Symantec today released a 16-page whitepaper (PDF) titled “Ransomware: A Growing Menace.” In it, the security firm released details of the malware type, after studying 16 variants of independently developed ransomware.
One malware family the firm analyzed resulted in some ridiculous data points, and shows exactly why cybercriminals have jumped on the ransomware bandwagon so quickly. By examining the data on the Command & Control (C&C) server, Symantec performed some crude estimates of potential earnings for one such scam:
- This particular variant charged users $200 to “unlock” their PC.
- Over a period of approximately one month of activity, from September to early October, 68,000 unique infected IP addresses were identified connecting to the C&C server.
- In one day, 5,700 unique IP addresses were recorded connecting to the C&C server.
- Out of those, just 168 people (or some 2.9 percent) entered what appeared to be a valid PIN in an attempt to unlock their computer.
- On that day, the criminals may have obtained $33,600. Extrapolating for 2.9 percent of 68,000 unique infections, revenue was approximately $394,000 over the one-month monitored period.
This particular scam required victims to pay their “fines” by purchasing special PINs from vendors such as Moneypak, Paysafecard or Ukash. It’s thus worth noting that the cybercriminals will lose a percentage of what they earn as they attempt to launder the money by converting the payment PINs into cash. Still, it’s easy to see that the scam is very, very profitable, even if only a small number of users fall for it.
In fact, while the $200 charge is on the high-end in this case, Symantec says this particular scam was conducted by “one of the smaller players.” A larger gang used ransomware that attempted to infect 500,000 computers over a period of 18 days. The company concludes:
Given the number of different gangs operating ransomware scams, a conservative estimate is that over five million dollars a year is being extorted from victims. The real number is, however, likely to be much higher.
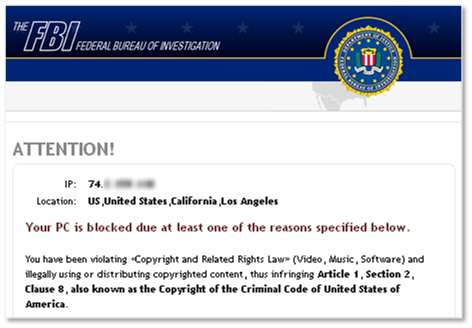
For the uninitiated, ransomware is malware which restricts access to the computer it infects, spamming the user with prompts that demand a ransom paid for functionality to be reinstated. Access is limited either by encryption, as in this case, or locking the system.
Recent variants use law enforcement imagery to make it look as if the warnings are legitimate. Many even leverage geo-location services to determine the location of the infected computer in order to display a message appropriate to that country. Those infected are told they have viewed or downloaded copyrighted or illegal material and must pay a fine in order to have their computer restored. If not, they are told they will be arrested.
In all cases, never pay the ransom. If you don’t know how, have a friend clean out your computer.
See also – Ransomware uses Anonymous name to extort money: Your files are encrypted, pay up to get them back
Image credit: Darren Deans
Get the TNW newsletter
Get the most important tech news in your inbox each week.