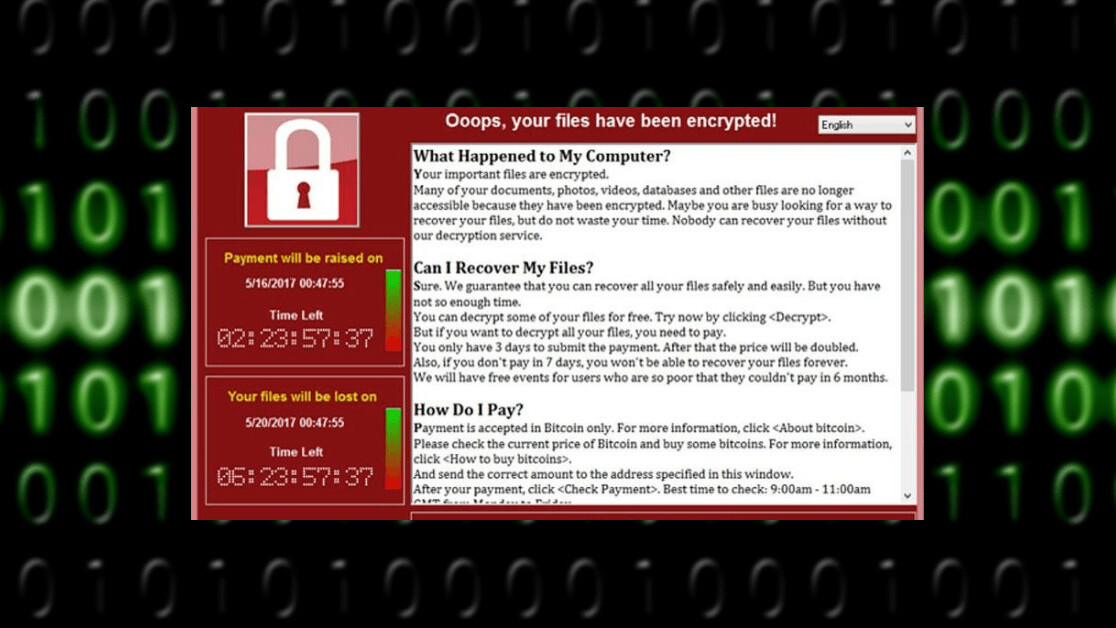
One year ago, my phone lit up with the first text alert about the WannaCry ransomware attack. From the onset, it was clear this attack was major and that it was moving across the world at an unprecedented speed. Over four days, WannaCry inflicted billions of dollars of damages and infected more than 300,000 machines.
Once my team and I handled the acute issues for our customers, our threat research team studied the differences between WannaCry and other major global incidents.
The dawn of a new cyberattack era
We determined that WannaCry was fundamentally different, signaling the dawn of a new, fifth generation of cyberattacks — or, “Gen V attacks.” The most prominent and successful examples of these attacks were created using leaked state-sponsored technology. WannaCry was powered by an exploit originally created by the United States National Security Administration and was released in stealth many weeks before the May 12, 2017 outbreak.
Gen V attacks result in exponentially more damaging financial and reputational losses compared to Gen IV (e.g. Target’s 2013 breach) and Gen III (e.g. the ILOVEYOU virus in 2000) attacks. Another defining characteristic of Gen V attacks is that they are multi-vector. WannaCry proliferated not just through the usual personal computers, but also via other IT infrastructure elements such as remote office servers, cloud networks, traditional network endpoints, and mobile devices.
Further adding to the complexity, some hackers created variants of WannaCry to earn Bitcoin ransoms, while others focused on creating chaos by targeting medical devices in hospitals last June, or most recently at Boeing and the city of Atlanta.
Why companies are unprepared for Gen V attacks
Following the anniversary of the WannaCry outbreak and to determine how security infrastructures have improved, we conducted an industry study to gauge security and IT professionals’ opinions on Gen V attacks and their levels of preparedness to defend against them.
The results were concerning.
More than three in four CISOs (77 percent) said they don’t believe they are equipped to handle Gen V attacks. The study also found that the biggest internal barriers to achieving higher levels of security are staffing challenges and security technologies that conflict with the business or user experience.
Most unsettling about these findings is that companies are actually less well-prepared than CISOs believe. When we surveyed the type of security technologies that companies deploy, we found only three percent are using threat prevention solutions that can successfully prevent a business from falling victim to a Gen V attack. Nearly four in five organizations (79 percent) are using security solutions built for Gen II or Gen III attacks — despite what is clearly a Gen V-level global cyberthreat environment.
To achieve the highest security level, organizations must integrate and unify security infrastructures so they operate better together, sharing threat data across all entry points in real time. This means evolving from a layered, componentized security approach to one that is more holistic — what some call a complete security architecture.
Prioritizing spending for modern warfare
Countries and their infrastructures are being attacked every day, as we’ve seen with recent reports on alleged attacks on the U.S. power grids. At the same time, billions of dollars are being stolen or extorted in attacks on Bitcoin exchanges, ransomware attacks and high-level corporate phishing.
Regardless of the organizations or motivations behind attacks, our critical infrastructure, personal assets, and business assets are at serious risk of becoming collateral damage. It does not really matter who launches an attack or why — countries and global business communities simply need to defend themselves better — because the large-scale, multi-vector nature of these attacks are several generations beyond the average enterprise’s security capabilities. The reality is we’re spending trillions globally on military defense technologies, but investing only a fraction of that on defending businesses and infrastructure against cyberattacks.
We need to get the basics right, segmenting networks to quarantine attacks and stopping them from propagating. We also need to deploy advanced real-time threat prevention that stops attacks before they can get a foothold on networks. This needs to be unified across all environments — networks, cloud, and mobile — to deliver effective cyberattack prevention.
Working together as a global security community
Beyond increasing investment to protect digital assets, a critical factor in the fight against Gen V attacks is the need to educate and remove the barriers that currently inhibit small businesses and large global corporations from implementing Gen V-level cyber protection. As evidence that we are at an inflection point, the World Economic Forum recently cited cyberattacks and data fraud as two of the top five global risks in terms of likelihood (the other three are related to human effect on climate).
Because cyberattacks have become the modern weapon of choice for crippling critical infrastructure, we must work together as a global cybersecurity community to not only protect individual organizations but also to create a shared vision around protecting cities, nations, and the citizens within them. Without a concerted, collaborative effort, we can expect nations, communities, and our most trusted companies to continue to be woefully unprotected against the next mega cyberattack.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




