India’s most populous state, Uttar Pradesh (UP), has more than 350,000 coronavirus cases — with thousands added every day. It’s important for states to monitor those cases, but it’s equally important for them to keep that data safe from attackers. However, UP’s internal COVID-19 platform had multiple bugs that exposed citizens’ data.
A team of security researchers from VPNMentor, Noam Rotem and Ran Locar, found that the state’s internal coronavirus monitoring portal, Surveillance Platform Uttar Pradesh Covid-19, was riddled with bugs that put the personally identifiable data of citizens at risk.
The first bug was in the git repository that stored the platform’s code. The git was unsecured and it also contained visible login credentials of admin accounts. Effectively, it was possible for attackers to log into the platform and see all the private data. On top of this, most generated passwords were just four digits and many admin accounts also shared the same logins.
Attackers could’ve taken control of the dashboard, manipulating case statuses, or modifying patient data. This could’ve caused panic, disrupted the whole testing system, and put a lot of people at risk.
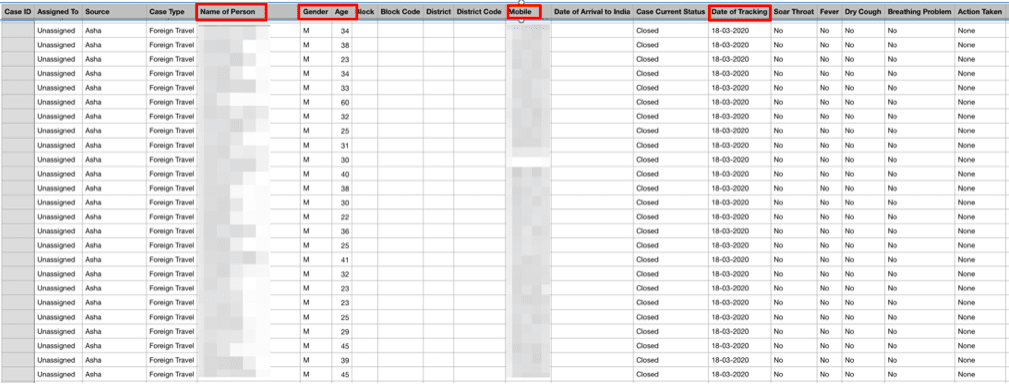
Researchers also found a link to CSV files through exposed web index that contained testing data from not only UP, but other regions of India. This is because the platform also integrated data acquired by India’s central government. These files contained the personally identifiable data of more than 8 million people.. This is because the platform also integrated data acquired by India’s central government.
They included information including names, addresses, tracking dates, and phone numbers along with test results. The platform also kept records of test results of foreign residents in India who tested positive for coronavirus.
The cybersecurity company’s tools detected the breach on August 1 — and researchers had reviewed the data by August 9. The VPNMentor team and TNW contacted UP authorities several times, however, we’ve received no response at the time of publishing. The vulnerabilities were finally plugged on September 10 after the company contacted India’s threat response team, CERT-In.
It’s not clear if any attacker was able to gain access to this data at this point. However, given the scale of the coronavirus pandemic in India, with more than 5.5 million COVID-19 positive cases registered in the country to date, the data is very sensitive and crucial to control the spread of the virus.
UP’s portal development team had to take basic steps of securing the git and conducting audits to make sure that the data of citizens was safe. It appears they did neither of these things.
Did you know we have an online event about digital marketing coming up? Join the Re:Brand track at TNW2020 to explore the latest brand marketing tech, trends, and challenges.
Get the TNW newsletter
Get the most important tech news in your inbox each week.