Earlier today, word began getting around that there was a new way to bypass the iOS 6.1 lock screen and that this one was even worse, allowing full access to the user portion of the file system. Well, that’s not exactly true, as we’ve uncovered with some simple tests.
The lock screen bug does in fact exist, and it works as advertised, bypassing the lock and bringing you to a blank black screen with just the status bar. But it allows you no access to anything, not pictures, not contacts and certainly not the file system.
Security researchers submitted a note to the Full Disclosure blog when they discovered the bug, but unfortunately their testing methods were flawed.
How do I know this? Because early last year, while investigating the security issues in the way that the Facebook (and Dropbox) apps were handling user tokens, TNW discovered that the user file system is in fact encrypted and un-viewable on a computer when an iPhone had a passcode enabled.
This ‘bug’ does not change that behavior. Though it appears as if the lock has been fully ‘bypassed’, it does not change the fact that the file system is still encrypted and unreachable.
Once an iPhone has been connected to a computer and unlocked once, its file system is always viewable by that machine, regardless of passcode status. Don’t shoot the messenger if you don’t like this behavior, that’s just the way it is. But, what it means is that this bypass method could only show the file system if it had previously been plugged into that computer while unlocked.
If the researchers had bothered to plug it into a machine that had never been connected to that device before, then they would have been unable to access the file system. They would have been presented with an error message by iTunes and by any file explorer utility.
In fact, the flaw in their methodology is exposed in the very first line of their instructions, where they say to connect it to iTunes.
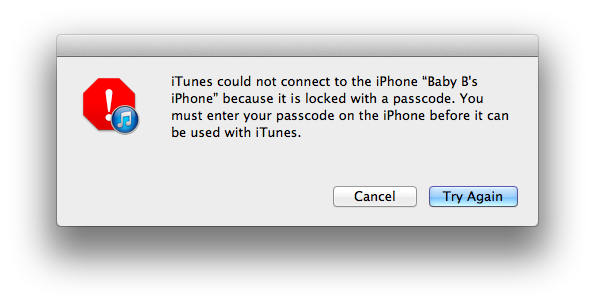
To demonstrate, here is an iPhone with a passcode enabled and the bypass trick done on it connected to a new computer for the first time. No dice on reading it, you can see the iTunes error message there:
Here’s a closer look at the message:
And here’s what happens when you unlock it, allow the computer to register the device and then ‘lock’ it again. Voila, access (you can see the iTunes restore dialog):
In short, in order to gain access to your iPhone’s file system, someone would need your computer and your phone. And if they’ve got both of those, you have bigger problems than someone getting access to your saved games.
All that aside, there is still two ways to bypass a passcode now in the clear, and that shouldn’t be. Apple needs to fix them and has already begun testing fixes for the next version of iOS 6.
Get the TNW newsletter
Get the most important tech news in your inbox each week.