Security is a space that is built upon collaboration—antivirus companies study markets, work with ethical hackers and focus on specific points of network infrastructure to keep both companies and consumers secure.
This methodical process may have worked in the early days of the internet, but innovation in sectors such as IoT and mobile are creating unforeseen gaps, presenting additional targets for bad actors to exploit. Given the interconnected nature of technology in markets that rely on APIs, software-as-a-service (SaaS), and platform-based models, breaches that impact one company will have ripple effects into others. On the consumer side, people often use similar passwords between services.
The threat is growing
Over time, bad actors have become more sophisticated and move faster than leaders in the security market can keep up. According to one study from the Identity Theft Resource Center and data risk management company CyberScout, the number of breaches in the United States alone jumped 29 percent in the first half of 2017. “Record highs” have become the new norm.
A two year joint research effort between the University of California at San Diego, the University of Twente in the Netherlands, and Saarland University in Germany, found that at any given time, a third of the internet experiences a DDoS attack—and this figure is likely an underestimate and poor predictor of future attacks that are growing at an exponential rate.
It’s imperative that the security industry must innovate. And it’s important to remember that this sector is vast and complex. It includes private companies, independent consultants, hobbyist hackers, governments, economists, lawyers, and smart people from all over the world.
All industries recognize the pain point: hackers are decentralized, they operate bots that cooperatively attack from many different directions, with little predictability. But security innovation is often densely concentrated within specific organizations.
One security company, PolySwarm, believes that the future of security should follow this path of decentralization, too. PolySwarm is a team of individuals with an extensive background in security and blockchain. They believe that the Ethereum blockchain has the potential to become a web of “good actors” from a variety of background—a network of the best private and public sector security experts—to crowdsource information for security defense firms.
But what will be the right mechanism to reward information drivers? PolySwarm believes that the answer is in cryptocurrency token, Nectar (NCT).
How NCT, ETH, and fiat currency fit together
Like Bitcoin, Ethereum is a cryptocurrency with its own blockchain, also called Ethereum. Unlike Bitcoin, Ethereum enables the development of applications on its blockchain called “smart contracts.” Smart contracts allow distributed applications (dApps) to use either Ether (ETH) or Ether-based tokens as forms of payment. NCT is convertible to ETH, which is convertible to fiat currency.
Security experts on the Ethereum blockchain can earn NCT by making accurate and timely assertions about suspicious artifacts, like Malware. Tokens are redeemable for ETH cryptocurrency, which can be redeemed for other currencies. For reference, you can see the exchange rate between ETH and USD here.
The expectation is that NCT will enable PolySwarm to deliver a valuable service to the security industry. The company will provide a threat detection funnel in the form of a data stream. Decentralized security experts funnel information to an infosec company, which transmits information to enterprises, which respond more proactively rather than in a reactionary way.
“Most companies don’t think about information security best practices before they build their products,” explains Michelle Tsing, co-founder of a blockchain payments startup and former legal counsel with PayPal’s information security team. “Security is a vertical that applies to all applications built on the blockchain and off blockchain.”
Dissecting the PolySwarm model
Headlines frequently call attention to shortcomings in today’s antivirus and intrusion prevention and detection products. PolySwarm’s presumption is that that today’s threat detection systems do not have well-aligned economic incentives. The relies on hacker-oriented behavioral economics to drive its model, using rewards, through crowdsourcing and collaboration, for malware detection. The idea is to create a data feed that security-focused companies can use. End-consumers and subscribers to malware notifications will benefit from this information source.
But this vision is only attainable if PolySwarm security experts act with integrity.
“People care about being the hero,” says Tsing. “If PolySwarm has a community of white hat hackers who find flaws before the cybercriminals, and the company rewards them accordingly, PolySwarm will be the hero of the cryptocurrency community.”
The idea is that the value of NCT will increase in both loyalty and monetary value as PolySwarm’s value proposition and model yields results to enterprises and consumers
“The biggest threat to NCT would be an insider job,” says Tsing. “It takes one bad apple to harm you. Confidentiality obligations may be breached by a participant. People control is very important in information security. Here, the question is whether there is transparency as to a participant in a decentralized system. Enterprise may have security systems already and may not view PolySwarm as a need.”
PolySwarm has built mechanisms to avoid the potential from bad actors. Here is their team’s response to Tsing’s observation.
“One mechanism is that PolySwarm records threat intelligence data on a publicly viewable blockchain. It is much harder to provide intentionally inaccurate information when everyone can see it,” explains Nick Davis, COO and co-founder at PolySwarm who comes from a background leading enterprise teams in the performance of real-world, large-scale digital forensics, malware reverse engineering, adversarial hunting, threat analysis and incident response. Pre-PolySwarm, he has delivered cutting-edge research using partial homomorphic encryption applied to network signatures. His perspective comes from having audited thousands of lines of code for security vulnerabilities.
“Another mechanism is that the PolySwarm marketplace will have a means to publicly view the reputation of Ambassadors and Security Experts. This will give Ambassadors a means to judge Security Experts, enterprises and end users a means to judge Ambassadors, and Security Experts a means to judge Ambassadors. This is not available in today’s market.”
PolySwarm also points out a 2015 report from Bank America Merrill Lynch, which reports that 70 percent of attacks are currently going undetected. Back then, BofA forecasted that there were 400 threats going undetected per minute. Since then, this figure has likely risen as global connectivity–particularly with IoT and smartphone adoption–has evolved as well.
The security space needs more reliable data feeds, with human beings making judgment calls at the ground level. This data can ultimately help security researchers build, validate, train, and score more sophisticated threat detection algorithms–with neural networks, for example.
