Google on Wednesday announced it has added new measures to protect Chrome users being targeted by malicious extensions. This time, the company is focusing on extensions that are abusing enterprise options or manipulating Chrome preferences; the company says you can expect to see “Safe Browsing” malicious download warnings “within a week.”
We say “this time” because Google has already taken similar measures in the past. Back in December 2012, Google revealed Chrome 25 would disable external extension deployment options on Windows by default and all extensions previously installed using them would be automatically disabled. Google delivered on its promise by releasing the new version of its browser in February 2013.
Having solved that problem, Google is now moving onto the next one. The company explains it has discovered malware that tries to get around silent installation blockers in one of two ways:
- Misuses Chrome’s central management settings intended for configuring instances of Chrome internally within an organization.
- Directly manipulates Chrome preferences in order to silently install and enable bundled extensions.
In the first scenario, the installed extensions are enabled by default and cannot be uninstalled or disabled by the user from within Chrome. In both cases, the user has unknowingly installed malware on his or her computer.
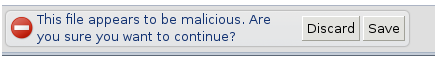
Google wouldn’t detail exactly what “new measures” it has added to safeguard against these two scenarios, but it did say it will identify software that violates Chrome’s standard mechanisms for deploying extensions, flagging such binaries as malware. If you try to download such threats next week, you’ll get a warning that looks like this:
If you develop apps or extensions for Chrome, you’ll want to make sure you’re following the browser’s standard mechanisms for extension installation, whether that’s via the Chrome Web Store, inline, or external. The documentation for all these is here.
Top Image Credit: Miguel Saavedra
Get the TNW newsletter
Get the most important tech news in your inbox each week.