In the social media era it’s extremely easy to assume a false identity by signing up for a service, making up a name and uploading a photo of random person off the Web.
Phone number verification is a measure that can be applied to any service or application to achieve an extra layer of security. It works by sending a one-time password (OTP) over a separate communication channel (SMS or voice), versus the IP channel (Internet) used by the application. The user then has to input the temporary password into the application to verify their identity.
Using this channel provides security in case the IP channel is compromised. Phone number verification is often used as a form of two-factor authentication – with the password being something the user knows and the phone being something the user has.
The importance of phone number verification shouldn’t be understated. This method can help prevent spam attacks by bots, fraud and account takeovers, and identify unreachable users due to stale or incorrect information.
Here are several use cases where phone number verification can be implemented:
User login
Confirming the identity of the user is important upon login to help prevent criminal attacks, data breaches and account takeovers for malicious activities.
Phone number verification can be implemented upon initial login or sign up to the service and when a user logs in from a new location, device or IP address to prevent fraud. Opt-in phone number verification during login can also be done if the user prefers to do this every single time they log-in.
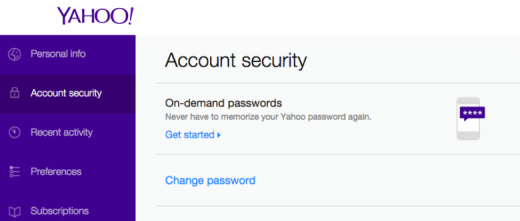
Services like online banking and email offer this extra layer of security. Yahoo now also offers password-free login by sending users on-demand passwords via SMS the moment they need access.
Password reset
Certain account recovery passwords have answers that can be found by doing some online research about the user, e.g. date of birth or hometown. Having a phone number verification step to halt the password reset process can stop hackers from easily taking over a user’s account.
This is particularly crucial in light of recent security breaches which require users to change their passwords. Twitch prompted all users to reset their passwords, while Slack added two-factor authentication.
Authenticating important account activity
It is important to add another authentication layer when a user makes changes to their account that will have a significant impact. This includes upgrades, account changes, refunds and purchases.
Authenticating upgrades and account changes can be useful for services that have more than one user because it can notify the paying user that account details are being changed. Authenticating unusual transactions will also help prevent fraud.
Call center efficiency
Instead of directing a user to a call center to verify their identity in order to activate a certain product, e.g. debit or credit card, mobile phone authentication can be used.
For banks that need a user to verify their card before using it with Apple Pay, those who opted for call center verification experienced friction and a subpar user experience. Phone number verification can speed up the process and reduce call center requirements.
Email verification, setting a password and account recovery questions are alternatives to phone number verification as these are also globally accessible and relatively inexpensive. However, these options are not as secure for reasons stated above.
Using email verification only
Emails are easily procurable for creating fake accounts in bulk use for spamming. A single user is able to create hundreds of free email accounts in a short span of time and use these to verify multiple accounts in the application. These hundreds of accounts can then be used for spam or fraud which will then create a very negative user experience.
Several online dating sites use email verification only, and as a result harbor a lot of spammers. This in turn causes the user to abandon the service after not finding any genuine users.
Dates of Asia started out by using an email verification system to reduce spam on the service as it was causing user abandonment. However, it wasn’t effective as email addresses were easy to spoof.
Using an SMS verification system eventually prevented new spam registrations and allowed the site to achieve a 94 percent global user conversion rate. SMS verification is also more secure than email verification because SMS uses an out-of-band (not using the same channel as the application) connection.
Using password only
Previously, passwords were stolen by phishing. This involves sending a user an email that appears to be from a service that the user is subscribed, tricking them into revealing personal information.
In the last few years, finding out one’s username/password combination has become more sophisticated. Attackers use an automated tool called an “account checker” to test different username and password combinations on e-commerce sites.
If a username/password combination works, they then steal the account holder’s names, addresses and payment card information from these sites.
Fraudsters can also gain username and password combinations using keyloggers, programs which record each keystroke made by a computer user. Last year, Germany’s Federal Office for Online Security (BSI) issued a warning that cybercriminals had gotten hold of a list of 16 million email addresses and passwords. Although it isn’t confirmed how this information was obtained, it is speculated that keyloggers were involved.
Furthermore, many consumers use the same username and password combination for several services. This gives a fraudster access to a variety of services that they can hack once they have the username/password combination.
Since “account checker” and “keylogger” attacks eliminate the need for phishing, are straightforward to carry out and deliver results, they probably won’t stop anytime soon.
Therefore, e-commerce sites need to add another layer of security to these accounts. Having phone number verification as an addition to password can greatly reduce the success of these attacks.
Using account recovery questions only
Account recovery questions are insecure as they can at times be either too complex for the user to remember or too easy to guess. Sometimes the answers are also case-sensitive which is harder for a genuine user to remember.
When Sarah Palin’s Yahoo email was hacked in 2008, the hacker claimed it was relatively easy due to the information available on the Web. A reset password request was made and the details required to do so were Palin’s birthdate, ZIP code and answer to where she met her spouse.
Since a simple Google search revealed that she met her spouse in Wasilla High, anyone could effectively have performed the hack. This shows that account recovery questions in isolation are insecure.
Yahoo now allows the option for phone number verification, alternate email verification or account recovery questions to reset a password.
In summary, phone number verification is a good security measure that has a variety of applications. More importantly, it can be used to replace or complement more traditional forms of security such as email verification, password and account recovery questions.
Read next: Phone numbers as unique user identity: Are you ready?
Image credit: nevenm/Shutterstock
Get the TNW newsletter
Get the most important tech news in your inbox each week.