
Operational security (OpSec) is only as effective as the idiot behind the keyboard. Strong passwords are meaningless when left on Post-it notes; encryption is ineffective when you don’t keep your laptop locked while unattended; and even the strongest deadbolt on the planet can’t protect a door left open.
With cryptocurrency, this presents a problem.
Many early adopters believed Bitcoin provided a wall of privacy when conducting illicit transactions. It’s partially true. Cryptocurrency transactions are, generally, more difficult to track than online fiat currency movement. But bitcoin was never meant to be anonymous; each transaction is recorded and permanently stored for all to see. And while the ledger entries don’t reveal the parties involved, the users themselves often do.
A recently published study by Qatar University and Hamad Bin Khalifa University revealed just how easy it is to unmask the users behind these transactions. Qatar University researcher Husam Al Jawaheri told Wired’s Andy Greenberg:
The retroactive operation security of bitcoin is low. When things are recorded in the blockchain, you can go back in history and reveal this information, to break the anonymity of users.
According to the study, lifting the veil of anonymity isn’t as difficult as you might imagine. Unlike the network investigative technique used by the FBI to ensnare online pedophiles in 2015, the new study didn’t rely on fancy exploits meant to break anonymity over the TOR network. This method required nothing more than a wallet address and some Googling.
Well, more or less.
Researchers crawled 1,500 hidden services (.onion sites) and collected 88 unique bitcoin addresses. They then crawled some five billion tweets and one million BitcoinTalk forum pages to collect an additional 4,200 and 41,000 (respectively) wallet IDs. Each of the collected addresses linked to Twitter and BitcoinTalk contained identifying information. And while this information isn’t always correct, it’s another digital breadcrumb left for investigators when they come calling.
For some, no further investigation was needed. The online identities were often linked to real email addresses, other social media accounts, and sometimes even a home address.
This is where OpSec goes to die.
BitcoinTalk, in particular, is a problematic site for users who intend to keep their information private. A 2016 Reddit post revealed the forum had recently sent users messages notifying them that some or all of their private messages had been turned over to authorities as part of an ongoing investigation.
It’s also been hacked at least twice since 2013. Both hacks resulted in user information being sold on the dark web.
Using this data, researchers were able to link 125 unique users to 20 Tor hidden services. And while some were completely legal transactions — like donating to WikiLeaks, for example — others made direct connections to illicit transactions on sites like Silk Road.
It’s not rocket science.
Oh my god I hope it’s me… you guys are awesome ?
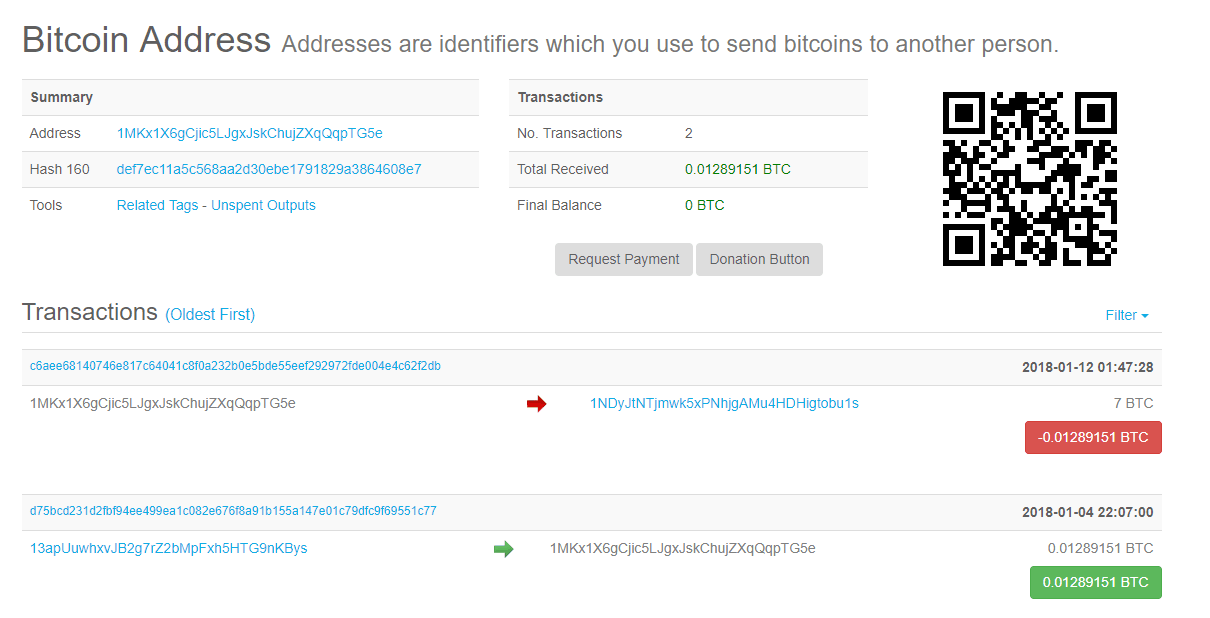
Here’s my Bitcoin Wallet Address – 1MKx1X6gCjic5LJgxJskChujZXqQqpTG5e pic.twitter.com/bk4bNptrOm
— Daniel Mac Sweeney (@Daftplanet) January 14, 2018
In all of 30 seconds we were able to find a random wallet address and pull up a complete history of its transactions. In total, Daniel has used his wallet twice since its creation earlier this year.
We don’t know Daniel and we’re not suggesting he’s buying shady goods from dark web marketplaces; he just happened to be the first wallet address we found on Twitter. But if either of these transactions matched the wallet of a dark web drug dealer, Daniel could have just created the probable cause needed to search his home, monitor his incoming mail, or track his movements.
Bitcoin’s defining feature might also be its most overlooked.
The permanence and immutability of the bockchain means all it takes is a single arrest to create a spiderweb connecting suppliers with dealers and dealers with users. And while it’s not foolproof for law enforcement, digital footprints are easy to cross-reference with pricing information on archived versions of long-dead online drug marketplaces, wallet addresses shared on the clear web, and the users buying and selling illegal items.
The information is publicly available and easily traceable.
As Bitcoin’s 2008 whitepaper stated:
We define an electronic coin as a chain of digital signatures. Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. A payee can verify the signatures to verify the chain of ownership.
Those magic mushrooms you bought for Coachella a few years back? It’s only a matter of time before law enforcement links you to the purchase. For many, these are one-off purchase and probably won’t lead to much, if any interest from the authorities. Others won’t be so lucky.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




