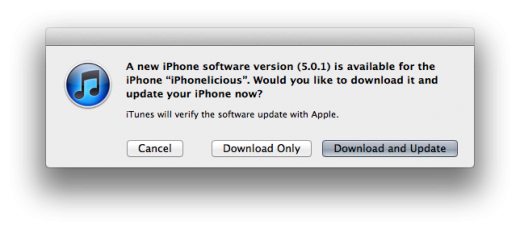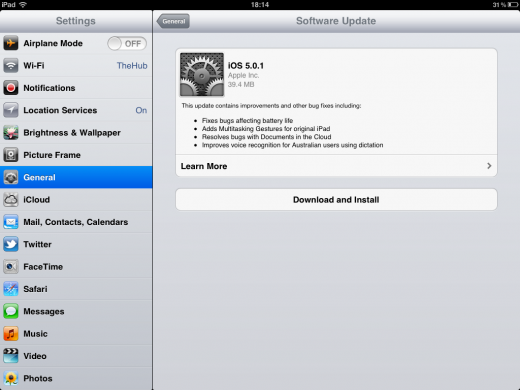
Apple has today released its iOS 5.0.1 update (build 9A405) to address battery issues, add multitouch gestures to the iPad 1 and more. The update is now available in iTunes, and is also available over-the-air to existing iOS 5 users.
Some users may not see the over-the-air update immediately, so either be patient or just use the iTunes update method. We recommend waiting and doing the update OTA because the update experience is much quicker this way, due to the smaller size of the update file (the iPad 2’s update is only 34.9MB OTA), and very slick.
The fixes that are listed are:
- Fixes bugs affecting battery life
- Adds Multitasking Gestures for original iPad
- Resolves bugs with Documents in the Cloud
- Improves voice recognition for Australian users using dictation
Apple has also included an explicit fix for the security issue discovered by security researcher Charlie Miller just a few days ago. In addition, there is a fix for the iPad Smart Cover security glitch, which would allow users access to your last running app.
To get the update now, plug your device into iTunes and click update, or if you’re already on iOS 5, you can go to Settings>General>Software Update to update your device.
Direct download links for the firmware of all devices:
- iPad
- iPad 2 Wifi
- iPad 2 GSM
- iPad 2 CDMA
- iPhone 3GS
- iPhone 4
- iPhone 4 CDMA
- iPhone 4S
- iPod touch 3G
- iPod touch 4G
iOS 5.0.1 Software Update
- CFNetwork
Available for: iOS 3.0 through 5.0 for iPhone 3GS, iPhone 4 and iPhone 4S, iOS 3.1 through 5.0 for iPod touch (3rd generation) and later, iOS 3.2 through 5.0 for iPad, iOS 4.3 through 5.0 for iPad 2
Impact: Visiting a maliciously crafted website may lead to the disclosure of sensitive information
Description: An issue existed in CFNetwork’s handling of maliciously crafted URLs. When accessing a maliciously crafted HTTP or HTTPS URL, CFNetwork could navigate to an incorrect server.
CVE-ID
CVE-2011-3246 : Erling Ellingsen of Facebook
- CoreGraphics
Available for: iOS 3.0 through 5.0 for iPhone 3GS, iPhone 4 and iPhone 4S, iOS 3.1 through 5.0 for iPod touch (3rd generation) and later, iOS 3.2 through 5.0 for iPad, iOS 4.3 through 5.0 for iPad 2
Impact: Viewing a document containing a maliciously crafted font may lead to arbitrary code execution
Description: Multiple memory corruption issues existed in FreeType, the most serious of which may lead to arbitrary code execution when processing a maliciously crafted font.
CVE-ID
CVE-2011-3439 : Apple
- Data Security
Available for: iOS 3.0 through 5.0 for iPhone 3GS, iPhone 4 and iPhone 4S, iOS 3.1 through 5.0 for iPod touch (3rd generation) and later, iOS 3.2 through 5.0 for iPad, iOS 4.3 through 5.0 for iPad 2
Impact: An attacker with a privileged network position may intercept user credentials or other sensitive information
Description: Two certificate authorities in the list of trusted root certificates have independently issued intermediate certificates to DigiCert Malaysia. DigiCert Malaysia has issued certificates with weak keys that it is unable to revoke. An attacker with a privileged network position could intercept user credentials or other sensitive information intended for a site with a certificate issued by DigiCert Malaysia. This issue is addressed by configuring default system trust settings so that DigiCert Malaysia’s certificates are not trusted. We would like to acknowledge Bruce Morton of Entrust, Inc. for reporting this issue.
- Kernel
Available for: iOS 3.0 through 5.0 for iPhone 3GS, iPhone 4 and iPhone 4S, iOS 3.1 through 5.0 for iPod touch (3rd generation) and later, iOS 3.2 through 5.0 for iPad, iOS 4.3 through 5.0 for iPad 2
Impact: An application may execute unsigned code
Description: A logic error existed in the mmap system call’s checking of valid flag combinations. This issue may lead to a bypass of codesigning checks. This issue does not affect devices running iOS prior to version 4.3.
CVE-ID
CVE-2011-3442 : Charlie Miller of Accuvant Labs
- libinfo
Available for: iOS 3.0 through 5.0 for iPhone 3GS, iPhone 4 and iPhone 4S, iOS 3.1 through 5.0 for iPod touch (3rd generation) and later, iOS 3.2 through 5.0 for iPad, iOS 4.3 through 5.0 for iPad 2
Impact: Visiting a maliciously crafted website may lead to the disclosure of sensitive information
Description: An issue existed in libinfo’s handling of DNS name lookups. When resolving a maliciously crafted hostname, libinfo could return an incorrect result.
CVE-ID
CVE-2011-3441 : Erling Ellingsen of Facebook, Per Johansson of Blocket AB
- Passcode Lock
Available for: iOS 4.3 through 5.0 for iPad 2
Impact: A person with physical access to a locked iPad 2 may be able to access some of the user’s data
Description: When a Smart Cover is opened while iPad 2 is confirming power off in the locked state, the iPad does not request a passcode. This allows some access to the iPad, but data protected by Data Protection is inaccessible and apps cannot be launched.
CVE-ID
CVE-2011-3440
Get the TNW newsletter
Get the most important tech news in your inbox each week.