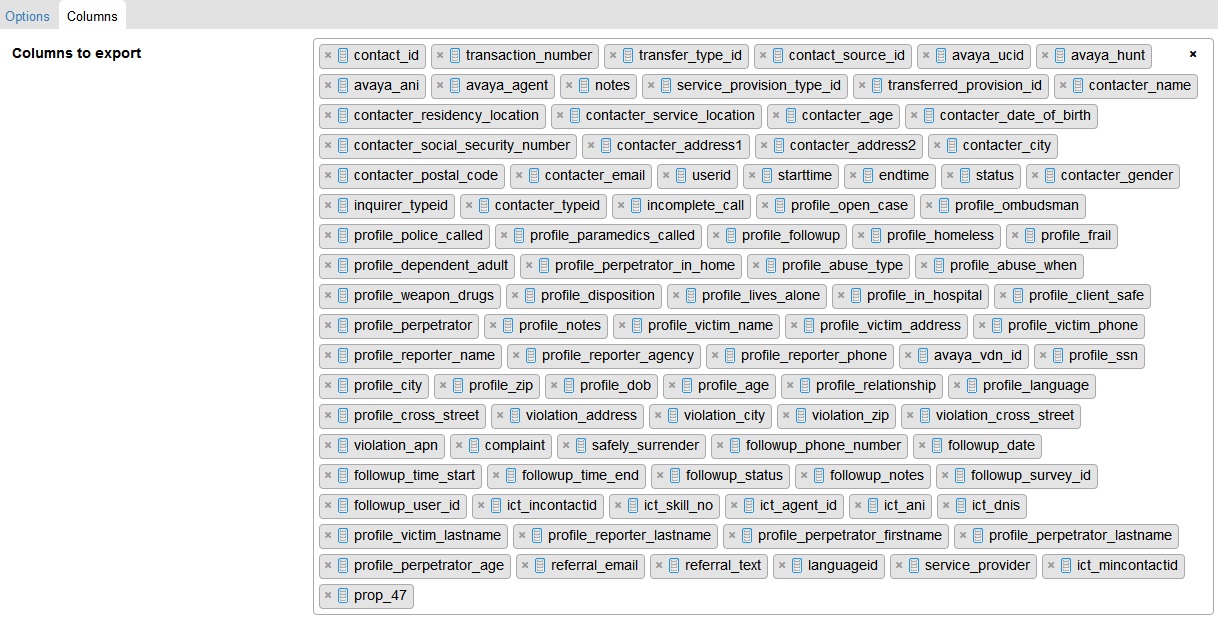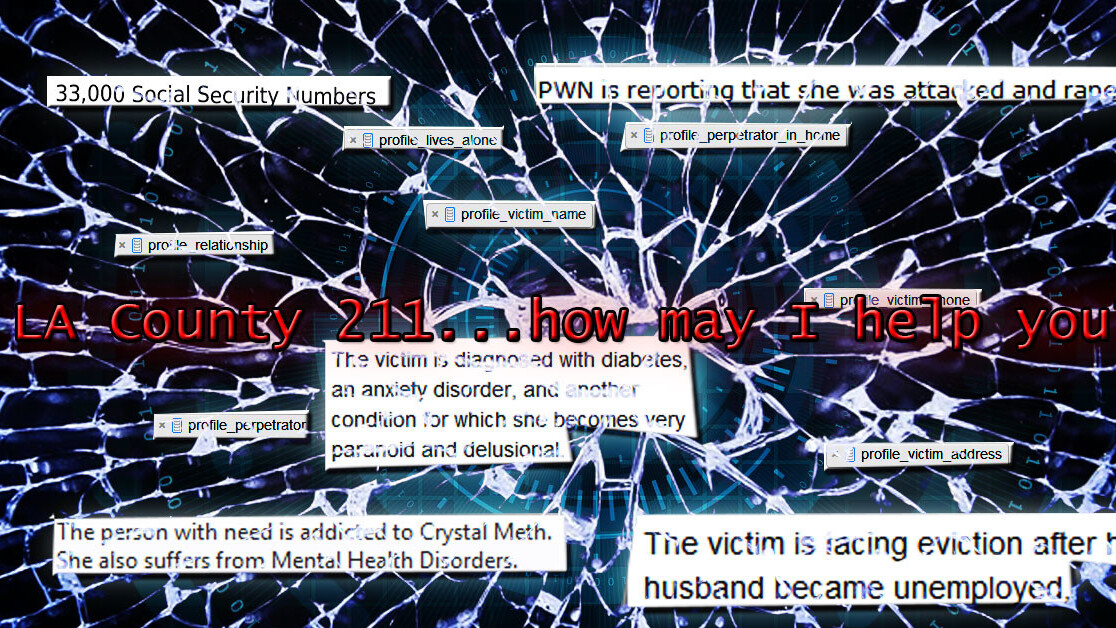
A mistake on the part of whoever is in charge of the LA County 2-1-1 System’s database exposed 3.2 million files containing terrifyingly sensitive data – much of which includes personally identifying information from calls with abuse and crisis victims. This is bad.
An Amazon Web Services (AWS) S3 bucket (basically, cloud storage) containing detailed information from more than 200,000 calls to the county’s 2-1-1 line, a hotline that provides assistance for abuse victims and persons in crisis (among other health and human services-related functions), was left configured for public access — for an unknown period of time — until a private security researcher noticed.
