Over the last 24 hours the world has been abuzz with talk about a small Firefox extension. Usually Firefox extensions don’t make headlines, but in this case one did. Why? This extension is called Firesheep, and it’s scary.
The Firesheep plugin can hijack your Facebook, Twitter, and Flikr sessions while you are connected to unsecured wifi. What do we mean hijack? We mean that it can steal your sessions, pretend to be you, and you won’t even know it.
Yeah, wow.
There is a lot of discussion about the ramifications of releasing something that is simple enough to let anyone become a hacker, and TUAW has some good suggestions for how to guard against Firesheep, but I want to give you my take on it and what practical steps you can take.
First off I want to tell you about my day yesterday (it relates, trust me). Sitting at home working on articles for this joint, I get a call from one of my friends at the CBC. “Have you heard about Firesheep?” I said I saw some headlines, but I hadn’t really looked at it. “Could you look at it and talk about it on camera?”, umm…sure….when? “How about an hour?” Eek. Sure…why not.
I dash to one of my favourite coffee places close by (which I also knew had open wifi) after getting Firesheep all loaded up (it took less than a minute). I order a latte, settle in and …
Holy crap.
Just like everyone said, running Firesheep I could see who was logged into Facebook and a bunch of other sites and with a double-click be that person.
Holy crap.
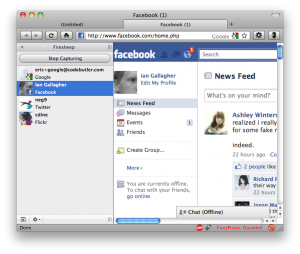 I’m not usually a terribly paranoid person online, but this gave me the willies. Anyone could have this running and you’d never know it. Oh sure, packet sniffers have been around for a while (that’s how it works), but packet sniffing isn’t easy for most people. Firesheep is easy enough for a kid to use. So how do you combat this? Well let’s get to that now…
I’m not usually a terribly paranoid person online, but this gave me the willies. Anyone could have this running and you’d never know it. Oh sure, packet sniffers have been around for a while (that’s how it works), but packet sniffing isn’t easy for most people. Firesheep is easy enough for a kid to use. So how do you combat this? Well let’s get to that now…
First thing, if you have a wireless network at home and you haven’t set up a WPA (or even WEP) password on it, do it now.
Next, for all the businesses that have open wifi, now is the time to bite the bullet and put a password on the network. No, I’m not talking about a “gatekeeper” password that lets you in for a period of time, but WPA/WEP. Encryption. Yes, I know it’s a hassle for people to ask, but just make it obvious. This isn’t about access control, it’s about safety. I showed the manager of the place where the CBC segment was shot what the risk was and he was pretty shocked.
If you frequent a place that has open wifi, ask them to put a password on it. If you lock down your wireless network, then that’s it. Firesheep isn’t a problem. If you’re slightly techie and know how to do this, offer to help. For free.
In the meantime, you can try Firefox extensions like Force-TLS or HTTPS Everywhere or Chrome a extension like KB SSL enforcer all of which force the site you’re on to load the HTTPS (encrypted) version of the site. The problem I ran into with KB SSL today was that a lot of sites don’t have their HTTP and HTTPS versions working together very well. I had to shut it off to read some things…so what does that do? These solutions are only a stop gap as far as I’m concerned.
For those of you lucky enough to have a mobile data stick or can tether your phone for access—both of those are nice and secure. What about your WiFi only mobile devices? Those I don’t have good solutions for. Myself I have both my iPhone and iPad set not to just autoconnect to available networks and I’m going to have them both “forget” several of the local places I go to that don’t have secured wifi. Yes, mobile devices are also vulnerable because this isn’t a vulnerability in a browser or device it’s while how you can the sites connect to each other.
This is what bugs me the most about the whole Firesheep problem. Websites like Facebook and Twitter could force everyone to https like gmail does, but they choose not to. Until now, the risk hasn’t been that huge, but now…now I don’t think they can say that.
From now on, if it’s unsecured WiFi, I’m not using it. Period. If I absolutely have to, then I’ll run a proxy. Yeah, it’s harsh, but even the Firefox and Chrome extensions are only a partial solution. They aren’t 100% and they don’t work with all sites equally well. All you need to do is forget to turn them on or have an application notifier running in the background and …
Done like dinner.
My last tip is for the rather geeky of you who happen to have a web host who lets you have an SSH (shell or terminal) connection (both Dreamhost and Bluehost do) is to use this awesome trick for setting up a secure/encrypted proxy. I use this one all the time, it takes just a moment to set up, but is very, very secure.
If you want to see the entire CBC piece (which gives the right level of urgency I think), the video is up on the CBC site now.
And if you have more suggestions…please let us know in the comments.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




