
“‘Conspiracy to commit computer misuse with intent to disrupt or impair the operation of a computer or computers’,” commenced Jake Davis in front of a packed auditorium at Wired 2013. “This is what I was sent to prison for.”
If that just made you blurt out ‘huh?’, you’re not the only one. “Don’t worry if you didn’t understand that sentence, because neither do I and neither does anyone else in the entire world,” he continued.
Cast your mind back to 2011, when online hackers wreaked havoc across the Internet, bringing down websites on a purported crusade of righteousness. The victims? Everyone from NATO and FBI contractors, to the Iranian government and Syrian Ministry of Defense.
The axe fell on many suspects, in the UK, Italy, Spain, the US, and elsewhere, with a series of police raids throughout the year helping to reel in some of the culprits. One of those was Davis, a teenager from the Shetland Islands – an archipelago that sits off the north-east of Scotland – who had helped form the Anonymous splinter hacktivist group known as LulzSec, while using the Topiary pseudonym.
Twitter was an instrumental tool in communicating with the world.
This is a joint statement from #Anonymous (@AnonymousIRC) and Lulz Security to PayPal (@PayPal) and its customers: http://t.co/4nqeut5
— The Lulz Boat (@LulzSec) July 27, 2011
Davis was collared in July 2011 following a police raid on his Shetland home. He appeared in court a few days later, where prosecutors claimed he possessed 750,000 people’s personal details. Following almost two years on bail, Davis and three LulzSec colleagues were handed jail terms ranging up to 32 months.
Here, Davis tells his story of what happened before, during and after his online hacking exploits were brought to an end.
Idle hands

“I decided to sit in my house on a computer all day, instead of knitting or farming or dressing up as a viking, which is what goes on in the Shetlands,” quipped Davis.
Davis did this for around five years, having dropped out of school when he was just thirteen. And what did he on his computer? Sit on chatrooms and play games for eighteen hours a day. “I was a basement-dwelling, nerd for five years,” he says.
But then, in December 2010, Davis got wind of one particular chatroom, one that was full of so-called ‘hacktivists’. It was a group called Anonymous and, despite some initial reservations, Davis joined the few-hundred strong community, not entirely convinced anything big was happening in there. “I was completely wrong though,” continued Davis.
Around the same time he was familiarizing himself with his new faceless friends, MasterCard, Visa Europe and PayPal (Bank of America joined later) all stopped processing payments for WikiLeaks, in light of the deluge of classified information it had attained and published, much to the US government’s chagrin. So Anonymous announced Operation: Payback, and duly took the financial giants’ websites offline.
“I didn’t expect that to happen, so I stuck around in this chatroom just lurking and cracking jokes initially, but then this progressed to writing,” says Davis. “I ended up accidentally writing deface pages for Libyan, Zimbabwean, and Egyptian government websites in support of the Arab Uprising.”
Things soon escalated – what started as a couple of hundred people grew to around 10,000 in this chatroom. And although Davis considered going back to being a humble gamer, someone then suggested going after the Westboro Baptist Church, an organization known for its extreme beliefs, particularly against gay people. This idea stemmed from Westboro’s public threats leveled against Anonymous.
But not only did they hack their site, they did so live on radio, with Davis the spokesperson for Anonymous. During a live discussion between Davis and a Westboro Baptist Church spokesperson, Anonymous struck, with part of the message reading:
“This domain has been seized by Anonymous under section #14 of the rules of the Internet …For this unremitting display of overzealousness, we award you no points. Take this defacement as a simple warning: go away. The world (including Anonymous) disagrees with your hateful messages, but you have the right to voice them. This does not mean you can jump onto Anonymous for attention…”
The radio exchange is still actually available to listen to on YouTube.
“I expected all that to just go away, but it got something like a million hits in four days,” says Davis. “Everyone in that chatroom now knew who I was, and I started getting paranoid so I decided to leave the Internet forever. This actually worked for about three weeks, before I got bored again and came back. A group of about seven of us decided that the solution to not-being-found for going after the Westboro Baptish Church, was to start our own hacking group.”
