate plans of patching it.)
One important outtake the researcher emphasizes is that missing to provide a solution to “such an obvious problem should give everyone involved with IOTA [a] pause and hopefully a bit more humility.”
Rebstock also remarks that the current setup of IOTA requires every transaction approval to go through the network’s coordinator – an implementation that many have argued ultimately renders the Tangle a centralized system.
While the IOTA team has conceded this is currently the case, it has promised to get rid of the coordinator in the future. However, the company has yet to lay out its plan for phasing out the coordinator.
Meanwhile, the cryptocurrency startup has remained focused on raising awareness of its technology and expanding its network of collaborators.
The company recently announced its Ecosystem platform which aims to offer developers, startups, and hobbyists with a powerful set of tools to build for IOTA. In addition to this, IOTA signed a memorandum of understanding with Taipei to make the city smarter and secured a substantiative investment from Robert Bosch Venture Capital.
These developments follow the launch of the IOTA Data Marketplace in collaboration with high-profile brands like Accenture, Fujitsu, and Bosch. The announcement attracted fair amount of controversy when it later became clear that Microsoft – which was purportedly in “partnership” with IOTA – is not an official partner, but merely a technology provider.
IOTA later argued the miscommunication came about as a result of an inaccurate statement (provided by Microsoft) in its Data Marketplace announcement.
The vulnerability marks another time IOTA has received criticism over the design of its network architecture. The company previously came under scrutiny for “rolling its own” hash function – a cardinal offence in the world of cryptography.
While some other cryptocurrencies like ZCash have engaged in similar practices, what made IOTA’s hash function problematic is that it purportedly did not undergo rigorous testing.
IOTA eventually addressed these issues in a four-segment response published on its blog – though many known figures in the blockchain and cryptocurrency space ultimately disagreed with IOTA’s line of defence.
In the meantime, those interested can peruse Rebstock’s full report on GitHub here.
We reached out to IOTA co-founders Dominik Schiener and David Sønstebø for a comment on the vulnerability. Schiener has since responded to TNW with the following statement:
“There is no vulnerability. Make that the headline.”
Update: Moments after this piece went up, Sønstebø contacted TNW to second Schiener’s words.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




