In the digital age of online banking, dating and brand building, your domain is quite literally the “main” show. It holds the information to whatever goods, services, thoughts – or even just pictures of cats – you’re pedaling these days. Your domain, and its connected social media profiles, is now a part of your identity.
A threat to your domain is not just a cyber security issue; it is a potentially terrifying theft of existence.
So, when a threatening stone is tossed at your digital castle, the defense must be strong enough withstand the barrage. When the attack comes with a ransom note to take your other owned online domains, such as a Twitter handle, it hits swift and from a multiple channels.
Josh Larson, Web developer at Happy Medium, has learned a thing or two about domain security when managing interactive Web design and SEO for a wide portfolio of business clients. He shared his knowledge on different security measures he’s seen and heard of across the industry.
“The first step in domain security is to keep a record of when your domains are up for renewal and keep the account information handy,” Larson suggested.
Newsworthy nuisance
Domain security is essential, not only for private information, but to protect the property on the Internet you put your name behind. For high-profile hacks the targets are global businesses, sought-after domains and social media handles, and heavy trafficked sites.
Larson referenced the recent attack on Shop Talk Show host, Chris Coyier. In a Twitter conversation with the hacker, who goes by pseudonym Earl Drudge, he tells Coyier he is going to “hax” him. The hacker gained access to the Media Temple-hosted domain through personal info obtained online and an image of a Photoshopped faux US passport. In a special podcast Drudge reveals he targeted Coyier’s domain, CSS-tricks.com, for an attack due to its high traffic.
The hacker’s intention? To reveal Media Temple doesn’t verify identification… and for the money and attention.
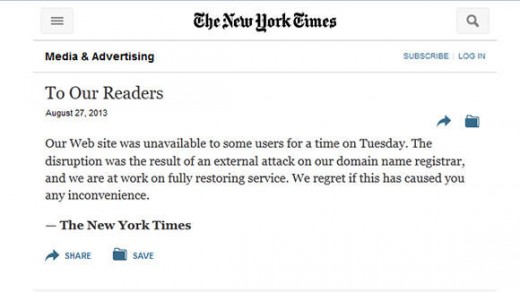
Then there’s the New York Times’ DNS hack in August 2013 where the site’s records were changed so visitors were targeted and pointed to a Syrian website. The attack was executed through domain name registrar, Melbourne IT.
The infamous Twitter hack of the handle @N also drew attention to GoDaddy’s security holes in Naoki Hiroshima’s harrowing tale. He did finally regain control of the account after it was passed around to multiple handlers.
X marks the spot
Just because you’re not a global news outlet or a thought leader, it doesn’t leave you immune to domain hacks.
“Higher profile sites are definitely at the most risk, but I could also see mom and pop shops’ sites that haven’t been updated since 2007 fall under risk because they’re easy targets,” Larson said.
People who threaten the original guarantee made with your domain registrar or hosting company do so for a variety of reasons. With personally targeted domains, the hacker is usually an extortionist looking to be paid off in exchange for keeping the domain.
“Social engineering hacks are where the attacker will call whatever registrar or hosting company it is and they will say they’re an employee or they are the account holder; they trick the person on the other end to thinking they are legit,” Larson said. ”It’s hard for the company on the other line to detect through the phone, so it’s not so much technical hacking, it’s social.”
Think about it. A person, pretending to be you, calls to a customer service center and speaks with a person who doesn’t know you, nor has ever spoken to you. If the hacker can gain access to the account they can change the personal information affiliated with the account.
Try to change the email, phone and password back and you look like the fraud. Your domain has disappeared under a blanket of spammy, flashy ads making you look like the charlatan.
This is a more personal, extreme way of being hacked beyond more common DDoS attacks, stolen credit card numbers or installed cryptocurrency miners.
Sharpen the armor
By now, you likely already have a domain registered, but optimally you would initiate the alarms from the start. Go through these steps to check off the security boxes surrounding your digital self.
Larson suggests doing business with a domain company host that has two-factor authentication (2FA) and good track record.
The security measure basically gives you a second opportunity to verify your identity via email, text or SMS with a generated code. 2FA tops the trends right now for account security. Case in point, social blogging site Tumblr recently turned on the extra security level as an option for users.
“When you think you’re secure because of a social security number or credit card number is on the account, you’re wrong,” Larson said. “It’s incredibly easy to buy social security numbers off illicit sites.”
Before your register or transfer your domain check twofactorauth.org to see which domain registrars and hosts offer two factor authorization. If your current domain company doesn’t you can tell them to support 2FA through Twitter with just the click of a button. The site is also open sourced, so you can add to the list.
For the fullest circle of protection check the site for all 2FA in all areas of the Internet including backup, cryptocurrencies and gaming.
“Make sure to use a secure email address, like a @gmail.com one, for logins instead of a custom domain email address,” Larson added.
The protective layers of a Gmail address mean that if your domain is compromised, the hacker cannot use the custom email address to hack other digital elements of your identity.
If you’ve felt the sharp prong of a hack before or think your sought-after domain name is at elevated risk, go through the extra steps of setting a registry lock in place. Do this after you’re at a good spot with a secure registrar. Registry locks mean that even small changes to the account require multitudinous extra steps to execute.
Hold your ground
If you think you’re being threatened, you’ll usually first receive an email from the registration company stating that your password has been changed. If you end up being threatened by a hacker to hand over money or information don’t immediately act and do whatever is asked.
“The thing you don’t want to do is cooperate with them,” Larson recommended. “First call the DNS or hosting company and tell them what happened. Give the account information you kept on file, then contact the authorities.”
A few simple steps and you’re on your way to a more secure digital identity.
Get the TNW newsletter
Get the most important tech news in your inbox each week.