The rise of LulzSec
 So the splinter group set up a new Twitter account, with this avatar serving as its brand – you’ll not doubt recognize it: a monocled cartoon man wearing a top hat, supping on a glass of goodness.
So the splinter group set up a new Twitter account, with this avatar serving as its brand – you’ll not doubt recognize it: a monocled cartoon man wearing a top hat, supping on a glass of goodness.
“We ended up going after the X-Factor, putting up a fake article on the PBS website claiming that rappers Tupac and Biggie were alive and well, living New Zealand.”
Things mushroomed from there. The Twitter account gained a few hundred thousand followers, and they started targeting the US Senate and the CIA‘s website, and eventually the serious and organized crime (SOCA) website in the UK.
“Apparently, that didn’t go down too well with the UK government,” says Davis. “The person responsible for taking down that website had his house raided that very same night, while the attack was still ongoing.”
In the wake of this, Davis vowed yet again to leave this shady world behind. But another three weeks passed, and the whole News International phone-hacking scandal kicked off in the summer of 2011.
“(Rupert) Murdoch came out with some statements, claiming he knew nothing about phone-hacking, (and we said) ‘okay, that’s not true’,” says Davis. “Then the Sun’s website was hacked, and replaced with a fake news article claiming that Rupert Murdoch, in the depth of his shame, had killed himself in his garden.”
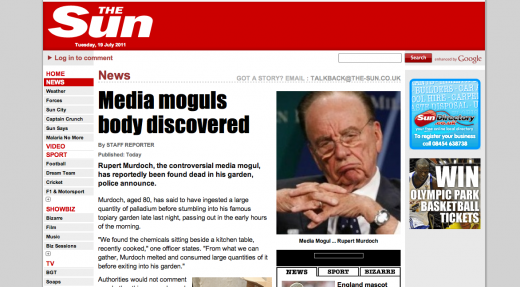
As things panned out, this was the last such ‘act’ Davis ever did online, because a little more than a week later, he received a quiet knock on his front door.
The end of Topiary and LulzSec
“I thought, ‘it could either be my neighbors complaining about my music being too loud, or the local mental health team coming to check if I was okay’,” says Davis. “But it turned out to be six, smart-looking serious individuals forming a semi-circle around my front door. They said ‘Jake Davis?’, I said ‘yes’. They said, ‘We’re arresting you on suspicion of conspiracy to commit DDOS'”, before reading him his rights.
Davis was then bundled back into his house, with the assembly grabbing all his electronics and shoving them into bags, while looking under his bed, in his drawers and everywhere in between. “They even opened my fridge and freezer, and started opening up my food, in case I was hiding micro SD cards in the fish fingers,” he says.
At this juncture, it’s worth remembering that Davis was living on the Shetland Islands, a small territory on the cusp of the North Sea and the Atlantic Ocean. So how were they going to get Davis and all his stuff off the island? As things transpired, the local airport had been commandeered, with Jake frogmarched down the runway with his bags of electronics carted on either side of him, and led onto a four-seat private jet.
“It was me and three of the officers facing each other, one of them was sitting there, casually reading the Godfather, while the other one was talking about how he wanted to improve his life and be better to people,” says Davis. “The third one was sitting there very seriously, not paying attention to the other two, on my computer dumping the RAM and copying the hard drive, giddy that she’d never done this at that altitude before.”
After landing in London, he was led into a black cab, driven to Charing Cross holding cells where, eventually, he applied for bail. This was declined, given that he was categorized as a ‘Tier One’ threat to national security.
For the record, there are three ‘tiers that make up the UK’s National Security Strategy – Tier Three is the lowest threat, and Tier One is the highest. “In Tier Two, I noticed there was a ‘biological attack by an enemy state’,” says Davis. “And in Tier One is organized cyber crime.”
Ultimately, Davis was denied bail because he was deemed to be more dangerous than nuclear warfare.
“At this point, I was thinking ‘but I was just a spokesperson, I didn’t actually hack anything – it was just jokes and tweets,” continues Davis. “And a radio show, of course. Eventually, the magistrate realized this, and let me go the next day.”