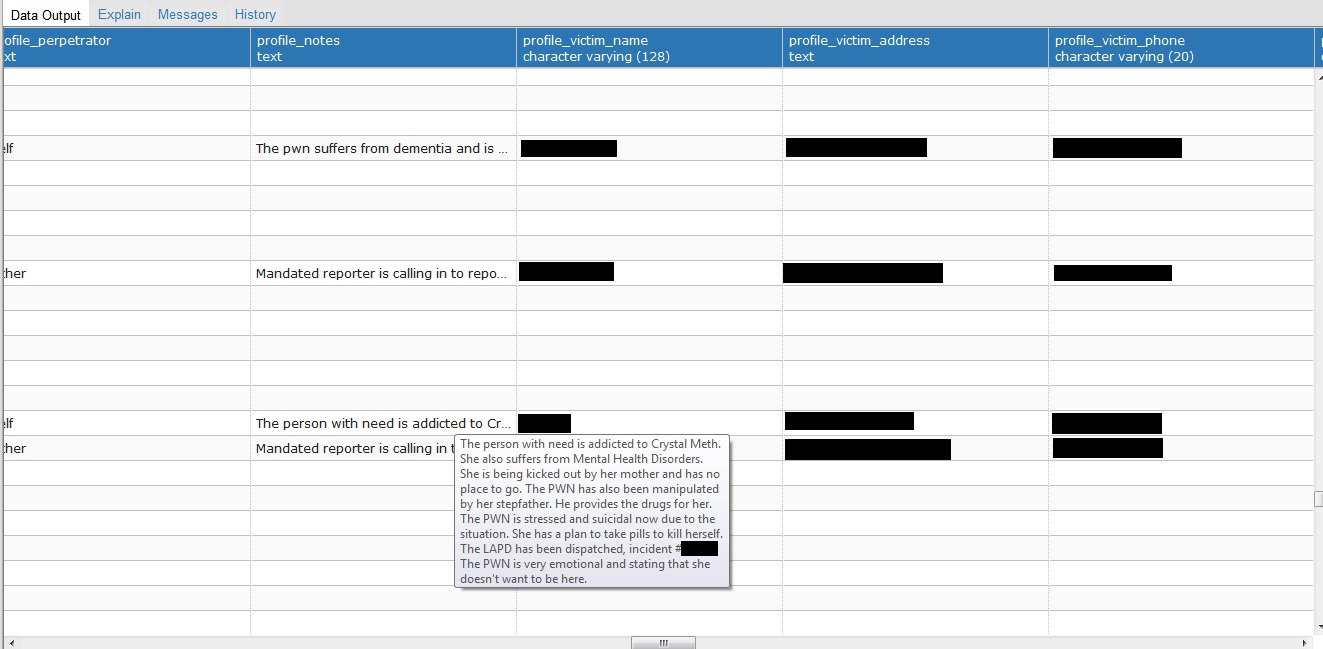
The leak exposed more than 33,000 social security numbers, over 300,000 email addresses, and the full names of the victims, alleged perpetrators, and witnesses in numerous suspected cases of physical and sexual abuse.
If that weren’t enough, the S3 bucket held “weakly hashed” passwords for 384 logins. Whatever information a bad actor couldn’t gain from the contents of the bucket could have feasibly been accessed by logging into the LA County 2-1-1 LinQ system using these credentials.
In the time since the incident was reported earlier this week, the bucket has reportedly been secured. But just like every other breach of this nature, by the time the problem is discovered there’s simply no way of knowing if any real damage has been done.
When you’re dealing with detailed information accusing potentially violent people of things such as child abuse and rape, any breach of security risks the lives of people who, often, are the most vulnerable among us. This kind of breach – essentially an IT person forgets to secure the bucket after doing something that requires it be set to public temporarily – is 100 percent preventable.
Like we’ve said before: bad employees are worse than good hackers.
Chris Vickery, a Cyber Risk Analyst for cyber resilience firm UpGuard, found the vulnerability by searching for publicly accessible AWS buckets which contained files or folders with the word “county” in them. As is the case with all of the vulnerabilities he exposes, all he needed to access the information was a regular old internet browser.
If a “hacker” can use IE, Chrome, Firefox, Opera, or Safari they’ve got all the tools they need to “hack” these AWS buckets. What’s worse: Amazon has taken steps to mitigate this type of problem, yet it still persists.
We talked to Vickery about the problem, one he makes a living sniffing out. He believes it’s just human nature:
You gotta make it so people can’t screw up. Because if people can screw up, a certain percentage of them will. That’s simple statistics.
Vickery knows what he’s talking about. He’s found similar breaches in the NSA and Department of Defense databases (both caused by the same kind of AWS S3 bucket misconfiguration). He says we’re still in the “triage phase” when it comes to these kinds of breaches — meaning they’ll keep happening until someone finds a way to make it impossible for administrators to accidentally not do the one thing they need to do to make sure an AWS bucket isn’t publicly accessible: make it inaccessible to the public. Basically the best we can hope for is good guys like him finding the breaches before bad actors do. And that’s terrifying.

Everyone makes mistakes, but not every mistake could lead to exposing tens of thousands of victims, their families, and witnesses to unthinkable consequences. The government – at every level – continues to show it has little ability to protect our data.
For its part, LA County is investigating and performing a security audit – further evidence the state of cyber security preparedness in this country is best described as “reactionary.”
The Next Web’s 2018 conference is just a few days away, and it’ll be ??. Find out all about our tracks here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.