NCT incentives lower the barrier to entry in the threat detection landscape, says Miriam Neubauer, managing director at Catena Capital, accelerator and fund for blockchain, cryptocurrency, and token-model based startups.
“More experts mean more resources against cyber attacks and more secure and cheaper software because the hackers are incentivized to fix malware ‘together’ rather than compete in a market driven by fiat currency,” Neubauer says.
You can think of PolySwarm as a network with many micro-engines that align incentives towards a common goal—a centralized ledger and data fee that has the potential to be a real-time source of information for commercial entities that serve both consumers and other businesses in the security threat detection space.
“Polyswarm’s architecture can bring transparency to a space with many unknowns,” says Neubauer. “It does a good job of separating different actors in the network (Ambassadors, Arbiters and Security Experts) as well as defining the different power levels these entities have inside the network.”
It would be naive, however, to expect experts to behave with integrity just because it is the right thing to do.
“We have carefully designed a marketplace where incentives and mechanisms are aligned towards providing accurate and timely threat detection,” explains Davis. The company has created the role of “Arbitrer” in its framework to provide a layer of intelligence.
“It is not impossible to hack or trick the system–every system can be hacked,” says Davis. “But we are confident that this will be significantly difficult to do on our platform. Consider the difference between hacking bitcoin vs. a bank, for instance.”
How to participate in an ICO safely
Before you become excited about the opportunity to invest in any new token or coin, take a step back to understand potential risks. ICOs are uncharted legal terrain. Blockchain and cryptocurrency technology has evolved so quickly that regulators are working to understand how to implement protection measures and incorporate gains from cryptocurrencies into tax laws. China has even considered banning ICOs. Consulting with a lawyer and CPA may be advantageous, depending on your personal circumstances.
“There are a host of crypto coin vulnerabilities that you need to be aware of,” writes Paul Sydlandsky, certified financial planner, for Investopedia “Hackers have gained unauthorized access to digital wallets and cryptocurrency exchanges. As recently as 2016, more than $50 million in ETH was stolen from investors in a fund known as the DAO.”
For a company like Polyswarm, you are making an investment based on the perceived worth of the company’s value proposition ability to achieve the vision it puts forth. One risk that exists is that “companies might not be open to the schemes and reward models PolySwarm proposes,” says Neubauer. “This can be an issue for the model when it goes to market.”
It is important to make a judgment call that aligns with your knowledge base and comfort level.
“Look at the people who are developing the solutions, poke holes in the model, and examine any prototypes and code for yourself,” says Pat Wilbur, CTO of IoT infrastructure company Hologram, which specializes in security as a core competency.
You can browse available source code on Github, here. You can see how NCT will fund operations, here:
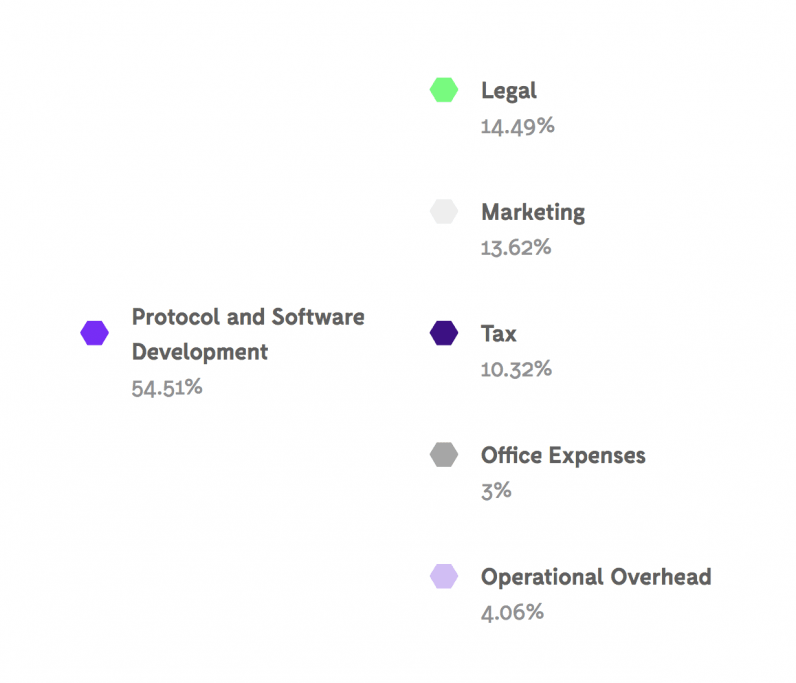
You can learn more about the PolySwarm roadmap, here. You can learn more about the team building PolySwarm here. Former McAfee CIO Mark Tonnessen recently joined the PolySwarm advisory team. The founding team includes technical and economic expertise from individuals who have worked on security initiatives ranging from DARPA-funded programs to corporate clients and hackathons.
ICO Details
PolySwarm will have an ICO, with a token sale period that begins on February 6, 2018, and closes on March 8, 2018. PolySwarm’s minimum funding level is set at the equivalent of $5M in Ethereum (ETH) and a maximum funding level (cap) at $50,000,000 USD in ETH. For those who want to participate in the token sale, according to the website, the minimum participaction threshold is $100. If PolySwarn does not meet its minimum funding level, buyers will receive refunds.
Get the TNW newsletter
Get the most important tech news in your inbox each week.
This post is brought to you by The Cointelegraph and is not an offering of securities or a solicitation to invest in securities. Yes, TNW sells ads. But we sell ads that don’t suck.