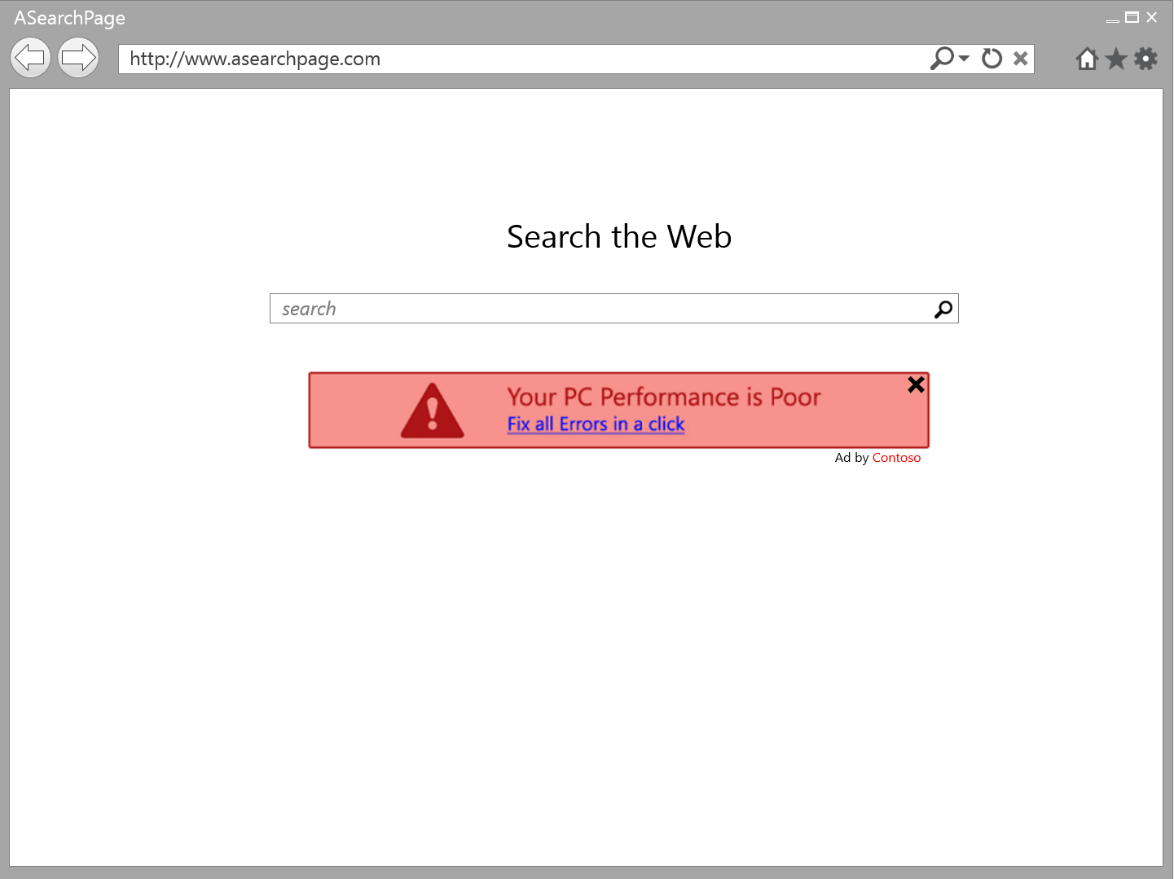
Microsoft today announced a change to how it handles adware, a form of malware that pushes unwanted advertisements to the user. As of July 1, the company’s security products will immediately stop any adware they detect and notify the user, who can then restore the program if they wish.
Currently, when any of Microsoft’s security products (including Microsoft Security Essentials and Microsoft Forefront) detects a program as adware, it will alert the user and offer them a recommended action. If the user doesn’t do anything, the security product will let the program continue to run until the user makes a decision.
The reason Microsoft has chosen a “July 1, 2014” deadline is because it wants to give developers three months to comply with its new rules. Here’s how the company defines adware:
We only consider classifying a program as adware if it runs on the user’s machine and produces notifications promoting goods or services in programs other than itself. If the program shows advertisements within its own borders it will not be assessed any further.
Many programs use advertising as a form of payment for the program and that is also an acceptable practice. We are more concerned with the advertising that interferes with our customer’s Windows experience without giving them choice and control over it.
More specifically, the advertisements that are opened by these programs must include an obvious way to close the ad as well as the name of the program that created the ad. At the same time, the program that creates these advertisements must provide a standard uninstall method for the program using the same name as shown in the ads it produces.
This is a good move on Microsoft’s part, and our sole issue is that it didn’t come sooner. Advertisements are only welcome when they’re useful, and when they’re unwanted and spammy, they simply ruin the overall user experience.
See also – Microsoft extends updates for Windows XP security products until July 14, 2015 and On Patch Tuesday’s 10th birthday, Microsoft awards first $100,000 bounty to security researcher for new exploit
Top Image Credit: AFP/Getty Images
Get the TNW newsletter
Get the most important tech news in your inbox each week.