Update: “We take user privacy very seriously and are actively investigating this report,” Apple spokeswoman Natalie Kerris told Recode.
Update 2: On September 2, Apple said that the celebrity photo breaches were a targeted attack unrelated to iCloud, but did not address the vulnerability discussed here.
_____________
An alleged breach in Apple’s iCloud service may be to blame for countless leaks of private celebrity photos this week.
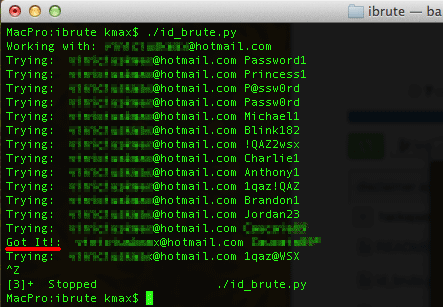
On Monday, a Python script emerged on GitHub (which we’re not linking to as there is evidence a fix by Apple is not fully rolled out) that appears to have allowed malicious users to ‘brute force’ a target account’s password on Apple’s iCloud, thanks to a vulnerability in the Find My iPhone service. Brute-force attacks consist of using a malicious script to repeatedly guess passwords in an attempt to discover the correct one.
The vulnerability allegedly discovered in the Find My iPhone service appears to have let attackers use this method to guess passwords repeatedly without any sort of lockout or alert to the target. Once the password has been eventually matched, the attacker can then use it to access other iCloud functions freely.
Users on Twitter were able to use the tool from GitHub — which was published for two days before being shared to Hacker News — to access their own accounts before it seems Apple patched the hole today. The owner of the tool noticed it was patched at 3:20am PT.
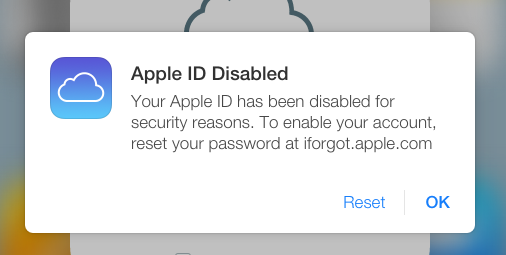
When we tested the tool, it locked out our accounts after five attempts, meaning that the Python script certainly tries to attack the service but Apple has patched the hole.
We discussed the tool with its creator, Hackapp, over Twitter, who said “this bug is common for all services which have many authentication interfaces” and that with “basic knowledge of sniffing and reversing techniques” it is “trivial” to uncover them. When asked if the method could have been used in the celebrity hack today, Hackapp said “I’ve not seen any evidence yet, but I admit that someone could use this tool.”
Hackapp also posted a slideshow that details the tool, why it was created and identifies other problems in iCloud keychain’s security. We’re not able to verify all the claims in the slideshow, but the creator points out the flaws we mentioned in the slide below.
It’s unclear how long this hole was open, leaving those with simple, guessable passwords easily attacked once hackers had an email address to target. There is still no concrete evidence that these images were leaked via iCloud and may have instead been obtained via multiple attacks, though the hacker that originally leaked the images claims that they were retrieved from iCloud.
A similar kind of attack has occurred before. Hackers have previously used Find My iPhone to hold victims ransom, locking their phones and demanding money in exchange for giving their phone back.
We’ve contacted Apple for comment but have yet to receive a reply. Meanwhile, The Independent reported that Apple has “refused to comment” on any security flaw in iCloud today.
Read next: Do you know where your photos are?
Image credit: Justin Sullivan/Getty Images
Get the TNW newsletter
Get the most important tech news in your inbox each week.