
It turns out that scooping a juicy bug bounty reward from Google is as easy as tampering with its host header – or at least this is what one crafty Uruguayan highschooler with cybersecurity ambitions did to pull it off.
The Big G has rewarded Ezequiel Pereira with a $10,000 bug bounty after the independent security researcher came across a vulnerability that allowed coaxing one of the company’s back-end servers into granting attackers access to confidential data.
Aimlessly toying around with some Google services, the resourceful highschool researcher discovered that using popular vulnerability scanner Burp Suite to modify the host header made it possible to enter some internal App Engine applications – *.googleplex.com to be exact.
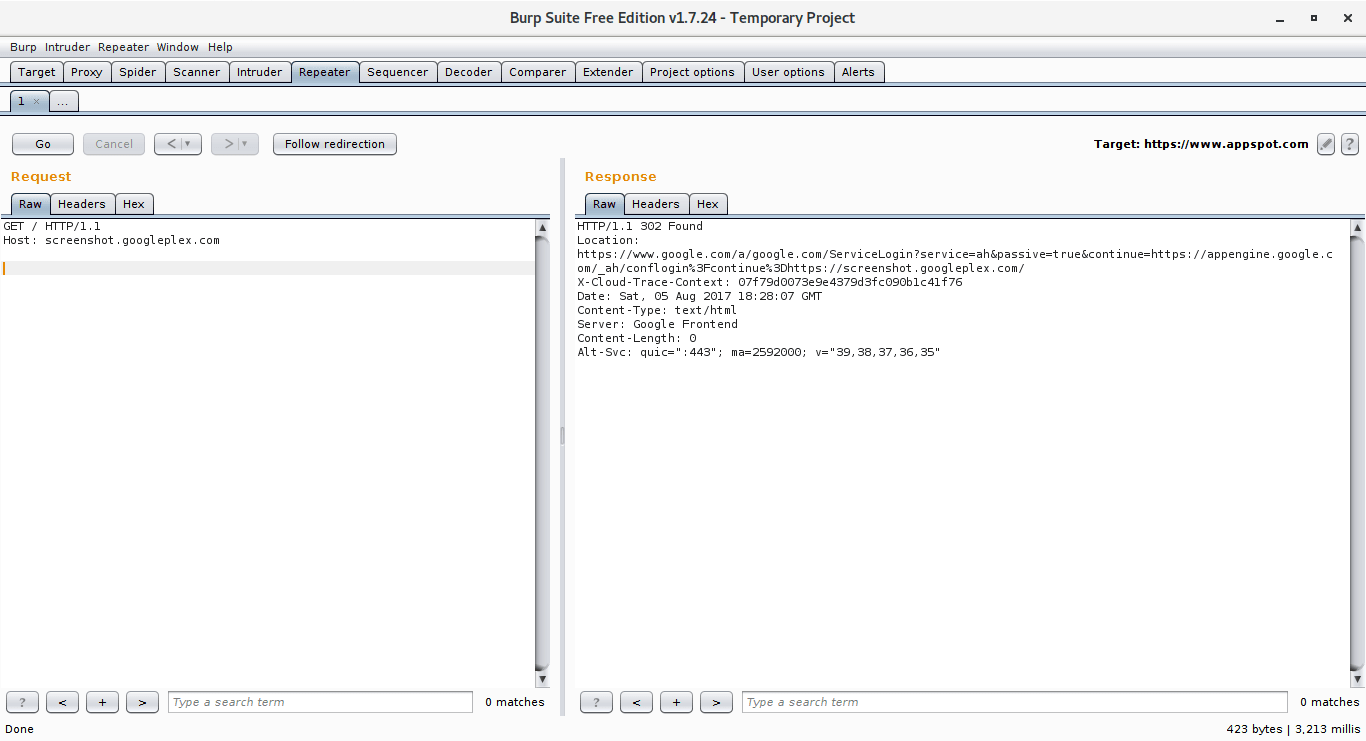
What tipped Pereira off that something might be wrong was that, unlike other Google servers he tried, one of the websites’ security measures weren’t properly set up. This allowed him to connect to the website (yaqs.googleplex.com) without having his username or account checked.
Once he was in, the homepage redirected him to a page that contained numerous links to various Google services and infrastructures. But more intriguingly: The footer read “Google Confidential.”
This is when the young researcher decided to quit poking around the website and report the issue right away:
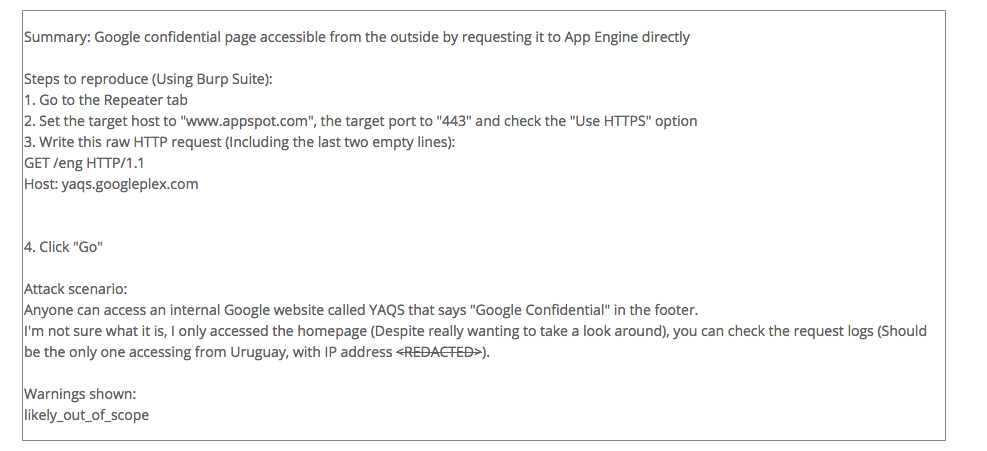
He reported the bug on July 11 and promptly received a response from Google, informing him its security team will circle back to him once it has had a chance to asses the severity of the vulnerability. He eventually received the $10,000 bounty on August 4.
The search engine giant has refrained from telling the high school student precisely what information the website contained. But its cybersecurity team remarked that the large bug bounty was rewarded because the researchers found some variants of the same vulnerability that could have put sensitive data at risk – data that could’ve cost Google millions of dollars.
Google has since eliminated the issue, according to Pereira.
The highschooler has documented in more detail the steps he took to breach Google’s network in a blog post.
For those inspired by Pereira’s brilliant work: One thing to keep in mind is that seeking and disclosing vulnerabilities ought to be done in a responsible manner – so make sure to peruse the criteria for the Google Vulnerability Report Program here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





