This weekend, Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich took to Twitter to announce they have discovered a “crazy bad” loophole in Microsoft’s built-in Windows anti-malware software package that leaves your system susceptible to remote attacks.
What is particularly scary is that the attack could take place over email – without even reading or opening the full email.
.@natashenka Attack works against a default install, don't need to be on the same LAN, and it's wormable. ?
— Tavis Ormandy (@taviso) May 6, 2017
The security experts proceeded to say they have reported the issue to Microsoft, adding that further details will be revealed once the bug has been eliminated – and it appears the time has finally come.
The Redmont heavyweight today rolled out a fix for the flaw that is now available via Windows Update. As explained in the report, the exploit resided in the Microsoft Malware Protection Engine and allowed attackers to “execute arbitrary code… and take control of the system.”
Here is how Microsoft summed up the backdoor:
An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
To exploit this vulnerability, a specially crafted file must be scanned by an affected version of the Microsoft Malware Protection Engine. There are many ways that an attacker could place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine. For example, an attacker could use a website to deliver a specially crafted file to the victim’s system that is scanned when the website is viewed by the user. An attacker could also deliver a specially crafted file via an email message or in an Instant Messenger message that is scanned when the file is opened. In addition, an attacker could take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server.
If the affected antimalware software has real-time protection turned on, the Microsoft Malware Protection Engine will scan files automatically, leading to exploitation of the vulnerability when the specially crafted file scanned. If real-time scanning is not enabled, the attacker would need to wait until a scheduled scan occurs in order for the vulnerability to be exploited. All systems running an affected version of antimalware software are primarily at risk.
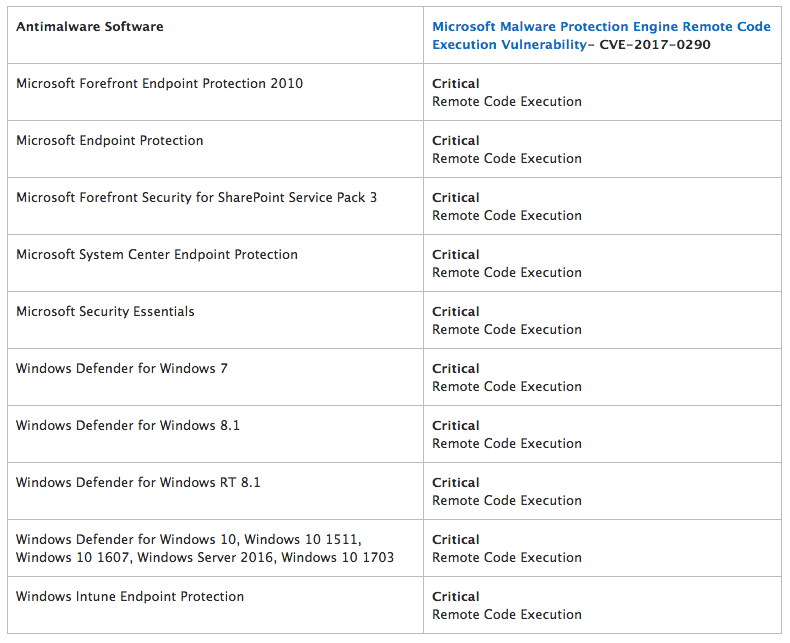
The company also released a full list of the affected applications that you can check out here:
Microsoft says the patch will land on your system automatically over the course of the next two days.
According to the initial security report filed by Google, the exploitable Malware Protection service is “enabled by default” in Windows 8, 8.1, 10, Server 2012 and several more versions of the software.
Silvanovich has also posted a proof of concept exploit script that happens to fit in a single tweet:
CVE-2017-0290 is tweetable :)
var e = new Error();https://t.co/0RDygaVW6B({message : 7 });https://t.co/xkH9SQpNJE
— Natalie Silvanovich (@natashenka) May 9, 2017
Head to the full post on the Microsoft Security TechCenter for more details about the vulnerability.
Better ditch whatever you’re doing and get the fix as soon as you can – waiting for the automatic update sounds pretty risky if you ask me.
Get the TNW newsletter
Get the most important tech news in your inbox each week.