The University of Oxford on Monday announced it had temporarily blocked Google Docs on its campus. The Oxford University Computer Services department revealed that the service was being frequently used for illegal activities which threaten the security of the school’s systems and data.
Over the past few years, the university has been fighting phishing attacks that harvest email account credentials, typically used to send out spam. Since university email systems are generally considered reputable by other email providers, online criminals love compromising student and staff accounts.
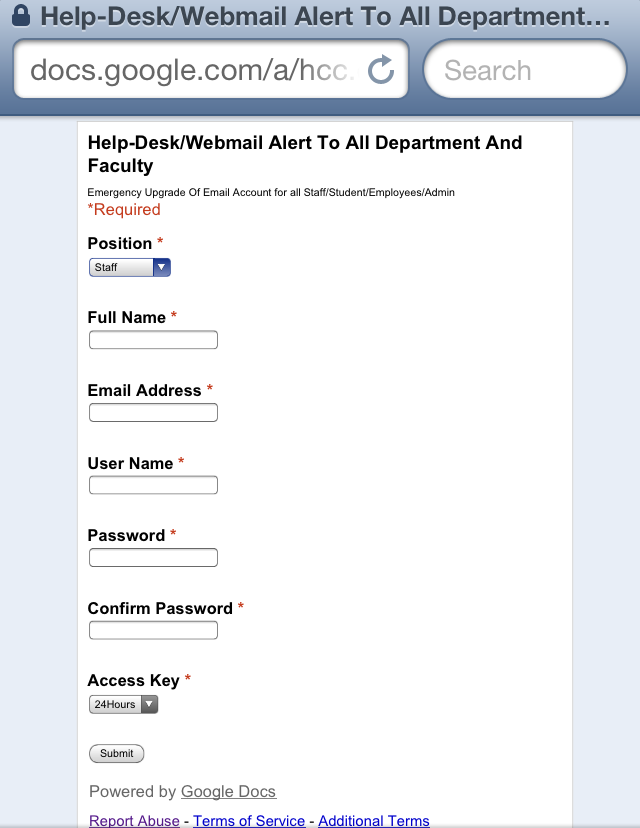
Early phishing attacks would simply ask users for a reply to the phishing email with their details, but current versions have since moved on to Web forms, most of which are hosted on compromised servers or various legitimate free hosting providers. While Oxford has simply been blocking these sites, as most of its users don’t rely on them, recently there has been an increase in criminals leveraging the forms in Google Docs as well.
We’ve seen malware that uses Google Docs as a proxy to phone home, but Oxford says the service is also being used by phishers because it is trusted and traffic is encrypted. The latter means there is a large technical hurdle to overcome:
Many educational establishments will have some capability for filtering traffic to malicious URLs as it flows through their network. That’s easy with unencrypted traffic. If the site uses SSL, then you have to do some kind of SSL interception. Straightforward on a corporate network full of tightly-managed systems. Much harder on a network full of student machines, visitor laptops and the like, and in our opinion, something to be avoided.
Oxford thus has to ask Google to take the form down. Unfortunately, using the “Report abuse” link at the bottom of each page doesn’t immediately solve the problem. Google is slow to take action, however, with reaction times ranging anywhere from a day or two all the way to a few weeks. Given that most users who are likely to visit the phishing form will do so when they first see the email, this isn’t good enough:
Granted, many, if not most of our users do spot the scams, and do nothing (or better, warn us about it). But as with most spam, it only takes a small proportion to respond for the attacks to be worthwhile. And we have tens of thousands of users. Despite all attempts at user education, some will inevitably respond. We see a good mix: first-year “digital native” undergraduates, ancillary staff, emeritus professors.
Oxford says over the past few weeks “there has been a marked increase in phishing activity against our users.” Not only is this bad news for the students and staff that click on the links and fill out the forms, but the compromises and associated spam can adversely impact the university’s “reputation” with other email services such as Gmail, Hotmail, and Yahoo. If one of these services start rejecting emails from Oxford accounts, because a proportion of the mail is being marked as spam, everyone on campus is affected.
Since “almost all the recent attacks” have used Google Docs URLs, the university decided to simply block the service temporarily. After two and a half hours, the restrictions on access to Google Docs were removed because “the impact on legitimate business was greater than anticipated, in part owing to the tight integration of Google Docs into other Google services.” In other words, university students and staff rely on Google Docs to get their work done. Who would have guessed.
The Computer Services department has since apologized for the disruption but insists it must always consider the overall risk to the university as a whole, and thus may take similar action again in the future. In the meantime, it is investigating alternatives to the temporary solution and will be getting in touch with Google:
We will also be pressuring Google that they need to be far more responsive, if not proactive, regarding abuse of their services for criminal activities. Google’s persistent failures to put a halt to criminal abuse of their systems in a timely manner is having severe consequences for us, and for many other institutions. If OxCERT are alerted to criminal abuse of a University website, we would certainly aim to have it taken down within two working hours, if not substantially quicker. Even out of official hours there is a good chance of action being taken.
We have to ask why Google, with the far greater resources available to them, cannot respond better. Indeed much, if not all, of the process could be entirely automated – and part of their corporate culture is that their programmers and sysadmins should be automating common tasks such that they can devote efforts to more interesting matters. Google may not themselves be being evil, but their inaction is making it easier for others to conduct evil activities using Google-provided services.
We have contacted Google about this issue as well. We will update this article if we hear back, but we’re not expecting much since it’s a US holiday.
See also – New malware variant recognizes Windows 8, uses Google Docs as a proxy to phone home and Google releases faster version of Forms with real-time collaboration, automatic saving, and more
Image credit: Balazs Dudas
Get the TNW newsletter
Get the most important tech news in your inbox each week.