
GitHub is increasing the security of repositories by requiring all developers to enable two-factor authentication by the end of 2023.
The company’s directive is simple: if you contribute to code, you must enable 2FA.
GitHub is probably pushing this initiative because the number of people using adequate security measures is so low. The company said only 16.5% of active GitHub users and only 6.44% of NPM registry users use 2FA.
Last November, GitHub forced NPM package maintainers to enroll for 2FA to avoid account takeovers. The company is expanding this effort to secure top packages on the service:
“In February we enrolled all maintainers of the top-100 packages on the NPM registry in mandatory 2FA, and in March we enrolled all NPM accounts in enhanced login verification. On May 31, we will be enrolling all maintainers of the top-500 packages in mandatory 2FA.”
Enabling two-factor authentication
While GitHub’s mandatory 2FA rollout will take effect next year, you can enable it right now to increase a project’s security.
The company allows you to use multiple methods for 2FA, including SMS, a time-based one-time password (TOTP) service like 1Password or Authy, and a fingerprint reader like Touch ID on Mac or Windows Hello. GitHub also supports integration with physical security keys like Yubikey.
Here’s how you can enable 2FA on your GitHub account:
- Log in to your GitHub account on the desktop.
- Click on your profile avatar in the top right corner, and then on Settings.
- Go to the Password and Authentication section.
- Click the Enable button under the Two-Factor Authentication section.
- You’ll get a dialog to choose SMS-based authentication or Third-party app-based authentication. You can add the other authentication method later as well.
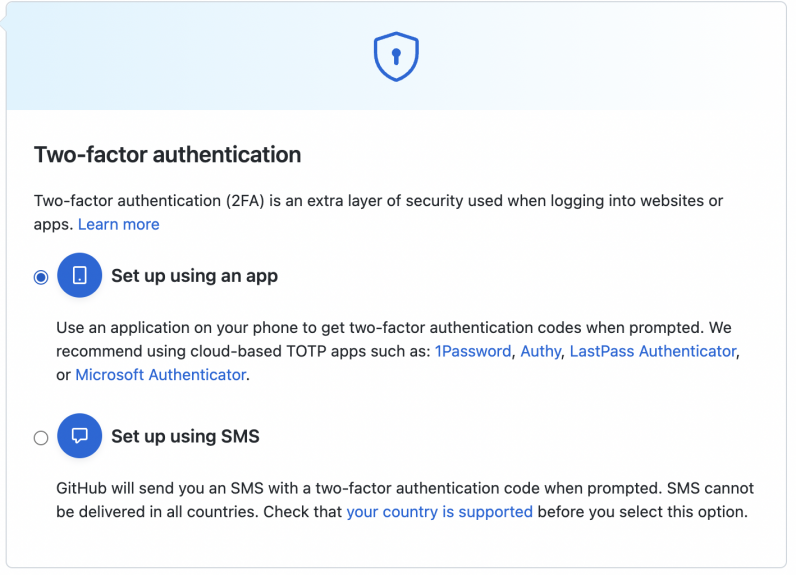
- For SMS-based authentication, you can add your phone number, and receive a code for verification.
- For the app-based authentication, you’ll get a QR code to scan from an app like Authy or Microsoft Authenticator to register the account.
- You’ll get to a screen where GitHub will ask you to save recovery codes.
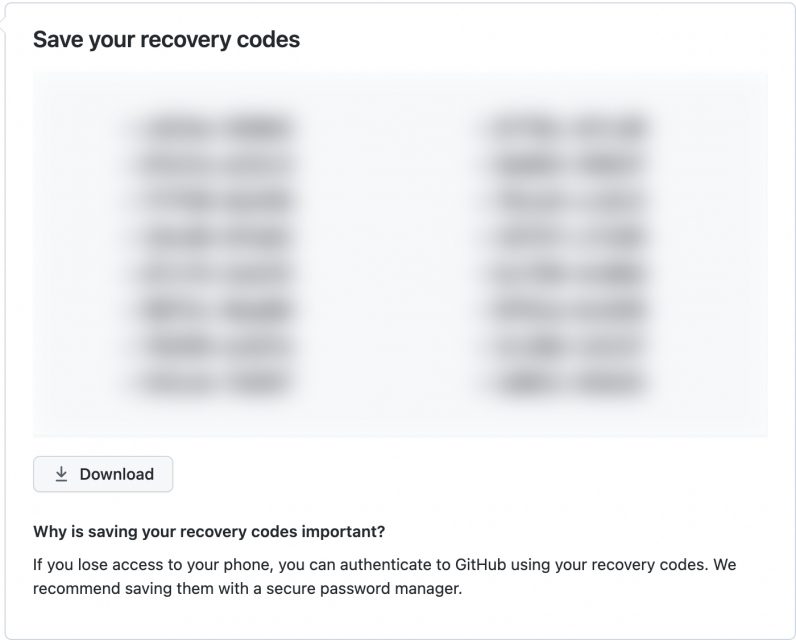
- You can use them to log in to your account if you don’t have access to your phone or other methods of authentication.
Viola, you’re done!
For extra security, you can head back to Password and Authentication > Two-Factor Authentication, and add new methods like Touch ID on your Mac, an Android device, or a physical security key.
Plus, once you enable 2FA, you can use the GitHub mobile app to approve new sign-ins. Watch it in action in the GIF below.
You can read about setting up your security for your account here.
Hopefully, we’ll see an uptick in accounts using 2FA before the mandatory rollout begins. Secure your shit, people.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




