
 A new plugin from SecTheory and WordPress guru Joost De Valk is giving WordPress blog owners the opportunity to detect user accounts that share the same credentials as those recently compromised in the Gawker website hack.
A new plugin from SecTheory and WordPress guru Joost De Valk is giving WordPress blog owners the opportunity to detect user accounts that share the same credentials as those recently compromised in the Gawker website hack.
One of the more undesirable outcomes of the Gawker data breach was the fact that the attackers published over one million user records, allowing anyone with a torrent client to grab a copy and find a list of usernames and passwords. Armed with user credentials, the sites that share those users become the next potential targets. Whether it be your email address or your Twitter account, it is possible further damage can be done.
Accepting its duty to help protect its users, SecTheory took the Gawker hacker list, parsed the results and then sought about developing an API that would allow users to find out if their accounts were compromised. WordPress plugin developer Joost De Valk took this API and extended its use by incorporating it into a WordPress plugin called Shared User Checker.
With Shared User Checker, WordPress admins are now able to detect which users have been compromised, making their own sites more secure but also giving the option to alert the users that they may have had their details stolen in the Gawker attacks.
As SecTheory’s Robert Hansen says
These users did nothing wrong, and shouldn’t be punished, but because they often use the same passwords it is important that they be alerted to the very real threat.
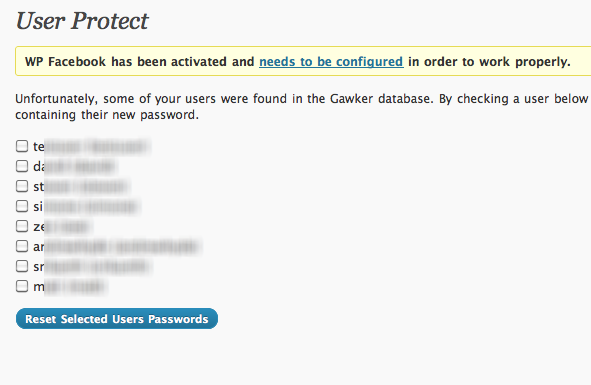
WordPress blog owners simply need to download the plugin file, upload and activate. Once there, enter the WordPress Settings panel inside your blog and there will be a new option called “User Protect”.
Run the tool and find out who has been compromised. You will then be able to amend records or contact the affected users.
The plugin can be modified to accept other compromised lists in future, it might be a good idea to keep this one enabled as you never know when you might need it.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





