Yahoo-owned image and video hosting service, Flickr, was suffering from a glaring flaw that made it possible for malicious agents to upload thousands of unwanted pics to the accounts of random, unsuspecting users.
The defect resided in the Flickr’s Upload by email feature, which enables users to upload images straight to the platform by sending emails to a specific address, automatically generated and assigned to users by the hosting company itself.
The vulnerability was discovered by high-schooler and independent security researcher Jazzy, who has since documented the issue at more length over at his blog.
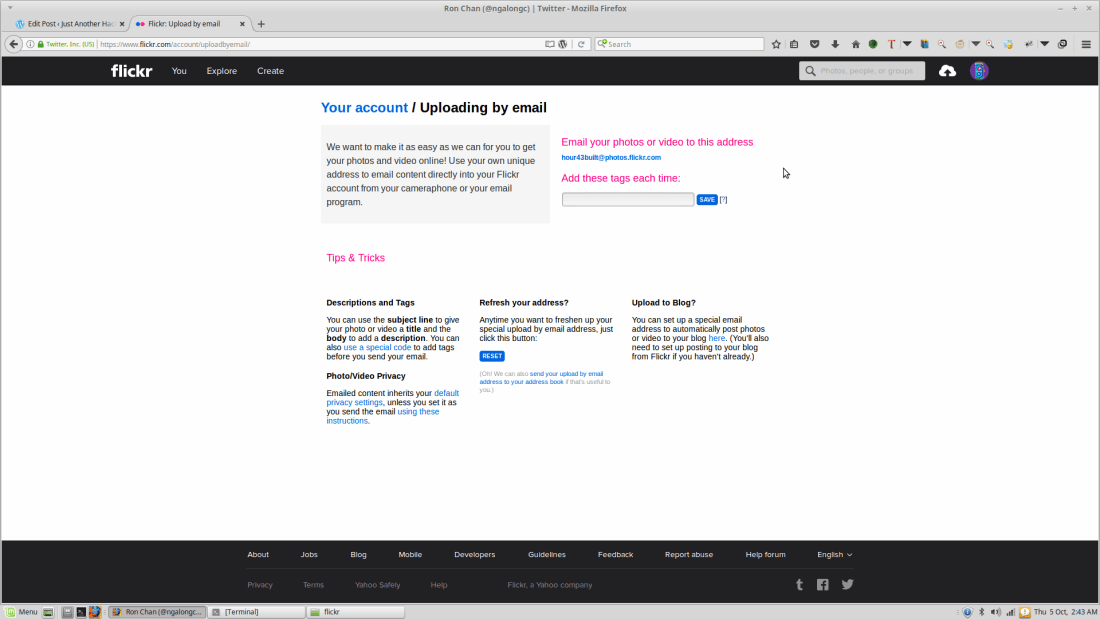
Flickr offers users the option to request a unique email address they can use to upload images to their accounts by mailing them to the address in question. The problem, though, is that anybody who knows the correct address could abuse it to upload images without any user consent.
This prompted Jazzy to dig deeper and seek whether there is a way to extract a long list of Flickr-generated email addresses. While he couldn’t breach the website’s defenses to snatch any email addresses, he noticed there is an option to change his automatically-generated email and get a new one.
After repeating the procedure a few more times, he noticed a pattern. The email returned by Flickr had some well-defined properties – this is the formula it followed:
<Random dictionary word><Random number 0-100><Random Dictionary word>@photos.flickr.com
He further spotted that the length of each dictionary word was always shorter than six characters.
With this in mind, he decided to whip up a quick Python script, which would repeatedly change his Flickr email address and record each new unique address in a log file.
He ran the script overnight, generating more than 20,000 addresses. He then went on to write another script, designed to sort through the emails and show how often each dictionary word appeared. The result was surprising, to say the least.
Out of the 23,692 email addresses amassed, Jazzy discovered that Flickr only used a total of 935 unique words. This meant that, the total amount of permutations the email-naming algorithm could generate close to 87.5 million variations. Flickr only has about 50 million users.

This meant that every randomly generated email address has higher than 50 percent chance of belonging to an actual user. And, according to his own estimates, all it would take to deluge all of Flickr’s 50 million users with tons of images is a short script, some computing power and a couple of hours.
Jazzy has already notified Yahoo of the vulnerability. Its technical team swiftly amended the flaw and has since rewarded the crafty high-schooler with a “nice bounty.” Big up to you, Jazzy, well done.
Correction: This piece incorrectly stated that Flickr generates unique email addresses for each user. While the platform does offer this feature, it is something users need to personally request to receive access to. We have corrected our mistake to reflect this more clearly.
Get the TNW newsletter
Get the most important tech news in your inbox each week.