Life on bail
There were strict conditions in place, and Davis was ultimately banned from the Internet for two years. He was also banned from asking anyone to use the Internet on his behalf. “So if I said to anyone, ‘check out this cool YouTube video of a cat running around’, this would be a breach of bail and I would be sent to prison,” says Davis.
Davis also wore an electronic tag around his ankle, which was connected to a box in his house, and he had to be home by 10pm every night for the next two years. “I’d moved to a new area of England and I had no idea how to get around,” he says. “I couldn’t legally use Google Maps, and I had to be back in my house by 10pm. That was a strange combination to deal when I didn’t know my way around.”
The following year, as things were progressing towards trial, it transpired that one of his fellow ‘hackers’ was actually working for the FBI, and produced a lot of evidence from America that got shipped over. “So I immediately pleaded guilty, and I was sentenced to two years in Feltham Young Offenders Institution. But because of the time I’d spent on the electronic tag, this minused off around a year. And in the UK, you spend around half your time in prison and half on parole, where I am now.”
As things transpired, Davis actually only spent 37 days in Feltham.
654 days on curfew and 37 days in Feltham. Up next: another 365 days on license (parole) and 1825 days of intense monitoring. Free though!
— Jake Davis (@DoubleJake) June 22, 2013
“The first day I went into prison – and I knew Feltham was basically where a lot of gang members were sent – this rather large man in a tracksuit came right up to me and said something like, “Yo blood, what you in for?” (affecting a rather good London ‘street’ accent’),” says Davis.
“So I said ‘computer hacking’,” he continues. “He looked at me for a second, and this is where I expected everything to go horribly wrong, but he said to me, ‘Oh yeah, you was on that real ting innit blood? You was hackin’ the CIA, the FBI, the MI5, the Illuminati, man…gimme that skin bruv.”
And so they became good friends, playing cards together in their shared cell.
Davis was released from prison in June this year, and is now legally banned from encrypting any files until May 2018. He’s also legally banned from deleting his Internet history until May 2018, and he has to store it all on a USB stick so that anybody from the authorities can plunder the information.
“The most interesting restriction at the moment is that I’m legally banned from communicating with anyone associated to, or formally associated to, Anonymous,” says Davis. “But I guess the whole idea of Anonymous is that everyone is anonymous.”
Given his six-month hacking spree, Davis had one solid piece of advice for those looking to avoid getting hacked themselves.
“I guess what I’ve learned from all this, is that, well, don’t use the same password everywhere,” he says. “That’s my one piece of advice. Fifty percent or seventy percent of the victims made that horrible mistake of using a very small password. There was this one CEO of a company, he used the same password for his World of Warcraft profile as he did his company’s entire financial account. But I won’t name names.”
Real-world security
“But what’s more important is real-world security,” continued Davis, somewhat enigmatically.
Indeed, as part of his preparation of speaking at Wired 2013, Davis had been invited to talk with Wired Editor David Rowan at their London HQ. Upon leaving the meeting, and subsequently the building, Davis then tried something very interesting.
It was raining outside, and the door to the building had locked behind him, but a man was delivering boxes on the inside, so Davis asked the guy if he could let him back in, as he’d ‘accidentally’ walked out without his pass.
“He let me in, there was nobody on the reception desk, so I walked up four floors, waited outside the Wired door which was locked, until someone came out on his phone, and I walked in,” says Davis. “I walked straight into the Wired office, saying ‘I’ve left my umbrella here, can anyone help me find it?’. Everyone was being helpful, to be fair they were busy, but they were helping me look in cupboards, underneath desks…everywhere.”
Davis then walked into David Rowan’s office, who had already vacated, but rather than perusing his personal computers, he took a single shoe from his cupboard, put it in his bag and walked away with it. What better time to give the shoe back to him than at Wired 2013, with hundreds of people looking on? None, if you ask us – and that’s exactly what Davis did to a rapturous applause.
As for what Davis is doing today, well, the 20-year-old confirmed he was working somewhere, but for legal reasons couldn’t elaborate.
“The people I work for won’t let me tell you who I work for – that’s all I can say.”
Image Credits
Image 1 – Brockvicky – Flickr |
Get the TNW newsletter
Get the most important tech news in your inbox each week.





